Investigate and remediate communication compliance alerts
Important
Microsoft Purview Communication Compliance provides the tools to help organizations detect regulatory compliance (for example, SEC or FINRA) and business conduct violations such as sensitive or confidential information, harassing or threatening language, and sharing of adult content. Communication Compliance is built with privacy by design. Usernames are pseudonymized by default, role-based access controls are built in, investigators are opted in by an admin, and audit logs are in place to help ensure user-level privacy.
After you've configured your communication compliance policies, you'll begin receiving alerts for message issues that match your policy conditions. To view and act on alerts, users must be assigned to the following permissions:
- The Communication Compliance Analysts or the Communication Compliance Investigators role group
- Reviewer in the policy that is associated with the alert
After you establish required permissions, use the following working instructions to investigate and remediate issues.
Tip
Get started with Microsoft Security Copilot to explore new ways to work smarter and faster using the power of AI. Learn more about Microsoft Security Copilot in Microsoft Purview.
Investigate policy matches and alerts
The first step in investigating issues detected by your policies is to review policy matches and alerts. There are several areas in the communication compliance area to help you quickly investigate policy matches and alerts:
Policies page: When you sign into the Microsoft Purview portal or the Microsoft Purview compliance portal using credentials for an admin account in your Microsoft 365 organization, select the Communication Compliance solution, and then select the Policies page. This page displays communication compliance policies configured for your Microsoft 365 organization and links to recommended policy templates.
Note
If your role group is scoped by one or more admin units, you'll see a message at the top of the page to let you know that you can only view and manage the policies that you're scoped for. To learn more about what you can access, select View role groups in the banner.
Each policy listed includes the following columns:
Messages scanned today: The aggregate number of messages that the policy has scanned on the current day for users and locations that are in scope of the policy. If there's a policy match, the item is added to the New pending today column. The number refreshes automatically once per hour — it doesn't update if you refresh the page. At the end of the UTC day, the count resets to zero.
Tip
If the value in the column is 0 or a very low number, it may be because the policy is too strict. For example, the policy might be focused on just one user or on just one location that the in-scope user doesn't use. You might see a wide variety of aggregate numbers in this column if your policies have different focuses. For example, one policy might be focused on an entire department of users sending messages from multiple locations while another policy might be focused on just one user or just one location.
New pending today: Shows the number of policy matches for the current day. This value updates whenever you open the page. You can also select the Refresh button to get the latest count. At the end of the UTC day, the count resets to zero.
Total pending: The count of policy matches that need review. This value updates whenever you open the page. You can select the Refresh button to get the latest count. After refreshing, this number will match the number on the Pending tab.
Total resolved: The total number of resolved policy matches. This value updates whenever you open the page. You can select the Refresh button to get the latest count. After refreshing, this number will match the number on the Resolved tab.
Status: The status of the policy (Active or Deactivated).
Last modified: The date and Coordinated Universal Time (UTC) of the last policy modification.
Last policy scan: The UTC date for the last policy scan.
To start remediation actions, select the policy associated with the alert to launch the Policy details page. From the Policy details page, you can review a summary of the activities, review and act on policy matches on the Pending tab, summarize a lengthy message by using Microsoft Copilot in Microsoft Purview, or review the history of closed policy matches on the Resolved tab. Learn more about remediation actions.
Alerts page: Go to Communication compliance > Alerts to display the last 30 days of alerts grouped by policy matches. This view allows you to quickly see which communication compliance policies are generating the most alerts ordered by severity. An alert isn't the same thing as a policy match. An alert generally consists of multiple policy matches, not just one policy match. After the required number of policy matches is met for a particular alert, the alert is created and email is sent to the alert recipient.
Reports page: Go to Communication compliance > Reports to display communication compliance report widgets. Each widget provides an overview of communication compliance activities and statuses, including access to deeper insights about policy matches and remediation actions.
Tips for quickly reviewing policy matches on the Pending or Resolved tab
When you select a message to review on the Pending tab or the Resolved tab, the condition that caused the policy match is displayed in an alert message bar (yellow banner) at the top of the Source tab. This is a quick way to determine the condition or conditions that caused the policy match. If there are multiple conditions, select View all in the banner to see all the conditions that caused the policy match. At this time, only trainable classifiers and sensitive information types are highlighted as conditions in the yellow banner.
Sometimes it's useful to quickly review policy settings without opening a policy. For example, if you're testing multiple policies with different conditions, you might want to save time by reviewing conditions for each policy to determine risk before opening the policy. You can do this by selecting Policy settings, which opens a panel where you can view the policy settings. If you're a member of the Communication Compliance or Communication Compliance Admins role group, you can view and change settings from the panel. If you're a member of the Communication Compliance Investigators or Communication Compliance Analysts role group, you can view settings but you can't change them.
Using filters
The next step is to sort the messages so it's easier for you to investigate. From the Policy details page, communication compliance supports multi-level filtering for several message fields to help you quickly investigate and review messages with policy matches. Filtering is available for pending and resolved items for each configured policy. You can configure filter queries for a policy or configure and save custom and default filter queries for use in each specific policy. After configuring fields for a filter, you'll see the filter fields displayed on the top of the message queue that you can configure for specific filter values.
