It is a clock skew. CA adds it to all signed stuff, such as certificates and CRLs to allow clocks between enrollment client and CA server to be out of sync for a bit: +/- 5mins. 5 mins is not a random value, it is derived from Kerberos threshold. The behavior you are observing is expected, correct and by design. You should not do anything with it.
Windows 2019 Certificate Authority is adding 10 minutes to my Certificate Expiration Date
Here's one for the ages. I built a new subCA from a base Server 2019 build. I have done this several times in the past. I issued it a 10year cert from the RootCA. So far everything is good. I configured certificates to be valid for two years. Now when we request certificates using the default IPSec (Offline request) template it issues certificates for 2yrs and 10 minutes. It's driving me nuts. I currently have a case open with Microsoft and they have no idea what it is.
Anyone that can help me figure this out? I've hit a wall. I have exhausted all my avenues and apparently Microsoft's...
Thanks,
Chris
1 additional answer
Sort by: Most helpful
-
Chris Krikorian 21 Reputation points
2020-09-23T04:32:33.653+00:00 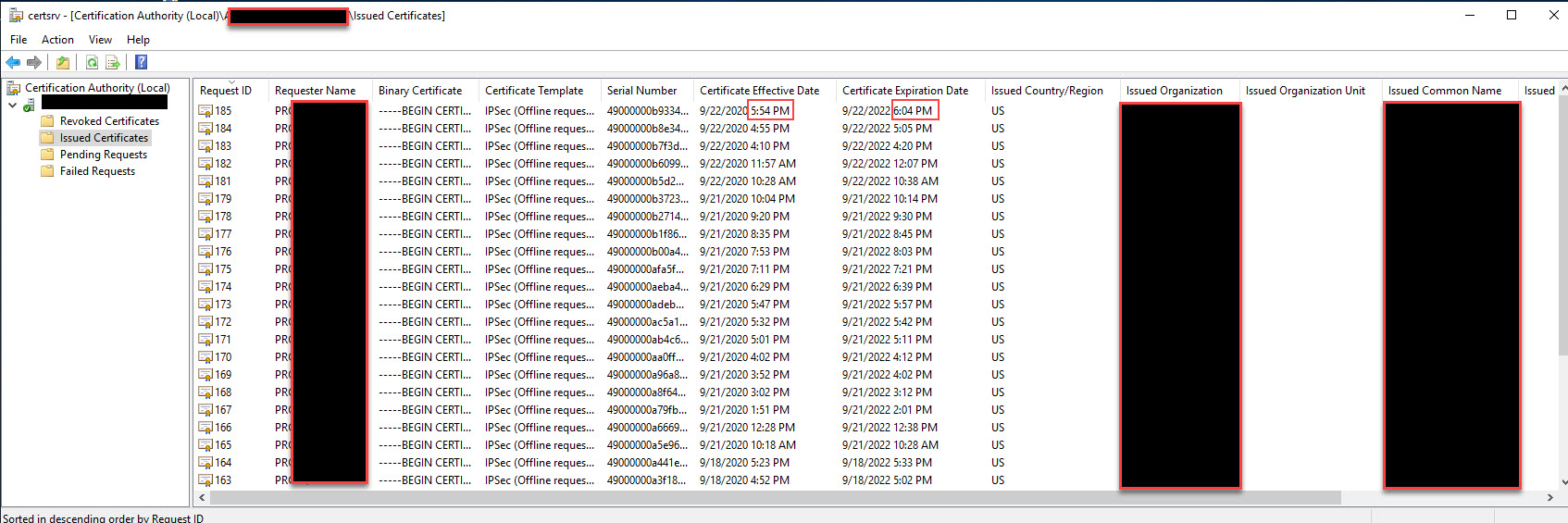
10 minutes added mysteriously ¯_(ツ)_/¯

