Audit and deploy virtual network flow logs using Azure Policy
Azure Policy helps you enforce organizational standards and assess compliance at scale. Common use cases for Azure Policy include implementing governance for resource consistency, regulatory compliance, security, cost, and management. To learn more about Azure policy, see What is Azure Policy? and Quickstart: Create a policy assignment to identify noncompliant resources.
In this article, you learn how to use two built-in policies to manage your setup of virtual network flow logs. The first policy flags any virtual network that doesn't have flow logging enabled. The second policy automatically deploys virtual network flow logs to virtual networks that don't have flow logging enabled.
Prerequisites
An Azure account with an active subscription. Create an account for free.
A virtual network. If you need to create a virtual network, see Create a virtual network using the Azure portal.
Audit flow logs configuration for virtual networks using a built-in policy
The Audit flow logs configuration for every virtual network policy audits all existing virtual networks in a scope by checking all Azure Resource Manager objects of type Microsoft.Network/virtualNetworks for linked flow logs via the flow log property of the virtual network. It then flags any virtual network that doesn't have flow logging enabled.
To audit your flow logs using the built-in policy, follow these steps:
Sign in to the Azure portal.
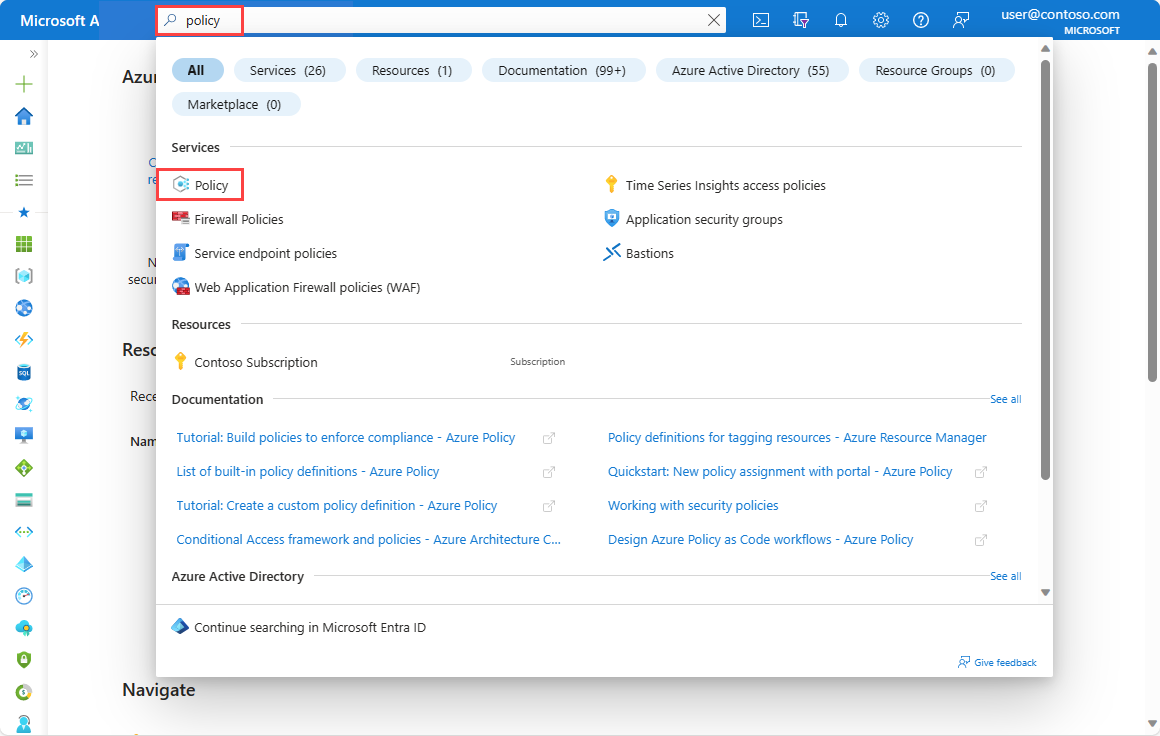
In the search box at the top of the portal, enter policy. Select Policy from the search results.