Key filters (the Body/Subject, Date, Sender, and Tags filters) are always displayed on the Pending and Resolved tabs to make it easy to access those filters.
For the Date filter, the date and time for events are listed in Coordinated Universal Time (UTC). When filtering messages for views, the requesting user's local date/time determines the results based on the conversion of the user's local date/time to UTC. For example, if a user in U.S. Pacific Daylight Time (PDT) filters a report from 8/30/2021 to 8/31/2021 at 00:00, the report includes messages from 8/30/2021 07:00 UTC to 8/31/2021 07:00 UTC. If the same user was in U.S. Eastern Daylight Time (EDT) when filtering at 00:00, the report includes messages from 8/30/2021 04:00 UTC to 8/31/2021 04:00 UTC.
Filter details
Communication compliance filters allow you to filter and sort messages for quicker investigation and remediation actions. Filtering is available on the Pending and Resolved tabs for each policy. To save a filter or filter set as a saved filter query, one or more values must be configured as filter selections.
The following table outlines filter details:
| Filter | Details |
|---|---|
| Body/Subject | The message body or subject. You can use this filter to search for keywords or a keyword phrase in the body or subject of the message. The subject appears in the Subject column for email messages. For Teams messages, nothing appears in the Subject column. |
| Date | The date the message was sent or received by a user in your organization. To filter for a single day, select a date range that starts with the day you want results for and end with the following day. For example, if you wanted to filter results for 9/20/2020, you would choose a filter date range of 9/20/2020-9/21/2020. |
| File class | The class of the message based on the message type, either message or attachment. |
| Has attachment | The attachment presence in the message. |
| Item class | The source of the message based on the message type, email, Microsoft Teams chat, Bloomberg, etc. For more information, see Item Types and Message Classes. |
| Recipient domains | The domain to which the message was sent; this is typically your Microsoft 365 subscription domain by default. |
| Recipient | The user to which the message was sent. Note: The Recipient field includes recipients in the To and CC fields. BCC fields are not supported. |
| Sender | The person who sent the message. |
| Sender domain | The domain that sent the message. |
| Size | The size of the message in KB. |
| Tags | The tags assigned to a message, either Questionable, Compliant, or Noncompliant. |
| Language | The detected language of text in the message. The message is classified according to the language of most the message text. For example, for a message containing both German and Italian text, but most text is German, the message is classified as German (DE). For a list of supported languages, see Learn about trainable classifiers. You can also filter by more than one language. For example, to filter messages classified as German and Italian, enter 'DE,IT' (the two-digit language codes) in the Language filter search box. To view the detected language classification for a message, select a message, select View message details, and scroll to the EmailDetectedLanguage field. |
| Escalated To | The user name of the person included as part of a message escalation action. |
| Classifiers | The name of built-in and custom classifiers that apply to the message. Some examples include Targeted Harassment, Profanity, Threat, and more. |
Configure a filter
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Communication Compliance solution.
- Select Policies in the left navigation, and then select a policy to see policy matches (if any) for that policy.
- On the Policy page, select either the Pending or Resolved tab to display the items for filtering.
- Select Filters.
- Select one or more filter checkboxes, and then select Apply.
- To save the selected filters as a filter query, select Save the query after you've configured at least one filter value. Enter a name for the filter query, and then select Save. This filter is available to use for only this policy and is listed in the Saved filter queries section of the Filters page.
Review and remediate policy matches and alerts
No matter where you start to review policy matches or alerts or the filtering you configure, the next step is to take remediation action. Start your remediation using the following workflow on the Policy or Alerts pages.
Note
If you see a policy prefaced with "DSPM for AI" (or "AI hub" from the preview name), the policy was created in Data Security Posture Management for AI, not in communication compliance. To learn more about this solution, see Data Security Posture Management for AI provides insights, policies, and controls for AI apps.
Examine the message basics
Sometimes it's obvious from the source or subject that a message can be immediately remediated. It may be that the message is spurious or incorrectly matched to a policy and it should be resolved as misclassified. To mark a message as misclassified, select Resolve and Item was misclassified to leave a note in the item's history that it is misclassified and remove it from the Pending queue. To share misclassified content with Microsoft, select Send message content, attachments, and subject to remove it from the Pending queue and report the items to Microsoft.
Note
Misclassified options in the Resolve pane won't appear if the condition that caused the policy match is not based on a trainable classifer. Reporting misclassified items to Microsoft is NOT supported for Content Safety classifiers yet.
From the source or sender information, you may already know how the message should be routed or handled in these circumstances. Consider using Tag as or Escalate to assign a tag to applicable messages or to send messages to a designated reviewer.
Examine the message details
After reviewing the message basics, open the message to examine the details and determine further remediation actions.
Tip
For lengthy messages, you can save time by summarizing the message (including attachments, transcripts, and recordings) with Copilot in Microsoft Purview.
