Tutorial: Configure HTTPS on an Azure CDN custom domain
Important
Azure CDN Standard from Microsoft (classic) will be retired on September 30, 2027. To avoid any service disruption, it is important that you migrate your Azure CDN Standard from Microsoft (classic) profiles to Azure Front Door Standard or Premium tier by September 30, 2027. For more information, see Azure CDN Standard from Microsoft (classic) retirement.
Azure CDN from Edgio will be retired on November 4, 2025. You must migrate your workload to Azure Front Door before this date to avoid service disruption. For more information, see Azure CDN from Edgio retirement FAQ.
This tutorial shows how to enable the HTTPS protocol for a custom domain associated with an Azure CDN endpoint.
The HTTPS protocol on your custom domain (for example, https://www.contoso.com), ensures your sensitive data is delivered securely via TLS/SSL. When your web browser is connected via HTTPS, the browser validates the web site's certificate. The browser verifies it's issued by a legitimate certificate authority. This process provides security and protects your web applications from attacks.
Azure CDN supports HTTPS on a CDN endpoint hostname, by default. For example, if you create a CDN endpoint (such as https://contoso.azureedge.net), HTTPS is automatically enabled.
Some of the key attributes of the custom HTTPS feature are:
No extra cost: There aren't costs for certificate acquisition or renewal and no extra cost for HTTPS traffic. You pay only for GB egress from the CDN.
Simple enablement: One-click provisioning is available from the Azure portal. You can also use REST API or other developer tools to enable the feature.
Complete certificate management is available:
- All certificate procurement and management is handled for you.
- Certificates are automatically provisioned and renewed before expiration.
In this tutorial, you learn how to:
- Enable the HTTPS protocol on your custom domain.
- Use a CDN-managed certificate
- Use your own certificate
- Validate the domain
- Disable the HTTPS protocol on your custom domain.
Prerequisites
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. To get started, see Install Azure PowerShell. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
Before you can complete the steps in this tutorial, create a CDN profile and at least one CDN endpoint. For more information, see Quickstart: Create an Azure CDN profile and endpoint.
Associate an Azure CDN custom domain on your CDN endpoint. For more information, see Tutorial: Add a custom domain to your Azure CDN endpoint.
Important
CDN-managed certificates are not available for root or apex domains. If your Azure CDN custom domain is a root or apex domain, you must use the Bring your own certificate feature.
TLS/SSL certificates
To enable HTTPS on an Azure CDN custom domain, you use a TLS/SSL certificate. You choose to use a certificate that is managed by Azure CDN or use your certificate.
- Option 1 (default): Enable HTTPS with a CDN-managed certificate
- Option 2: Enable HTTPS with your own certificate
Azure CDN handles certificate management tasks such as procurement and renewal. After you enable the feature, the process starts immediately.
If the custom domain is already mapped to the CDN endpoint, no further action is needed. Azure CDN processes the steps and completes your request automatically.
If your custom domain is mapped elsewhere, use email to validate your domain ownership.
To enable HTTPS on a custom domain, follow these steps:
Go to the Azure portal to find a certificate managed by your Azure CDN. Search for and select CDN profiles.
Choose your profile:
- Azure CDN Standard from Microsoft
- Azure CDN Standard from Edgio
- Azure CDN Premium from Edgio
In the list of CDN endpoints, select the endpoint containing your custom domain.
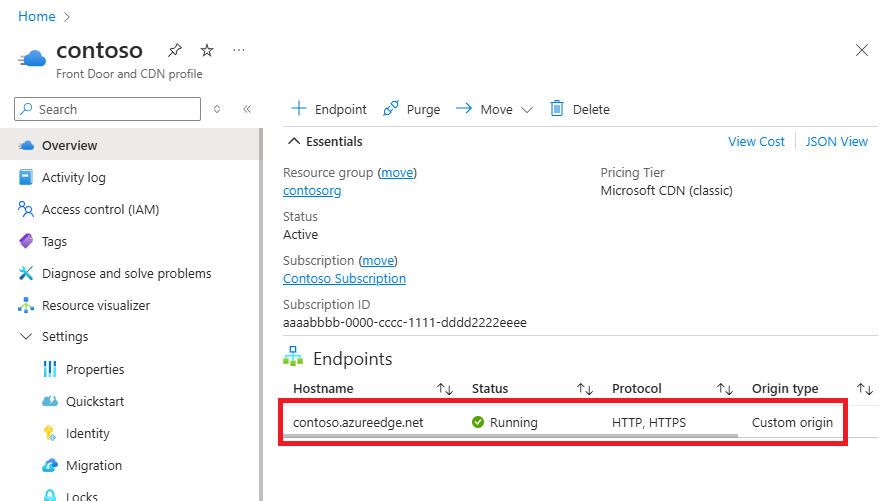 The Endpoint page appears.
