Hi @Denis Dal Molin ,
Welcome to the Microsoft Q&A Platform. Thank you for reaching out & I hope you are doing well.
I understand that you would like to understand more about packet routing feature of Azure Firewall.
Azure Firewall, can indeed do packet routing, just like any other NVA.
You can consider the "Block/allow" action of Azure Firewall something like NSG and not UDR.
This means, Azure Firewall will always learn the routes of Spoke VNets and OnPremises' address ranges (just like any other VM in the Hub Vnet would).
As long as there is an allow rule for Spoke VNets' traffic, packets are not dropped and routed accordingly.
P.S : You can use the above behavior of Azure Firewall to achieve transit routing between two Spoke VNets.
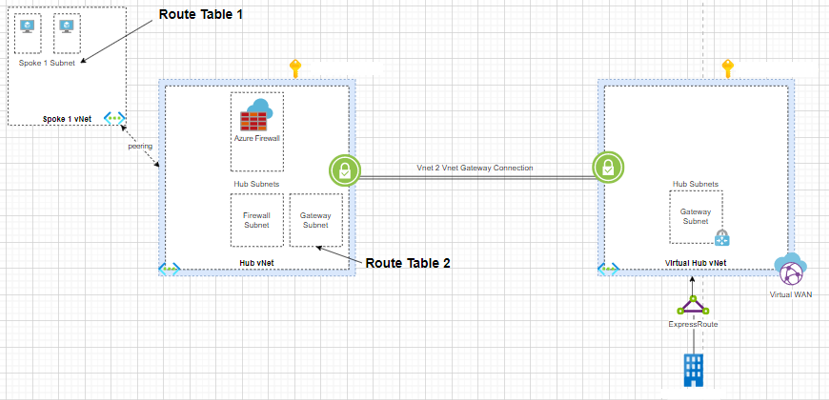
Now, in your case, with UDR
Consider a VM in Spoke (Left)
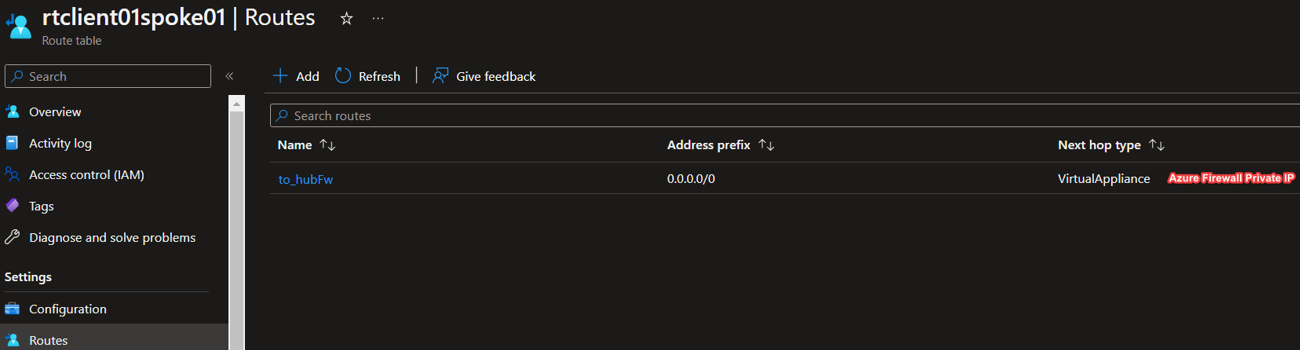
- You have a route table with 0.0.0.0/0 --------> Azure Firewall with Propagate Gateway routes disabled.
- So, any traffic (other than that destined to Hub) will go to the Firewall
- Now, there is no route table in Firewall
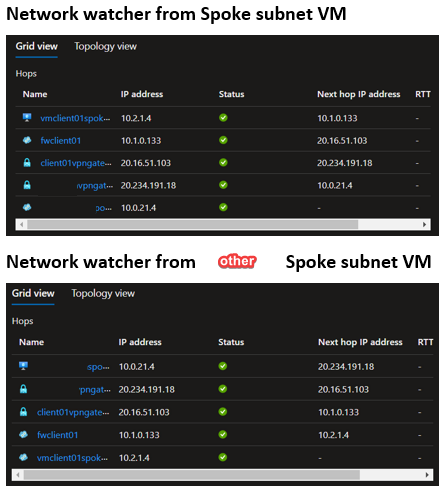
- So, Firewall would know that next hop as Gateway
- And from Gateway, the packet goes via Vnet-to-Vnet connection
Consider a VM in Spoke/Hub (Right)
- Any traffic destined to left goes via vHub.
- And from vHub, the packet goes via Vnet-to-Vnet connection and reached the Gateway to the left
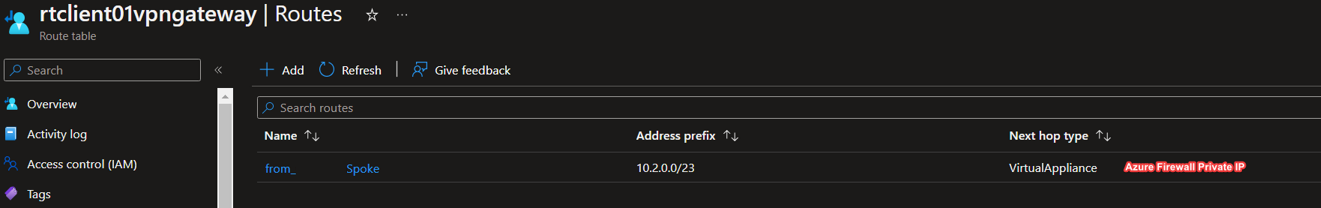
- You have a route table with Left VNets (10.2.0.0/23) --------> Azure Firewall with Propagate Gateway routes disabled.
- So, any traffic destined to 10.2.0.0/23 will go to the Firewall
- Now, there is no route table in Firewall
- So, Firewall would know that next hop Spoke VNet by "default routes" learnt from Peering.
Without UDR
- Both To and Fro traffic would skip the Azure Firewall if you do not have a route table in Spoke VNet and Gateway Subnet
- But traffic is still allowed
I hope this helps.
In case my understanding of your question is incorrect, please do let me know and I shall try to address your concern.
Cheers,
Kapil
----------------------------------------------------------------------------------------------------------------
Please don’t forget to close the thread by clicking "Accept the answer" wherever the information provided helps you, as this can be beneficial to other community members.