Select a message to view the complete message header and body information. Several different options and views are available to help you decide the proper course of action:
Sentiment: Messages include a sentiment evaluation (powered by Azure Cognitive Service for Language) to help investigators quickly prioritize potentially riskier messages to address first. The message sentiment is displayed in the Sentiment column and is enabled in the default view. Messages are flagged with one of the following values:
Value Description Positive Messages with Positive sentiment indicate a lower priority for triaging. Negative Messages with Negative sentiment indicate messages to prioritize. Neutral Messages with Neutral sentiment are determined to be neither positive nor negative. Not available Not available appears in the column for file formats that aren't supported. For example, sentiment analysis is not available for any image that's attached to a Teams or email message, text extracted from an OCR image, or text or recordings from a Teams transcript. Not available also appears if the message includes more than 5120 words. Scanning Scanning appears in the the column when communication compliance is trying to determine the appropriate sentiment value for the message. Attachments: This option allows you to examine Modern attachments that match policy conditions. Modern attachments content is extracted as text and is viewable on the Pending tab. For more information, see the Communication compliance feature reference.
Source: This view is the standard message view commonly seen in most web-based messaging platforms. The header information is formatted in the normal style and the message body supports imbedded graphic files and word-wrapped text. If optical character recognition (OCR) is enabled for the policy, images containing printed or handwritten text that match policy conditional are viewed as a child item for the associated message in this view.
Plain text: Text view that displays a line-numbered text-only view of the message and includes keyword highlighting in messages and attachments for sensitive info type terms, terms identified by built-in classifiers assigned to a policy, or for terms included in a dedicated keyword dictionary assigned to a policy. Keyword highlighting, which is currently available for English language only, can help direct you to the area of interest in long messages and attachments. In some cases, highlighted text might be only in attachments for messages matching policy conditions. Embedded files aren't displayed and the line numbering in this view is helpful for referencing pertinent details among multiple reviewers.
Conversation: This view, which is available for Teams chat messages, displays up to five messages before and after a message to help reviewers view the activity in the conversational context. Select Load more to load up to twenty messages before and after a message. To download messages, select Download conversation. This downloads an image file of everything you see in the user interface and also a .csv file of all the message metadata (UserId, UserName, and so on).
The Conversation view context helps reviewers quickly evaluate messages and make more informed message resolution decisions. Real-time message additions to conversations are displayed, including all inline images, emojis, and stickers available in Teams. Image or text file attachments to messages aren't displayed. Notifications are automatically displayed for messages that have been edited or for messages that have been deleted from the Conversation window. When a message is resolved, the associated conversational messages aren't retained with the resolved message.
Pattern detected notification: Many harassing and bullying actions over time involve reoccurring instances of the same behavior by a user. The Pattern detected notification is displayed in the message details and raises attention to the message. Detection of patterns is on a per-policy basis and evaluates behavior over the last 30 days when at least two messages are sent to the same recipient by a sender. Investigators and reviewers can use this notification to identify repeated behavior to evaluate the message as appropriate.
Translation: This view automatically converts message text to the language configured in the Displayed language setting in the Microsoft 365 subscription for each reviewer. This includes the text for the policy match and everything included in the conversation view (up to five messages before and five messages after the policy match). The Translation view helps broaden investigative support for organizations with multilingual users and eliminates the need for additional translation services outside of the communication compliance review process. Using Microsoft translation services, communication compliance automatically detects if the text is in a different language than the user's current system setting and displays alert message text accordingly. For a complete list of supported languages, see Microsoft Translator Languages. Languages listed in the Translator Language List are supported in the Translation view.
User activity: This view provides risk profile, policy matches, and user activities captured by insider risk management and communication compliance. This integration helps communication compliance investigators quickly see risk severity and the associated activities for the user while investigating and triaging pending policy matches.
The User activity view displays the Insider risk severity level for the user and has two sections, one for communication compliance policy matches and activities and one for insider risk management risk activities. View the risk severity of the user from insider risk management in the Source tab if data sharing is enabled. For more information, see Share insider risk management data with other solutions.
Communication compliance policy matches: This section displays the total number of communication Policy matches and the total number of Remediation actions for the user included in this policy match.
Select View details in this section to display a timeline of communication compliance activities for the user. This timeline includes:
- Totals for Policy matches and Remediation actions for the user
- Details for each activity associated with the user for the past 30 days.
Insider risk activity: This section displays the total number of Risk activities and the total number of Unusual activities for activities associated with this user for insider risk management policies. Unusual activities are activities for the user that are considered potentially risky, as they're unusual and a departure from their typical activities.
Select View details in this section to display a timeline of insider risk activity for the user. This timeline includes:
- The insider risk severity level.
- Totals for All activities and Unusual activities.
- Details for each activity associated with the user from the Activity explorer in insider risk management.
To view the insider risk activities in insider risk management, select Open in insider risk management.
Summarize a message by using Copilot in Microsoft Purview
You can use Copilot in Microsoft Purview to provide a contextual summary of a Teams, email, or Viva Engage message included in a policy match. The summary provided is in the context of one or more trainable classifiers that flag the message (for example, stock manipulation). This can save time for investigators if the message content is lengthy.
Copilot in Microsoft Purview summarizes the entire message, including any video recordings, meetings transcripts, or attachments (docx, pdf, or txt files).
Limitations
- The message content must be at least 100 words and less than 15,000 words. If the message content is less than 100 words or more than 15,000 words, Copilot in Microsoft Purview doesn't summarize it.
- At this time, only English language messages are supported for summarization.