The Endpoint page appears.In the list of custom domains, select the custom domain for which you want to enable HTTPS.
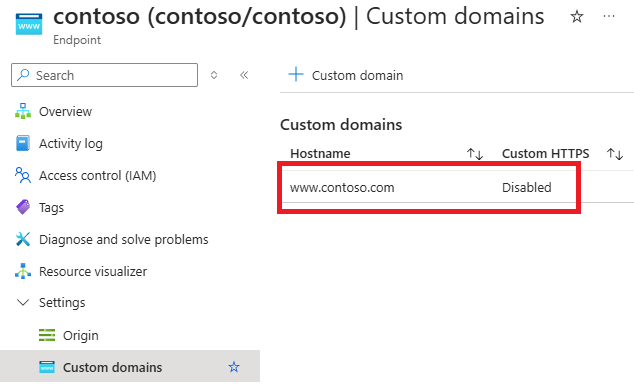
The Custom domain page appears.
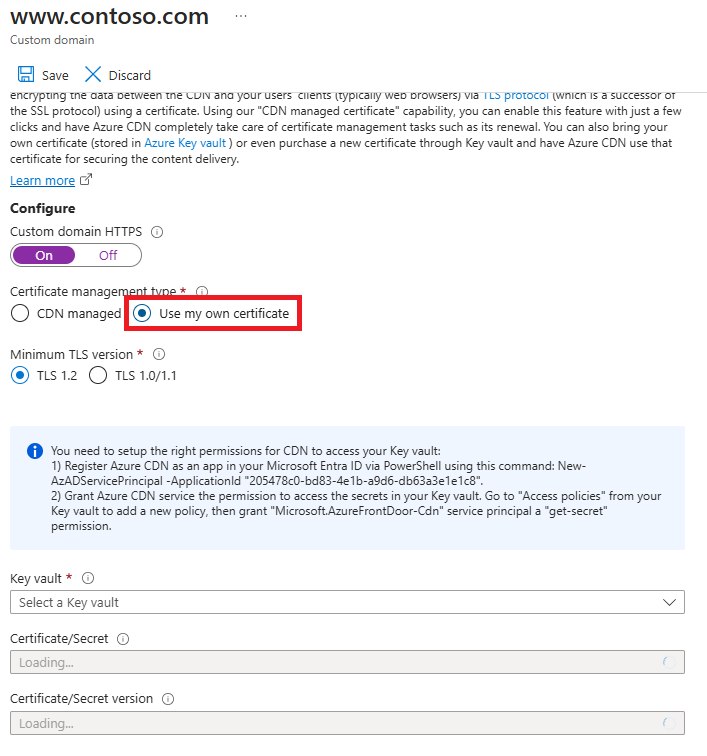
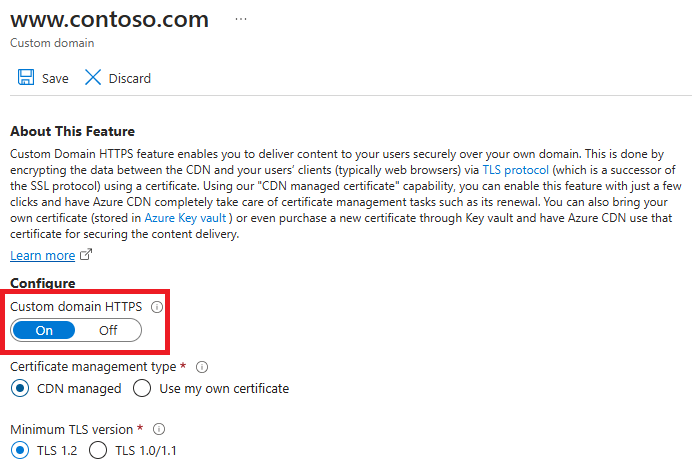
Under Certificate management type, select CDN managed.
