SMB over QUIC in Windows Server 2022 Datacenter: Azure Edition looks interesting.
The description at...
https://video2.skills-academy.com/en-us/windows-server/storage/file-server/smb-over-quic
...is a good starting point. But no more!
I can't find any detail about how networking would be handled!
I get that you would use split DNS, so the server name resolves differently internally and on the Internet.
Would you attach an interface with the server's public IPv4 address, and another interface with the server's internal IPv4 address?
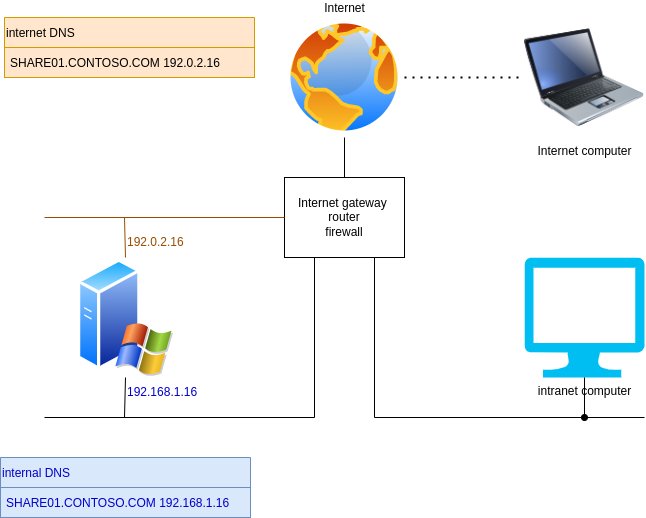
Would you simply NAT on your Internet router?
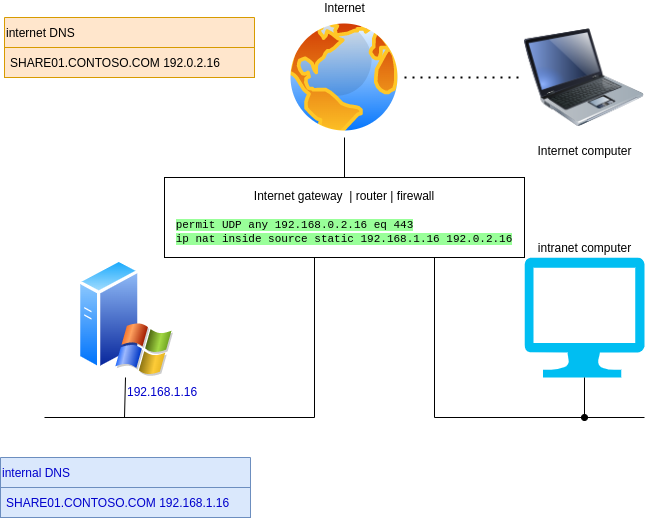
Neither feels "right" in contemporary networking; typically, we use pre-authentication from the Internet (eg using Azure Application Proxy). SMB was never designed for pre-authentication, or "modern authentication".
So I'm unsure how it's meant to work.
It used to be that publishing an SMB file server to the Internet (445/TCP) was simply wrong. This seems like publishing a SMB file server to the Internet over 443/UDP with no pre-authentication. Doesn't seem all that different to me.
Ned Pyle described it as file sharing without VPN (https://techcommunity.microsoft.com/t5/itops-talk-blog/smb-over-quic-files-without-the-vpn/ba-p/1183449).
But this looks like you would put a file server in Azure, enable SMB over QUIC, then configure Azure network to permit access only from your on premises network. That works fine, of course, that doesn't accommodate mobile users.
Eliminating the VPN for mobile users scenario;
- people using their Windows 11 laptop on the organisational network accessing SMB directly to the internal IPv4 address
- take their device home and continuing their work, but the device seamlessly connects over QUIC instead
is the key use case.