- At this time, only individual Teams messages can be summarized. If you summarize an individual Teams message, Copilot does not pull in the surrounding conversation.
Prerequisites for using Copilot in Microsoft Purview
To summarize a message in communication compliance using Copilot in Microsoft Purview, you must have specific licenses and you must onboard your organization to Copilot in Microsoft Purview. Learn more about Copilot in Microsoft Purview licensing requirements and onboarding. You must also be a member of the Communication Compliance, Communication Compliance Analysts or Communication Compliance Investigators role.
Summarize a message
In communication compliance, go to the Policies page, and then open any policy to view policy matches for that policy.
Select a message in the list. You can select a parent item or a child item. It's usually easier to select the parent item, however.
Below the message details, select Summarize. This opens the Copilot panel on the right side of the screen and displays a summary of the message.
Important
You might see a generic error message that says "An error occurred" after selecting Summarize. This error message can appear for any of the following reasons:
- You don't have the required license for Copilot in Microsoft Purview.
- You don't have the required communication compliance role and/or the Security Copilot contributor role. To use Copilot in Microsoft Purview, you must have one of the following communication compliance roles: Communication Compliance, Communication Compliance Analysts, Communication Compliance Investigators. You must also have the Security Copilot contributor role, which should be turned on by default for all users in a Microsoft Entra organization.
- There's an internal error. Microsoft will provide more information for these errors.
To use Copilot to create the summary, select one of the suggested prompts at the bottom of the panel. For example, if the classifier that flagged a message is Stock manipulation, select Summarize this message and supported attachments in the context of Stock manipulation category detected. You can also enter an open-ended question in the "Ask a question" box.
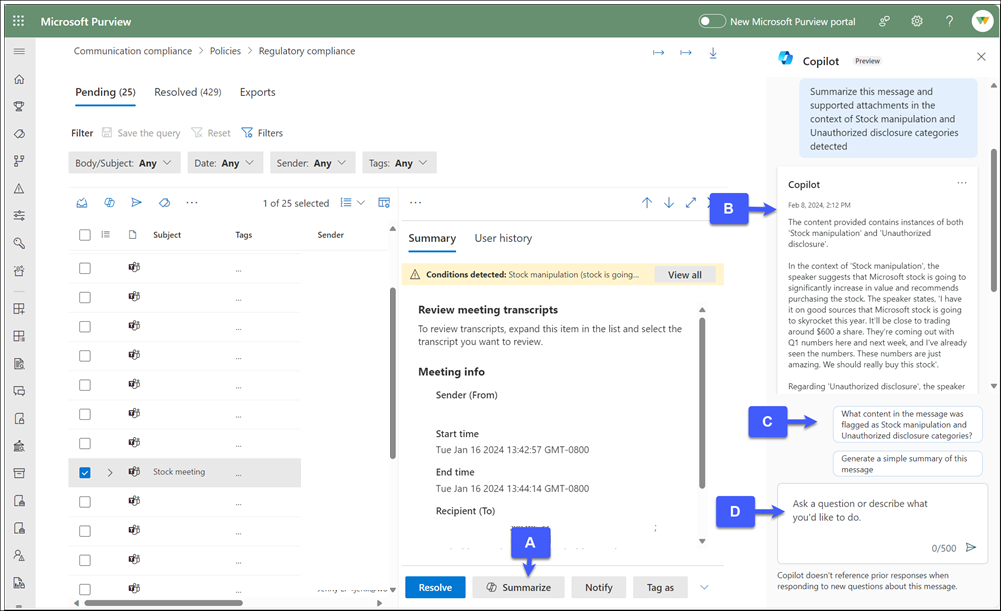
a. Summarize.
b. Summary generated by Summarize.
c. Suggested Copilot prompts.
d. "Ask a question" box for open-ended Copilot questions.Note
Only message content is summarized. If you ask a question relevant to the message content, Copilot provides a result. If the question isn't relevant to message content, Copilot instructs you to ask a different question.
If you want to provide feedback on the summarized content, select the drop-down arrow in the lower-right corner below the summary, and then enter your feedback.
After reviewing the summary, you can remediate the policy match like any other policy match (see next section).
Note
Copilot in Microsoft Purview responses are also recorded in Microsoft Security Copilot.
Understanding hidden matches
When a communication compliance policy is triggered, it highlights the exact matches in the Plain text tab. However, policies can also flag messages where the keywords are hidden and embedded in non-visible metadata, such as HTML tags or encoded strings. By default, this content is not visible in the plain text view.
The following are some example scenarios where hidden content matches might occur:
HTML tags: Hyperlinks embedded in HTML tags, for example:
<a href="https://example.com">Click here</a>.Alternative text for images: Descriptive text for images, for example:
<img src="sunset.png" alt="Sunset over the lake">Encoded strings: Encoded strings that represent different content when decoded, for example:
Base64: U3Vuc2V0IG92ZXIgdGhlIGxha2U=decodes to Sunset over the lakeFilename of attachment: The file name of the attachment may lead to a policy match but is not clearly highlighted in the text view.
OCR: Text extracted from images using Optical Character Recognition (OCR).
If a message appears not to match the conditions set for the policy, complete the following steps:
- Select and download the message with the policy match.
- Extract the contents of the zipped folder.