Select Assignments, and then select Assign policy.
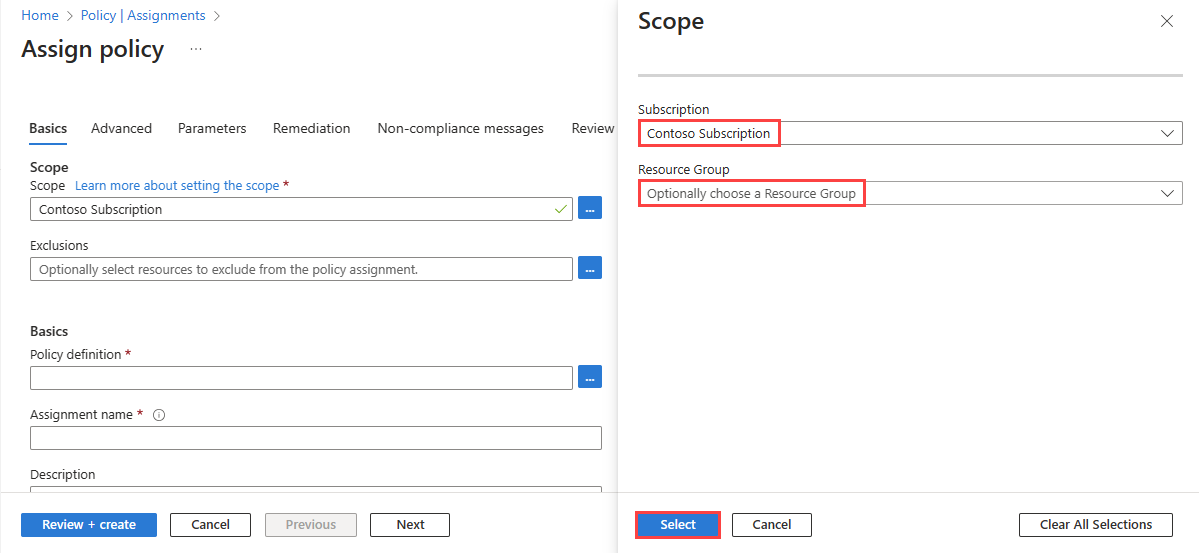
Select the ellipsis (...) next to Scope to choose your Azure subscription that has the virtual networks that you want to check using the policy. You can also choose the resource group that has the virtual networks. After you make your selections, select the Select button.
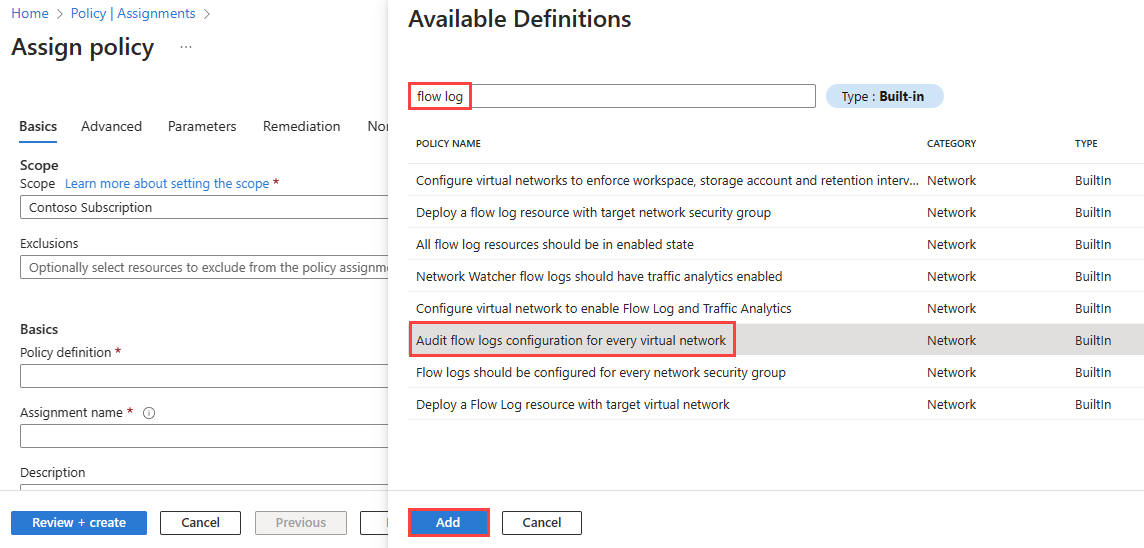
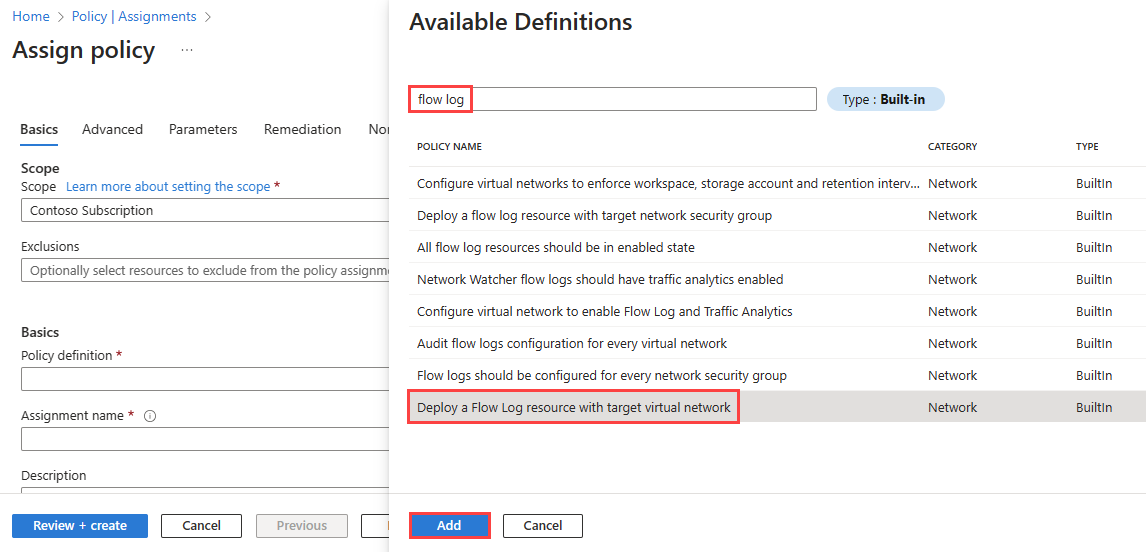