Select On to enable HTTPS.
Continue to Validate the domain.
Validate the domain
If you have a custom domain in use mapped to your custom endpoint with a CNAME record or you're using your own certificate, continue to Custom domain mapped to your Content Delivery Network endpoint.
Otherwise, if the CNAME record entry for your endpoint no longer exists or it contains the cdnverify subdomain, continue to Custom domain not mapped to your CDN endpoint.
Custom domain is mapped to your CDN endpoint by a CNAME record
When you added a custom domain to your endpoint, you created a CNAME record in the DNS domain registrar mapped to your CDN endpoint hostname.
If that CNAME record still exists and doesn't contain the cdnverify subdomain, the DigiCert CA uses it to automatically validate ownership of your custom domain.
If you're using your own certificate, domain validation isn't required.
Your CNAME record should be in the following format:
- Name is your custom domain name.
- Value is your content delivery network endpoint hostname.
| Name | Type | Value |
|---|---|---|
| <www.contoso.com> | CNAME | contoso.azureedge.net |
For more information about CNAME records, see Create the CNAME DNS record.
If your CNAME record is in the correct format, DigiCert automatically verifies your custom domain name and creates a certificate for your domain. DigitCert doesn't send you a verification email and you don't need to approve your request. The certificate is valid for one year and will be autorenewed before it expires. Continue to Wait for propagation.
Automatic validation typically takes a few hours. If you don't see your domain validated in 24 hours, open a support ticket.
Note
If you have a Certificate Authority Authorization (CAA) record with your DNS provider, it must include the appropriate CAs for authorization. DigiCert is the CA for Microsoft and Edgio profiles. For information about managing CAA records, see Manage CAA records. For a CAA record tool, see CAA Record Helper.
Custom domain isn't mapped to your CDN endpoint
If the CNAME record entry contains the cdnverify subdomain, follow the rest of the instructions in this step.
DigiCert sends a verification email to the following email addresses. Verify that you can approve directly from one of the following addresses:
- admin@your-domain-name.com
- administrator@your-domain-name.com
- webmaster@your-domain-name.com
- hostmaster@your-domain-name.com
- postmaster@your-domain-name.com
You should receive an email in a few minutes for you to approve the request. In case you're using a spam filter, add verification@digicert.com to its allowlist. If you don't receive an email within 24 hours, contact Microsoft support.
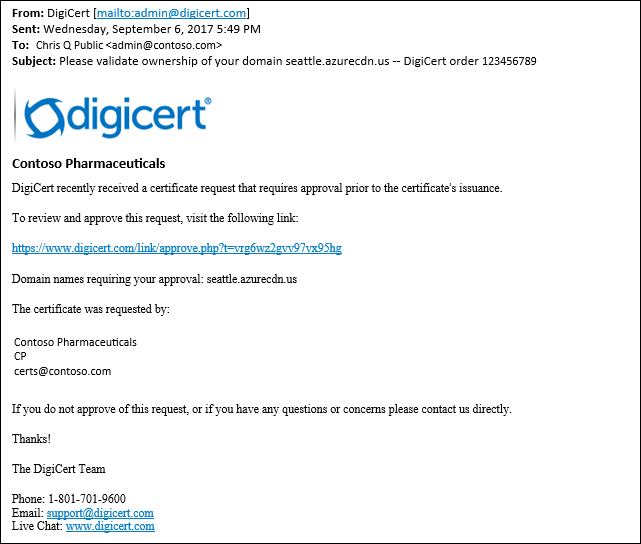
When you select the approval link, you're directed to the following online approval form:

Follow the instructions on the form; you have two verification options:
You can approve all future orders placed through the same account for the same root domain; for example, contoso.com. This approach is recommended if you plan to add other custom domains for the same root domain.