- Locate the .eml file.
- Open the .eml file using any text editor.
- Use the Find function to search for the individual keywords in the policy conditions to identify where the match occurs.
Decide on a remediation action
After reviewing message details, you can choose from several remediation actions:
Resolve: Selecting Resolve immediately removes the message from the Pending queue and no further action can be taken on the message. When you select Resolve, you close the message without further classification. You can also mark the message as misclassified if it was incorrectly generated by the alerting process and any trainable classifiers. All resolved messages are displayed in the Resolved tab.
To save investigators time in the case of duplicate policy matches across multiple policies, the Cross-policy resolution setting (preview) is turned on by default, which means that when a policy match is resolved, communication compliance automatically resolves all instances of the same policy match in any policy where it's detected, regardless of the reviewer's scope. Cross-policy resolution actions are noted in the item history for each policy and the number of Resolved items is incremented in the Items and actions per policy and Items and actions per location reports for all related policies.
When the Cross-policy resolution setting is turned on, this message appears in the Resolve pane.
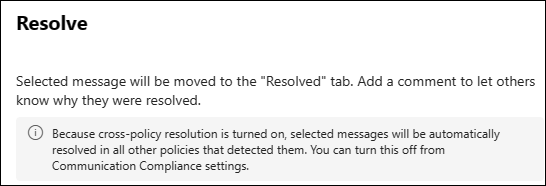
If you don't want to automatically resolve all instances of the same policy match when an investigator resolves a policy match, you can turn off the Cross-policy resolution setting. Anyone who can resolve messages (anyone with the Communication Compliance, Communication Compliance Investigators, or Communication Compliance Analyst role) will know if the setting is turned off because the message in the Resolve pane will disappear. To turn off the setting, in the Microsoft Purview portal, select Settings in the upper-right corner of the page, select Communication Compliance, and then select the Cross-policy resolution setting. In the Compliance portal, select Settings in the upper-right corner of the page, and then select the Cross-policy resolution setting.
Power Automate: Use a Power Automate flow to automate process tasks for a message. By default, communication compliance includes the Notify manager when a user has a communication compliance alert flow template that reviewers can use to automate the notification process for users with message alerts. For more information about creating and managing Power Automate flows in communication compliance, see the Step 5: Consider Power Automate flows section in this article.
Tag as: Tag the message as Compliant, Non-compliant, or Questionable as it relates to the policies and standards for your organization. You can also create a custom tag. Adding tags and tagging comments helps you micro-filter messages for escalations or as part of other internal review processes. After tagging is complete, you can also choose to resolve the message to move it out of the pending queue. You can filter on any tag value.
Notify: Use Notify to assign a custom notice template to the message and send a warning notice to the user. Choose the appropriate notice template configured in the Communication compliance settings area and select Send to email a reminder to the user that sent the message and to resolve the issue.
Escalate: Use Escalate to choose other people in your organization who should review the message. Choose from a list of reviewers configured in the communication compliance policy to send an email notification requesting additional review of the message. The selected reviewer can use a link in the email notification to go directly to items escalated to them for review.
Escalate for investigation: Use Escalate for investigation to create a new eDiscovery (Premium) case for single or multiple messages. Provide a name and notes for the new case. The custodian is automatically filled in for you. You don't need any additional permissions to manage the case. Creating a case doesn't resolve or create a new tag for the message. You can select a total of 100 messages when creating an eDiscovery (Premium) case during the remediation process. Messages in all communication channels included in communication compliance are supported. For example, you could select 50 Microsoft Teams chats, 25 Exchange Online email messages, and 25 Viva Engage messages when you open a new eDiscovery (Premium) case for a user.
Remove message in Teams: Use Remove message in Teams to block potentially inappropriate messages and content identified in messages from Microsoft Teams channels and 1:1 and group chats. This includes Teams chat messages reported by users and chat messages detected using machine-learning and classifier-based communication compliance policies. Removed messages and content are replaced with a policy tip that explains that it's blocked and the policy that applies to its removal from view. Recipients are provided a link in the policy tip to learn more about the applicable policy and the review process. The sender receives a policy tip for the blocked message and content but can review the details of the blocked message and content for context regarding the removal.
Create a custom tag
You can tag a policy match as Compliant, Non-compliant, or Questionable as it relates to the policies and standards for your organization. If you need more flexibility than the standard tags provide, create a custom tag. For example, you might want to create an Escalated tag so investigators can let other team members know that a policy match has already been escalated. Since you can apply multiple tags to any policy match, using the same example, investigators could apply that tag and also apply the Non-compliant tag for a policy match.
Keep the following in mind for custom tags:
- You can apply tags to policy matches that appear on the Pending tab.
- You can apply multiple tags to a policy match.
- You can create up to 10 custom tags per policy.
- You create custom tags at the policy level so if you want to use the same custom tag for multiple policies, you must recreate the tag for each policy.
- When you apply a custom tag to a policy match:
- The tag appears in the Tags column in the list of policy matches. If you apply more than one tag, each tag appears in the Tags column.
- The tag appears in the Tags filter. You can then select the checkbox for that tag to filter all policy matches by that tag.
- A Custom tag column appears in the following reports: Items and actions per policy, Items and actions per location, and Activity by user.