Select the ellipsis (...) next to Policy definition to choose the built-in policy that you want to assign. Enter flow log in the search box, and then select the Built-in filter. From the search results, select Audit flow logs configuration for every virtual network, and then select Add.
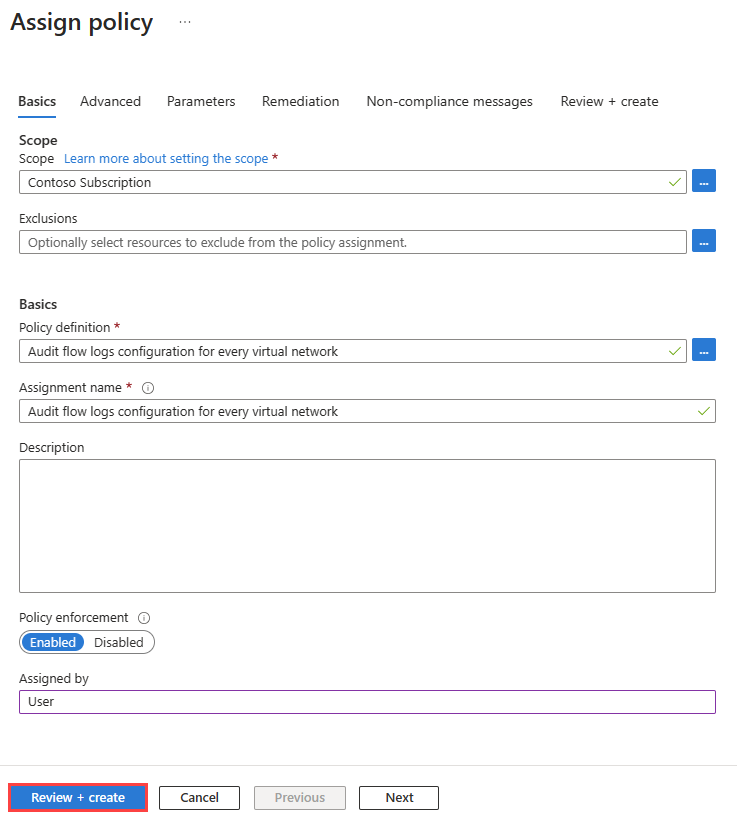
Enter a name in Assignment name or use the default name, and then enter your name in Assigned by.
