Bitlocker: Network Unlock
Hello everyone. It’s Rafal Sosnowski from Microsoft Dubai Security PFE Team. Recently I have been requested by my customers to explain Bitlocker Network Unlock. So here you go.
Network Unlock is a relatively new Bitlocker protector (added in Windows 8) that can be used to unlock computers after the reboot without need of entering Bitlocker PIN.
This is very helpful in scenarios where all workstations protected by Bitlocker with TPM+PIN need to be restarted due to monthly maintenance or after power outage. Another scenario is when you don’t want to bother your users in corporate network with PIN prompt but require it when user takes laptop home.
For Network Unlock to work you need to meet some prerequisites mentioned below including having DHCP Server, WDS Server, UEFI capable clients and special certificate deployed by the GPO. Network unlock uses MS-NKPU protocol encapsulated into DHCP packets.
How Network Unlock Works:
The whole process of unlocking the Operating System drive encrypted by Bitlocker with network unlock feature is split into three phases:
Phase 1:
In first phase client that is configured to use network unlock has to obtain valid IP address from the DHCP server. This DHCP request is sent from UEFI firmware not from DHCP client service in the Operating System. We also assume that proper GPO is configured on the client which enables Network Unlock and delivers special certificate used to encrypt message sent in next phase.

Phase 2:
In this phase clients will broadcast MS-NKPU request which is encapsulated into DHCP INFORM packet and is containing Bitlocker key material encrypted with the WDS certificate public key from the GPO. Also this packet will contain 256-bit session key used later to protect the data exchange.
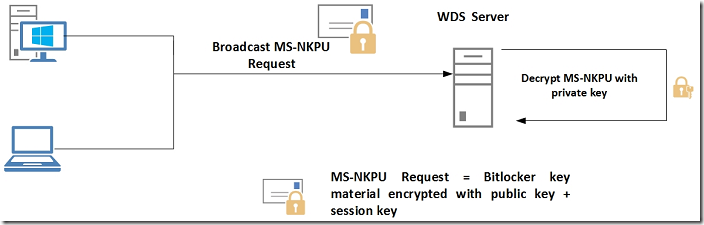
Phase 3:
When Network Unlock server receives the MS-NKPU Request, it will decrypt it with corresponding private key of WDS certificate and send back the Bitlocker Key material encrypted with the session key. Because client generated this session key in previous step, it will decrypt the Bitlocker key material easily. Client now will be able to unlock its drive and allow user to log on to the system.

Prerequisites:
DHCP Server
DHCP server provides IP address to the clients in the pre-OS boot environment. DHCP Server is required when you are using IPv4 and is optional if you are using Ipv6 due to auto configuration with link-local Ipv6 address. Network Unlock on the client uses its linked local address to create DHCPv6 request packet, so it works without configuring a DHCPv6 server. You can configure both DHCPv4 and DHCPv6 scopes on the same machine or on different machines/devices. If you have DHCP and client computers in different subnets you will have to configure DHCP Relay agent on your router.
WDS Server
WDS server as a separate server role or part of the SCCM and is required to provide PXE functionality (Pre-boot Execution Environment). PXE is mainly used to install or boot operating system from the network but in this case it will answer all NKPU requests arriving to the server. Indeed, WDS server is a hosts for special Network Unlock provider which answers these requests.
NKP Provider is added to the server during Network Unlock feature installation and is loaded to memory when WDS service starts. Corresponding event will be also logged in the: Applications and Services Logs\Microsoft\Windows\Deployment-Services-Diagnostics\Debug
Event ID: 24577
[WDSServer/WDSPXE] NKPPROV Provider initialized successfully.
Note: this log is disabled by default. You need to explicitly enable it in the Eventvwr.msc
Also you can verify if provider has been registered successfully under:
HKLM\System\CurrentControlSet\Services\WDSServer\Providers\WDSPXE\Providers\

It is also possible to configure list of IPv4 or IPv6 subnets on WDS server, in classless inter-domain routing (CIDR) notation, from which clients are permitted to be unlocked.
Network Unlock Feature
On the WDS server you need to install Bitlocker Network Unlock feature using Server Manager or command line:
Install-WindowsFeature BitLocker-NetworkUnlock
This process will register small DLL (nkpprov.dll) as a separate PXE provider plugged into the WDS server. This provider listens to all DHCPv6/v4 broadcast packages on the network, and will only respond if the package is for Network Unlock. It will not respond to normal DHCP/PXE packets.