You can approve just the specific host name used in this request. Another approval is required for later requests.
After approval, DigiCert completes the certificate creation for your custom domain name. The certificate is valid for one year. If the CNAME record for your custom domain is added or updated to map to your endpoint hostname after verification, then it will be autorenewed before it's expired.
Note
Managed certificate autorenewal requires that your custom domain be directly mapped to your CDN endpoint by a CNAME record.
Wait for propagation
After the domain name is validated, it can take up to 6-8 hours for the custom domain HTTPS feature to be activated. When the process completes, the custom HTTPS status in the Azure portal is changed to Enabled. The four operation steps in the custom domain dialog are marked as complete. Your custom domain is now ready to use HTTPS.
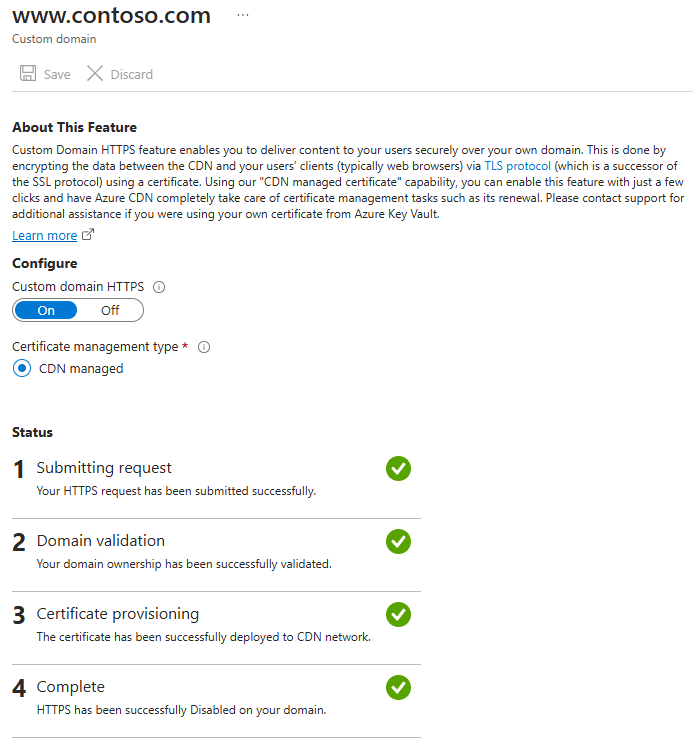
Operation progress
The following table shows the operation progress that occurs when you enable HTTPS. After you enable HTTPS, four operation steps appear in the custom domain dialog. As each step becomes active, other substep details appear under the step as it progresses. Not all of these substeps occur. After a step successfully completes, a green check mark appears next to it.
| Operation step | Operation substep details |
|---|---|
| 1 Submitting request | Submitting request |
| Your HTTPS request is being submitted. | |
| Your HTTPS request has been submitted successfully. | |
| 2 Domain validation | Domain is automatically validated if it's CNAME mapped to the CDN Endpoint. Otherwise, a verification request is sent to the email listed in your domain's registration record (WHOIS registrant). |
| Your domain ownership has been successfully validated. | |
| Domain ownership validation request expired (customer likely didn't respond within 6 days). HTTPS won't be enabled on your domain. * | |
| Domain ownership validation request was rejected by the customer. HTTPS won't be enabled on your domain. * | |
| 3 Certificate provisioning | The certificate authority is currently issuing the certificate needed to enable HTTPS on your domain. |
| The certificate has been issued and is currently being deployed to CDN network. This could take up to 6 hours. | |
| The certificate has been successfully deployed to CDN network. | |
| 4 Complete | HTTPS has been successfully enabled on your domain. |
* This message doesn't appear unless an error has occurred.
If an error occurs before the request is submitted, the following error message is displayed:
We encountered an unexpected error while processing your HTTPS request. Please try again and contact support if the issue persists.
Clean up resources - disable HTTPS
In this section, you learn how to disable HTTPS for your custom domain.