- If you delete a custom tag for a policy:
- It's removed from any previous items that were tagged with that custom tag.
- You will no longer be able to filter by that tag.
Tip
Any action that you do with custom tags is tracked in the History of remediation actions pane. Select View item history to display this pane.
Create and apply a custom tag for a policy match
- On the Policies page, select a policy to view the policy matches for that policy.
- Select the checkbox for the policy match that you want to create a custom tag for. Select the checkboxes for multiple policy matches if you want to apply a custom tag in bulk.
- Select Tag as on the command bar.
- In the Tag item pane on the right side of the screen, select Add a new tag.
- Enter the name of the new tag, and then press Enter to add the new tag.
Note
A custom tag must be between 3 and 64 characters and can't include special characters. Spaces and hyphens are allowed.
- Select the checkbox for the new tag to apply it to the policy match.
- In the Comment box, add a comment to describe the purpose of the tag (optional).
- Select Save.
Edit or delete a custom tag
- On the Policies page, select a policy to view the policy matches for that policy.
- Select the checkbox for the policy match that has the custom tag you want to edit.
- Select Tag as on the command bar.
- In the Tag item pane on the right side of the screen, select the ellipsis next to the custom tag.
- Select Edit, and then make your changes or select Delete to delete the tag.
Important
If you delete a custom tag, it's removed from any previous items that were tagged with that custom tag. You will no longer be able to filter by that tag.
- Select Save.
Review Microsoft Teams meetings transcripts
If you have deployed Microsoft Teams in your tenant, you can review Teams meetings transcripts for actionable alerts. Teams transcripts are automatically included if you choose Teams as a Microsoft 365 location when you create a custom policy or when you create a policy based on a template.
Scheduled meetings: Communication compliance ignores communication direction for Teams transcripts. If an individual is an invitee or is present in a scheduled (non-recurring) meeting, all of the meeting content is included, regardless of who says what in the meeting. This also helps in situations where a user is attending the meeting through a hub device in a conference room, since it's not always possible to tell whether an offending communication comes from an in-scope user. Since all meeting content is included, an investigator can review the recording of the meeting to determine if the offending communication was said by an in-scope user.
Recurring meetings: For recurring meetings, only the following users are evaluated:
- Users who were invited to the meeting
- Users identified by the transcript as having spoken during the meeting
Unscheduled meetings: For unscheduled meetings (Meet now meetings), only users who have been identified by the transcript as having spoken during the meeting are evaluated.
Requirements
To review Teams meeting transcripts, you must turn on meeting transcripts for the tenant, since meeting transcripts are not turned on by default. Learn more about turning on meeting transcripts for a tenant.
Limitations
You can set one or more of the following policy conditions:
- Content matches any of these classifiers.
- Content contains any of these sensitive info types.
- Message contains any of these words.
- Message contains none of these words.
Any other policy conditions are ignored. Learn more about conditional settings.
Note
If you don't set any conditions, transcripts are captured for all meetings.
Only sensitive info types, keyword lists, and regulatory trainable classifiers are detected. Regulatory trainable classifiers include:
- Corporate sabotage
- Gifts and entertainment
- Money laundering
- Regulatory collusion
- Stock manipulation
- Unauthorized disclosure
Note
All other classifiers, including business conduct classifiers, are not detected.
Ad-hoc (unscheduled) meetings are not captured.
External meetings are not captured if the meeting organizer is outside the tenant.
Meeting recordings started by an uninvited user are not captured.
Resolve an alert for a communication in a meeting transcript
After a policy is created, when a transcript is detected that contains offending content, an alert is triggered to bring the offending content and background context to the attention of an investigator.
To resolve an alert related to a meeting transcript:
- Select the Source tab and then review the transcript for the offending content. The Source tab shows the entire transcript. When you select the Source tab, the transcript is automatically scrolled to the line that contains the policy match. The offensive keyword/phrase is highlighted.
- Use the Plain text tab to do a line-by-line review of the text, including start and stop times in relation to the overall meeting time. Text is captured 30 seconds before and after the offending communication.
- Select the Translation tab to review translations in up to eight languages for the Plain text tab. Messages in other languages are automatically converted to the display language of the reviewer.
- Select the User history tab to see a historical view of all user message remediation activities, such as past notifications and escalations for policy matches.
- Use Resolve, Notify, Tag as, Escalate, and Escalate for investigation options to resolve the alert. To learn more about these options, see Decide on a remediation action.
Unresolve messages
When messages are resolved, they're removed from the Pending tab and displayed in the Resolved tab. Investigation and remediation actions aren't available for messages in the Resolved tab. However, there may be instances where you need to take additional action on a message that was mistakenly resolved or that needs further investigation after initial resolution. You can use the Unresolve command to move one or more messages from the Resolved tab back to the Pending tab.
Unresolve a message
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Communication Compliance solution.
- Select Policies in the left navigation, and then select a policy that contains the resolved message to view the policy matches.
- Select the Resolved tab.
- On the Resolved tab, select one or more messages.
- On the command bar, select Unresolve.
- On the Unresolve item pane, add any applicable comments, and then select Save.
- Select the Pending tab to verify that the selected items are displayed.