Clients
Clients have to be Windows 8 or above with support for UEFI spec 2.3.1. Clients also have to have TPM enabled, activated and with ownership taken by the system. NKPU protocol (which is used by Bitlocker Network Unlock) can work with both wired and wireless networks [ link ], however there are not many platforms supporting PXE/DHCP over Wireless in pre boot environment. As per protocol specification:
The security of this protocol assumes that only a physical local area network (LAN) connection is available when executing this protocol, and that physical connectivity to the LAN is an implicit built-in authentication factor. Note that wireless networks do not offer this security. However, WiFi usage with the NKPU Protocol is acceptable if the user is required to authenticate to the access point when establishing a connection to the NKPU server.
From Bitlocker perspective, so far Microsoft doesn't support Network Unlock over WiFi. There are few reasons for that:
- Wi-Fi signals can be spoofed and the process of provisioning server certificates to clients (laptops) and enabling such network unlock can be vulnerable to man-in-the-middle attack, where attacker can then collect all hard drives keys that unlock all laptop drives and later get access to any stolen/lost laptop from that enterprise.
- Increasing retry logic in the pre-boot process quickly gets into very limited high quality entropy (RNG) we have available to use for session keys to protect unlock traffic against replay attacks. If retries are increased we can expose network unlock to replay attacks.
- Wi-Fi signals can easily spread outside of the physical building boundary and an attacker who stole or found lost laptop can walk to the building (without entering) and unlock it nearby, just by powering it on.
So again, according to Microsoft official protocol specification, NKPU can work over WiFi, however it is very challenging to secure such communication. For example I've never seen an 802.1x authentication implemented in UEFI WiFi network stack . Also, since it is almost impossible to limit boundary of the WiFi, even if we have Access Point authentication implemented, it would be impossible to defend against attacker unlocking stolen laptop just right to premises' fences. So, it might work but it's not supported
Client doesn’t have to have TPM+PIN nor TPM protector configured on the OS drive although it is best practice to use TPM+PIN protector. Network unlock protector is in fact combination of 2 protectors: TPM + certificate as shown in the picture below:
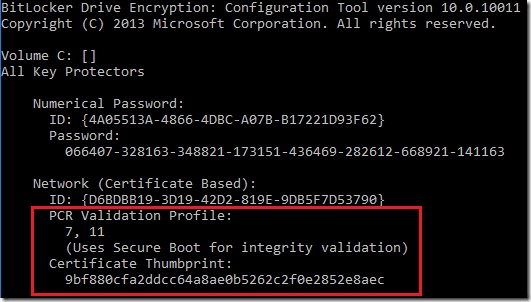
So yes it is possible to use Network Unlock protector without having TPM+PIN added to the OS drive, however in normal circumstances it is recommended to have it.
Certificate
Special certificate with OID 1.3.6.1.4.1.311.67.1.1 (Bitlocker Drive Encryption OID) has to be obtained from the Certification Authority Server* and imported into FVENKP computer store on the WDS server:
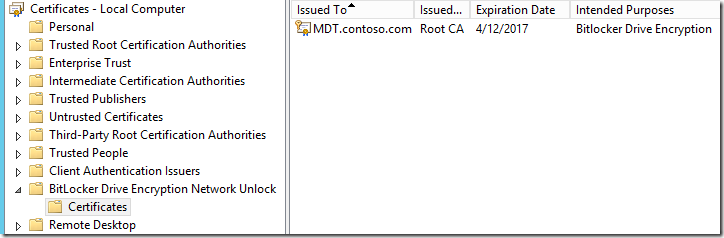
This certificate is used to encrypt Bitlocker Key Material sent by client to the WDS server. Only WDS server can decrypt it with its private key and send back to the client.
You can verify if certificate is present using certlm.msc or command line:
Certutil -verifystore FVENKP
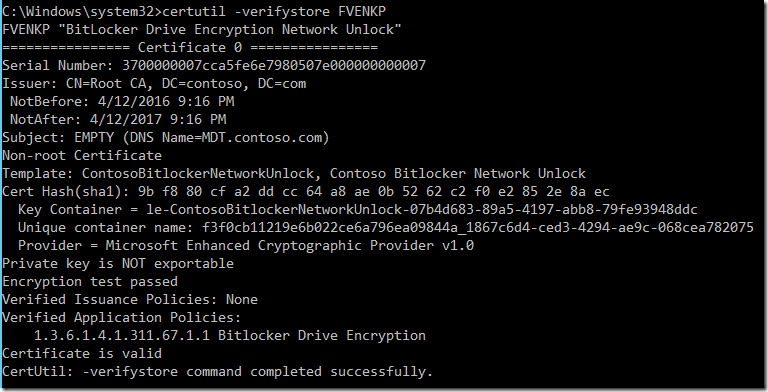
*Self-signed certificates are also supported.