Disable the HTTPS feature
In the Azure portal, search for and select CDN profiles.
Choose your Azure CDN Standard from Microsoft, Azure CDN Standard from Edgio, or Azure CDN Premium from Edgio profile.
In the list of endpoints, pick the endpoint containing your custom domain.
Choose the custom domain for which you want to disable HTTPS.
Choose Off to disable HTTPS, then select Apply.
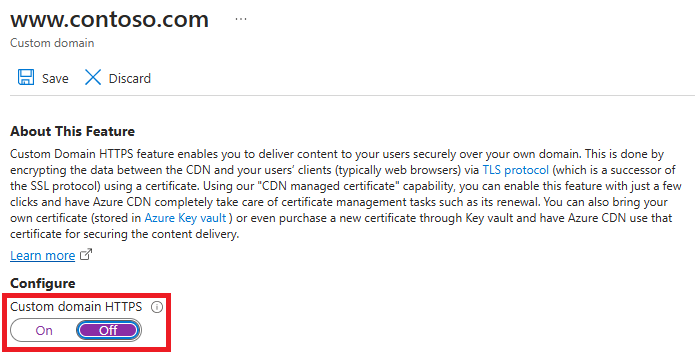
Wait for propagation
After the custom domain HTTPS feature is disabled, it can take up to 6-8 hours for it to take effect. When the process is complete, the custom HTTPS status in the Azure portal is changed to Disabled. Your custom domain can no longer use HTTPS.
Frequently asked questions
Who is the certificate provider and what type of certificate is used?
A dedicated certificate provided by Digicert is used for your custom domain for:
- Azure Content Delivery Network from Edgio
- Azure Content Delivery Network from Microsoft
Do you use IP-based or Server Name Indication (SNI) TLS/SSL?
Both Azure CDN from Edgio and Azure CDN Standard from Microsoft use SNI TLS/SSL.
What if I don't receive the domain verification email from DigiCert?
If you aren't using the cdnverify subdomain and your CNAME entry is for your endpoint hostname, you won't receive a domain verification email.
Validation occurs automatically. Otherwise, if you don't have a CNAME entry and you haven't received an email within 24 hours, contact Microsoft support.
Is using a SAN certificate less secure than a dedicated certificate?
A SAN certificate follows the same encryption and security standards as a dedicated certificate. All issued TLS/SSL certificates use SHA-256 for enhanced server security.
Do I need a Certificate Authority Authorization record with my DNS provider?
Certificate Authority Authorization record isn't currently required. However, if you do have one, it must include DigiCert as a valid CA.
On June 20, 2018, Azure CDN from Edgio started using a dedicated certificate with SNI TLS/SSL by default. What happens to my existing custom domains using Subject Alternative Names (SAN) certificate and IP-based TLS/SSL?
Your existing domains are gradually migrated to single certificate in the upcoming months if Microsoft analyzes that only SNI client requests are made to your application.
If non-SNI clients are detected, your domains stay in the SAN certificate with IP-based TLS/SSL. Requests to your service or clients that are non-SNI, are unaffected.
How do cert renewals work with Bring Your Own Certificate?
To ensure a newer certificate is deployed to POP infrastructure, upload your new certificate to Azure Key Vault. In your TLS settings on Azure Content Delivery Network, choose the newest certificate version and select save. Azure Content Delivery Network will then propagate your new updated cert.
Important
- As of June 20, 2024, Azure CDN Standard and Premium from Edgio won't support the Use my own certificates feature. This feature will be reintroduced again in early 2025.
- What are the required actions for custom domains using this feature? BYOC certificates already deployed on the Edgio platform will remain valid until its expiration date. No action is required for certificates expiring in 2025. We encourage you to switch over to CDN Managed for certificates requiring an update or will be expiring this year. If you're requiring additional assistance, submit a support request to work with a support engineer.
Next steps
In this tutorial, you learned how to:
- Enable the HTTPS protocol on your custom domain.
- Use a CDN-managed certificate
- Use your own certificate
- Validate the domain.
- Disable the HTTPS protocol on your custom domain.
Advance to the next tutorial to learn how to configure caching on your CDN endpoint.