This policy doesn't require any parameters. It also doesn't contain any role definitions, so you don't need to create role assignments for the managed identity on the Remediation tab.
Select Review + create, and then select Create.
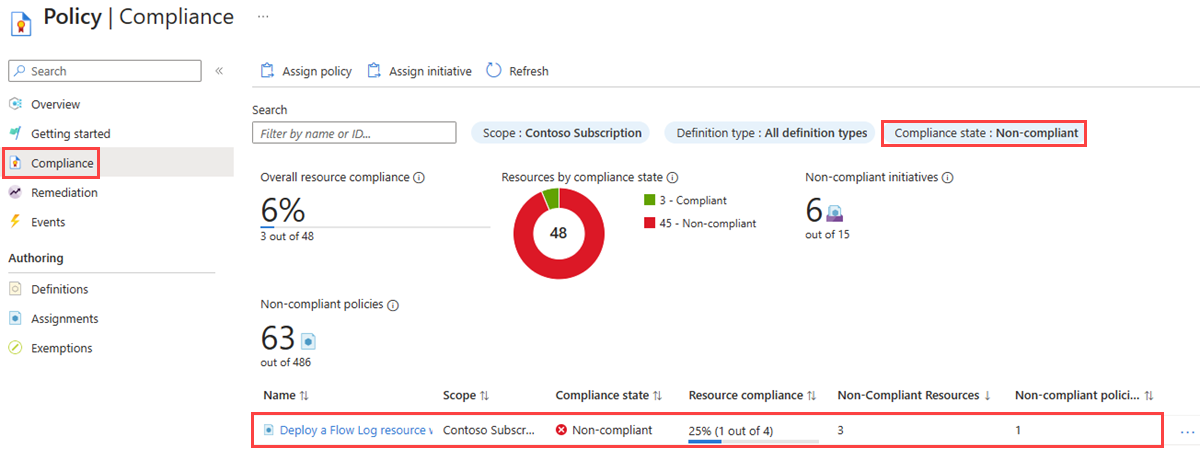
Select Compliance and change the Compliance state filter to Non-compliant to list all noncompliant policies. Search for the name of your audit policy that you created, and then select it.
In the policy compliance page, change the Compliance state filter to Non-compliant to list all noncompliant virtual networks. In this example, there are three noncompliant virtual networks out of four.
Deploy and configure virtual network flow logs using a built-in policy
The Deploy a flow log resource with target virtual network policy checks all existing virtual networks in a scope by checking all Azure Resource Manager objects of type Microsoft.Network/virtualNetworks. It then checks for linked flow logs via the flow log property of the virtual network. If the property doesn't exist, the policy deploys a flow log.
Important
We recommend disabling network security group flow logs before enabling virtual network flow logs on the same underlying workloads to avoid duplicate traffic recording and additional costs. For example, if you enable network security group flow logs on the network security group of a subnet, then you enable virtual network flow logs on the same subnet or parent virtual network, you might get duplicate logging (both network security group flow logs and virtual network flow logs generated for all supported workloads in that particular subnet).
To assign the deployIfNotExists policy, follow these steps:
Sign in to the Azure portal.
In the search box at the top of the portal, enter policy. Select Policy from the search results.
Select Assignments, and then select Assign policy.