GPO Configuration
Above WDS certificate (public key) has to be deployed to all computers that will be using network unlock feature. Simplest way is to use GPO
Computer Configuration\Policies\Windows Settings\Security Settings\Public Key Policies\Bitlocker Drive Encryption Network Unlock Certificate:
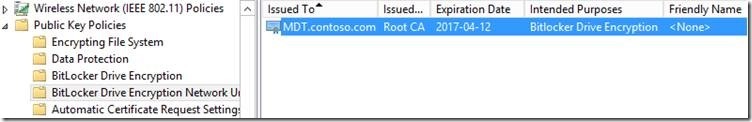
or registry: HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\FVE_NKP
Also policy “Allow network unlock at startup” has to be configured on all client computers via GPO:
Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives
Network Trace:
If we take a look at the network trace, we see that after obtaining IP address from the DHCP server 10.0.0.10 (DORA process) client 10.0.0.150 sends DHCP Inform packet with Vendor Class ID: Bitlocker. This is a request to Network Unlock Server containing session key, certificate thumbprint and Bitlocker key material encrypted with certificate public key deployed earlier by the GPO.
Bitlocker key materials is concatenated from Option 43 (0x2B) and Option 125 (0x7D) of that packet.
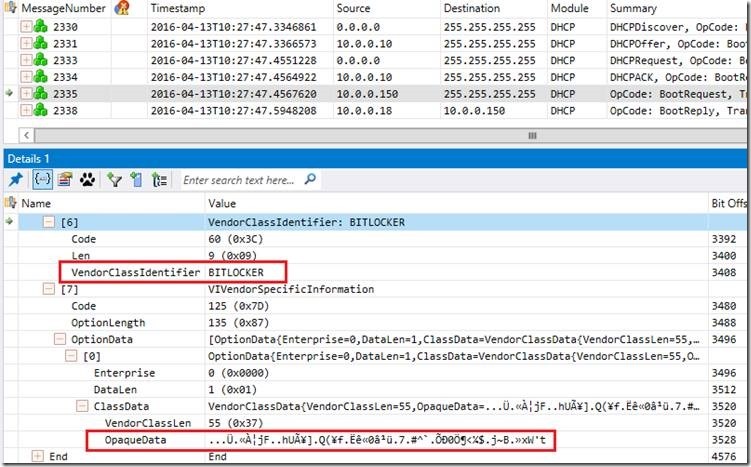
In the response server will send us Bitlocker Key which was decrypted by Network Unlock server private key. To protect this material server will encrypt it with the session key. This is encapsulated into DHCP reply with Opcode: BootReply:
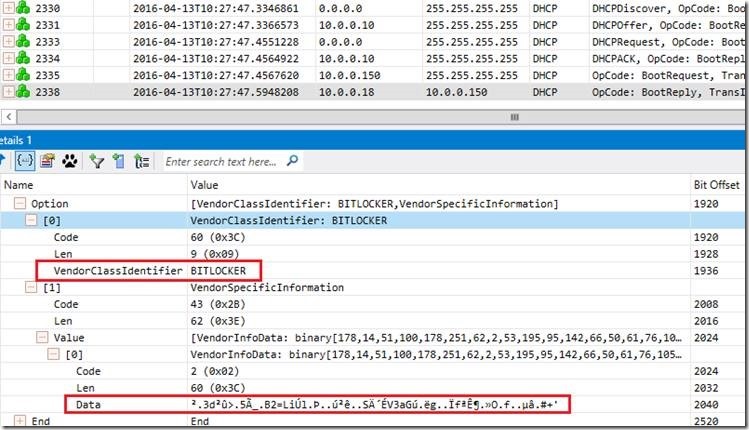
After obtaining Bitlocker Key Material from the Network unlock server, client will use session key to decrypt it and unlock the volume.
Additional notes:
DHCP v6 can be disabled in some of the UEFI implementations from the UI. If you want to make sure that Network unlock happens only via IPv4 you need to disable IPv6 on the network card of WDS server. Bootmgr code on the client will first try to unlock via DHCPv6 and failover to DHCPv4.
Network Unlock still uses TPM to check integrity of the platform. So if the values in the PCRs (Platform Configuration Registers) have changed due to, for instance: BIOS upgrade, replacement of motherboard, malware in the boot components etc. you will be still prompted for Bitlocker Recovery Password. Entering this password cannot be automated in any way.