Archive message details outside of communication compliance (optional)
You can export or download message details if you need to archive the messages in a separate storage solution. If you select one or more policy matches, and then select Download in the bar over the list, the selected messages are automatically added to a .zip file that you can save in storage outside of Microsoft 365. The size limit for files downloaded by using Download is 3 MB.
Export a collection of message details that exceeds 3 MB in size
If you want to download messages that cumulatively exceed 3 MB in size, use Export files (displayed in the upper-right corner of the Policies page). For example, you might want to download policy matches each week for archiving purposes. The download size limit for the Export files command is 3 GB. The maximum number of items depends on whether you select documents (limit of 1,000 items) or users (limit of 50,000). Files are exported to a .zip file that you can then download. The .zip file contains all the message files as a well as a summary .TXT file that includes data for the following fields: Document, Doc ID, Custodian, Subject/title, File name, File type, Error, and Message.
On the Exports tab, the export will either have a status of In progress or Ready to download. To download a file that has a Ready to download status, select the files batch in the Name list, and then select Download export(s) over the list.
You can either select the policy matches that you want to export, select Export files, and then select the list of documents or users you want to export, or you can select Export files and then select the documents, users, and date ranges that you want to export. After you select Export, it will take a few minutes for the job to complete. You'll receive an email notification with a link to the Exports tab when the export is ready to download. To download a file that has a Ready to download status, select the files batch in the Name list, and then select Download export(s) over the list.
Note
To include attachments in exported files, you must select them manually in the list of policy matches. They're not automatically included with their parent message file.
Tip
You can also create and download a Message details report.
Consider Power Automate flows
Microsoft Power Automate is a workflow service that automates actions across applications and services. By using flows from templates or created manually, you can automate common tasks associated with these applications and services. When you enable Power Automate flows for communication compliance, you can automate important tasks for alerts and users. You can configure Power Automate flows to notify managers when users have communication compliance alerts and other applications.
Customers with Microsoft 365 subscriptions that include communication compliance don't need additional Power Automate licenses to use the recommended default communication compliance Power Automate template. The default template can be customized to support your organization and cover core communication compliance scenarios. If you choose to use premium Power Automate features in these templates, create a custom template using the Microsoft Purview connector, or use Power Automate templates for other compliance areas in Microsoft Purview, you may need additional Power Automate licenses.
Important
Are you receiving prompts for additional license validation when testing Power Automate flows? Your organization may not have received service updates for this preview feature yet. Updates are being deployed and all organizations with Microsoft 365 subscriptions that include communication compliance should have license support for flows created from the recommended Power Automate templates before October 30, 2020.
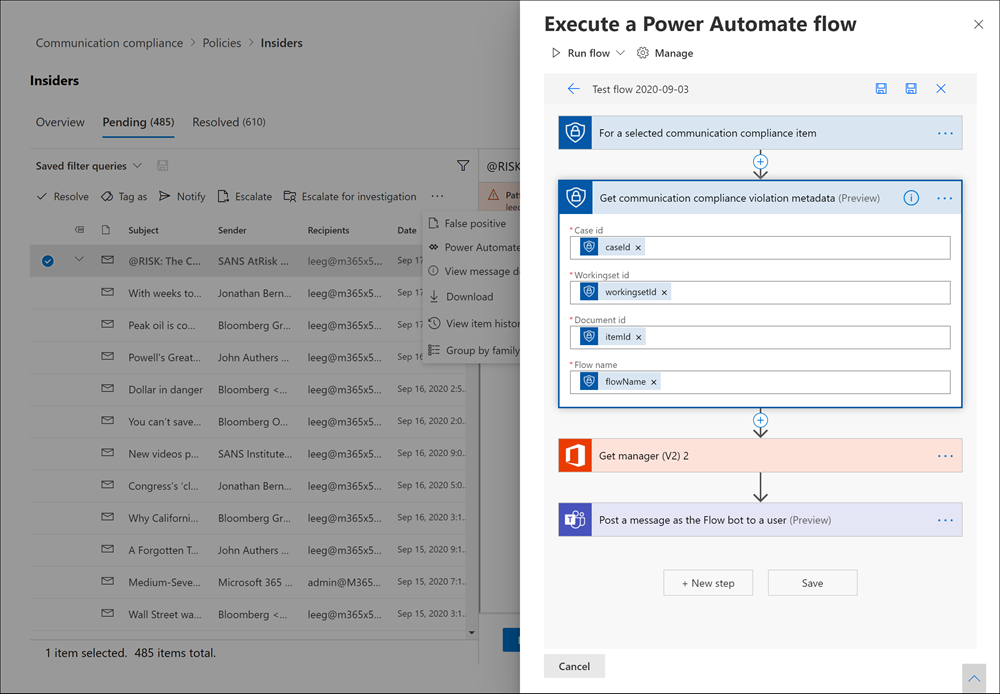
The following Power Automate template is provided to customers to support process automation for communication compliance alerts:
- Notify manager when a user has a communication compliance alert: Some organizations may need to have immediate management notification when a user has a communication compliance alert. When this flow is configured and selected, the manager for the case user is sent an email message with the following information about all alerts:
- Applicable policy for the alert
- Date/Time of the alert
- Severity level of the alert
Create notice templates
You can create notice templates if you want to send users an email reminder notice for policy matches as part of the issue resolution process. Notices can only be sent to the user email address associated with the policy match that generated the specific alert for remediation. When selecting a notice template to apply to a policy violation as part of the remediation workflow, you can choose to accept the field values defined in the template or overwrite the fields as needed.