Select the ellipsis (...) next to Scope to choose your Azure subscription that has the virtual networks that you want to check using the policy. You can also choose the resource group that has the virtual networks. After you make your selections, select the Select button.
Select the ellipsis (...) next to Policy definition to choose the built-in policy that you want to assign. Enter flow log in the search box, and then select the Built-in filter. From the search results, select Deploy a flow log resource with target virtual network, and then select Add.
Note
You need Contributor or Owner permission to use this policy.
Enter a name in Assignment name or use the default name, and then enter your name in Assigned by.
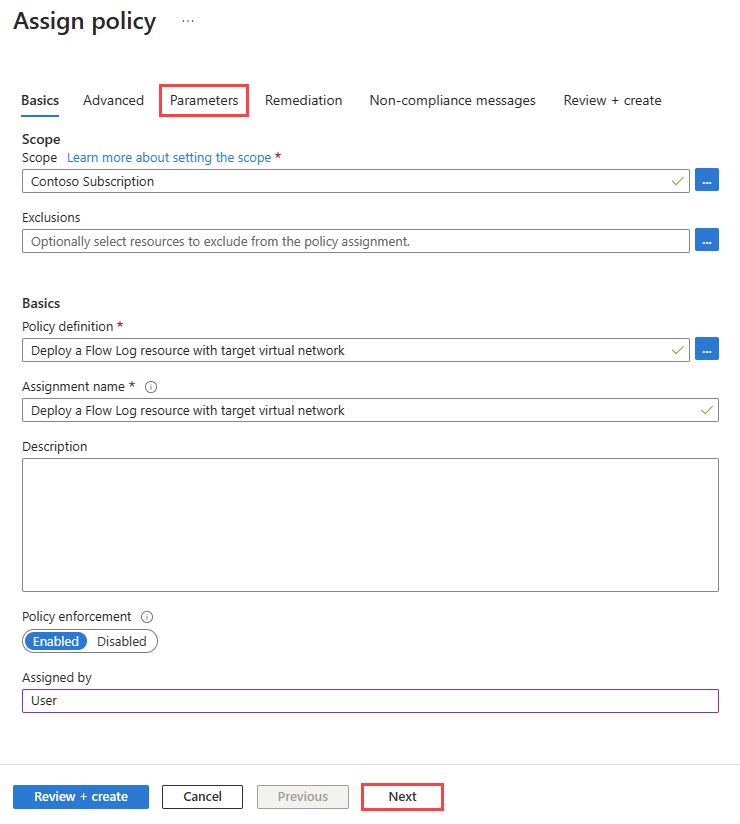
Select Next button twice, or select the Parameters tab. Then select the following values:
Setting Value Effect Select DeployIfNotExists to enable the execution of the policy. The other available option is: Disabled. Virtual Network Region Select the region of your virtual network that you're targeting with the policy. Storage Account Select the storage account. The storage account must be in the same region as the virtual network. Network Watcher RG Select the resource group of your Network Watcher instance. The flow logs created by the policy are saved into this resource group. Network Watcher Select the Network Watcher instance of the selected region. Number of days to retain flowlogs Select the number of days that you want to keep your flow logs data in the storage account. The default value is 30 days. If you don't want to apply any retention policy, enter 0. Select Next or the Remediation tab.
Select Create a remediation task checkbox.
Select Review + create, and then select Create.
Select Compliance and change the Compliance state filter to Non-compliant to list all noncompliant policies. Search for the name of your deploy policy that you created, and then select it.
In the policy compliance page, change the Compliance state filter to Non-compliant to list all noncompliant virtual networks. In this example, there are three noncompliant virtual networks out of four.
Note
The policy takes some time to evaluate virtual networks in the specified scope and deploy flow logs for the noncompliant virtual networks.
Go to Flow logs under Logs in Network Watcher to see the flow logs that were deployed by the policy.
In the policy compliance page, verify that all virtual networks in the specified scope are compliant.
Note
It can take up to 24 hours to update resource compliance status in Azure Policy compliance page. For more information, see Understand evaluation outcomes.