Comments
- Anonymous
May 11, 2016
Hi RafalThank youfor this article. It helped me to understand better Bitlocker Network Unlock.While reading your article, I found 2 mistakes:Prerequisites - WDS Server:HKLM\System\CurrentControlSet\Services\WDSServer\Providers\WDSPXP\Providers\WDSPXP --> instead of WSDPXENetwork Unlock Feature - Certificate:Command: Certutil -verifystore PVENKP --> instead of FVENKPBest regards,Flavio- Anonymous
May 11, 2016
Thank you Flavio. Corrected the typos! Have a good day.
- Anonymous
- Anonymous
June 02, 2016
Hi, are there any DCHP options that would need to be configured.. to let the clients know that they need to contact the WDS server or which WDS or is this solely handled by the UEFI client?- Anonymous
June 03, 2016
first MS-NKPU packet is broadcasted so there is no pointer to specific WDS server. That means all the machines will get the request (within one broadcast domain) and only WDS server with network provider will reply to the client using unicast. Because it is a broadcast, if you have your WDS server in another subnet you probably would need to have DHCP proxy/relay configured.- Anonymous
June 27, 2016
Thanks Rafal for your response.. are you talking about just configuring DHCP authorisation on your WDS server or actually configuring an additional helper address (My WDS server is not a DHCP server) and yes, the client is on a different VLAN.
- Anonymous
- Anonymous
- Anonymous
July 27, 2016
Can network unlock work without DHCP? - Anonymous
October 16, 2016
Yes if you use ipv6. - Anonymous
November 21, 2016
What are the redundancy options if the WDS server does down for a local site ? Would a second WDS server setup with a different cert be able to reply to requests ? - Anonymous
January 10, 2017
You can use multiple WDS servers with the same certificate and private key. there has to be someone that needs to answer that broadcast with the proper NKPU payload. - Anonymous
January 11, 2017
Hi Rafalwhere is the unlock key stored? On the WDS Server, Active Directory, ...?Do we have to enable Network unlock on the Client or is this done because of the “Allow network unlock at startup” Group policy Setting?Best regardsThomas - Anonymous
January 24, 2017
Public key of the certificate is delivered to the client via GPO. Private part is stored on WDS server and should be protected at all cost. Windows 8 clients and above support Network Unlock but you need to enable it in the GPO as mentioned in the article. - Anonymous
March 10, 2017
Did someone get Network unlock feature + MBAM working together ?It seems that GPO settings from MDOP-MBAM admin templates (where there is no "Network Unlock" Features) cancel settings from Bitlocker admin templates . Or maybe define them in 2 differents GPO's ? thx for any infos - Anonymous
March 13, 2017
My client machine is HP 440 G3 with window 10 installed, It currently boots in OS through BIOS.If i enable Bitlocker network unlock, will this client machine work or do i have to disable bios>enable UEFI and install OS again? - Anonymous
March 14, 2017
Hi, Can you give any instructions how to obtain the certificate? I have CA installed in my test environment but I just can't figure out how to get the certificate and how to assign it. I can't find any instructions from internet regarding bitlocker network unlock. Also, I'm not sure if the Bitlocker DRA instructions are valid for this (couldn't find anything else).Thank you. - Anonymous
May 09, 2017
@ Tushar You can convert MBR to GPT partition with Windows 10 1703 using a tool called MBR2GPT.exe without data loss. That will let you to switch to UEFI environment. In pre Windows 10 1703 you need to reinstall OS based on UEFI. There are also 3rd party tools to convert MBR to GPT but I cannot recommend any. - Anonymous
May 09, 2017
The comment has been removed - Anonymous
July 07, 2017
Is there a way to run WDS and the DHCP roles on the same server for Network unlock? - Anonymous
February 19, 2019
Rafal, what is the correct store name? FVENKP or FVE_NKP? Or FVE_NKP on the WDS server and FVENKP on the clients? Or vice-a-versa? - Anonymous
May 10, 2019
Hi Rafal,After implementing Bitlocker Network Unlock in my customers test lab we came up with following open questions:a) Is there a documented procedure available how to renew the used certificate - or is just the keypair used and it will logically never expire?b) How often does WDS access the private key of the cert? Is is supported to protect the key with a network based HSM solution (would be useful only if the key is access only during WDS startup) or would this impact performance and availability of the service because the key is accessed per request?Best Regard,Franz