Notices templates are custom email templates where you can define the following message fields in the Communication compliance settings area:
| Field | Required | Details |
|---|---|---|
| Template name | Yes | Friendly name for the notice template that you'll select in the notify workflow during remediation, supports text characters. |
| Sender address | Yes | Address of one or more users or groups that sent the message to the user with a policy match, selected from the Active Directory for your subscription. |
| CC and BCC addresses | No | Optional users or groups to be notified of the policy match, selected from the Active Directory for your subscription. |
| Subject | Yes | Information that appears in the subject line of the message, supports text characters. |
| Message body | Yes | Information that appears in the message body, supports text or HTML values. |
HTML for notices
If you'd like to create more than a simple text-based email message for notifications, you can create a more detailed message by using HTML in the message body field of a notice template. The following example provides the message body format for a basic HTML-based email notification template:
<!DOCTYPE html>
<html>
<body>
<h2>Action Required: Contoso Employee Code of Conduct Policy Training</h2>
<p>A recent message you've sent has generated a policy alert for the Contoso Employee <a href='https://www.contoso.com'>Code of Conduct Policy</a>.</p>
<p>You are required to attend the Contoso Employee Code of Conduct <a href='https://www.contoso.com'>training</a> within the next 14 days. Please contact <a href='mailto:hr@contoso.com'>Human Resources</a> with any questions about this training request.</p>
<p>Thank you,</p>
<p><em>Human Resources</em></p>
</body>
</html>
Note
HTML href attribute implementation in the communication compliance notification templates currently support only single quotation marks instead of double quotation marks for URL references.
Automate tasks for alerts and users with Microsoft Power Automate
To create a Power Automate flow from a recommended default template, use the Manage Power Automate flows option from Automate when working directly in an alert. To create a Power Automate flow with Manage Power Automate flows, you must be a member of at least one communication compliance role group.
Automate tasks
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Communication Compliance solution.
- Select Policies in the left navigation, and then select the policy that includes the policy matches that you want review.
- Select the Pending tab, and select a policy match.
- Select Power Automate from the alert action menu.
- On the Power Automate page, select a default template from the Communication compliance templates you may like section on the page.
- The flow lists the embedded connections needed for the flow and displays if the connection statuses are available. If needed, update any connections that aren't displayed as available. Select Continue.
- By default, the recommended flows are preconfigured with the recommended communication compliance and Microsoft 365 service data fields required to complete the assigned task for the flow. If needed, customize the flow components by using Show advanced options and configuring the available properties for the flow component.
- If needed, add any additional steps to the flow by selecting New step. In most cases, this change shouldn't be needed for the recommended default templates.
- Select Save draft to save the flow for further configuration later, or select Save to complete the configuration for the flow.
- Select Close to return to the Power Automate flow page. The new template is listed as a flow on the My flows tab and is automatically available for the user that created the flow when working with communication compliance alerts.
Share a Power Automate flow
By default, Power Automate flows created by a user are only available to that user. For other communication compliance users to have access and use a flow, the flow must be shared by the flow creator. To share a flow, use Power Automate when working directly in an alert.
To share a Power Automate flow, you must be a member of at least one communication compliance role group.
Share a flow
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Communication Compliance solution.
- Select Policies in the left navigation, and then select the policy that contains the policy matches that you want to review.
- Select the Pending tab, and select a pending policy match.
- Select Power Automate from the alert action menu.
- On the Power Automate flows page, select the My flows or Team flows tab.
- Select the flow to share, then select Share from the Flow Options menu.
- On the flow sharing page, enter the name of the user or group you want to add as an owner for the flow.
- On the Connection Used dialog, select OK to acknowledge that the added user or group will have full access to the flow.
Edit a Power Automate flow
If you need to edit a flow, use Power Automate when working directly in an alert. To edit a Power Automate flow, you must be a member of at least one communication compliance role group.
Edit a flow
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Communication Compliance solution.
- Select Policies in the left navigation, and then select the policy that contains the policy matches that you want to review.
- Select the Pending tab, and then select a pending policy match.
- Select Power Automate from the alert action menu.
- On the Power Automate flows page, select the flow to edit. Select Edit from the flow control menu.
- Select ellipsis > Settings to change a flow component setting or ellipsis > Delete to delete a flow component.
- Select Save, and then select Close when you've finished editing the flow.
Delete a Power Automate flow
If you need to delete a flow, use Power Automate when working directly in an alert. To delete a Power Automate flow, you must be a member of at least one communication compliance role group.
Delete a flow
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Communication Compliance solution.
- Select Policies in the left navigation, and then select the policy that contains the policy matches that you want to review.
- Select the Pending tab, and select a pending policy match.
- Select Power Automate from the alert action menu.
- On the Power Automate flows page, select the flow that you want to delete. Select Delete from the flow control menu.
- On the deletion confirmation dialog, select Delete to remove the flow or select Cancel.