We have deployed Arc agents to 12 Linux hosts using the script for multiple hosts with a service principle method. The agent has installed and because the subscription has Defender for Cloud enabled the MDE agent has installed. We see the agent connected with consistent heartbeat entries in the LA workspace and Defender for Endpoint events are being fed into the workspace.
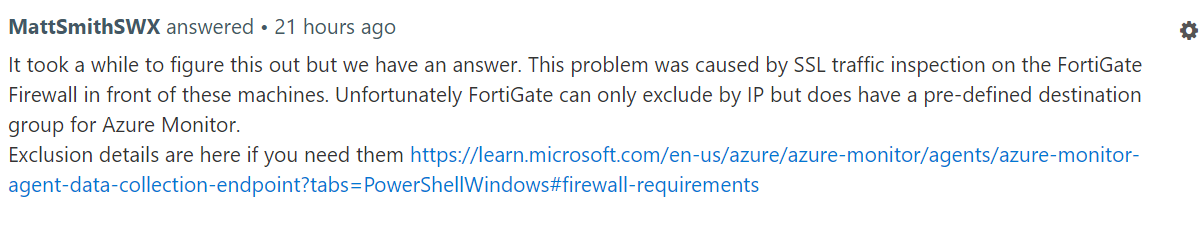
When adding a data collection rule for syslog the data is retrieved to log analytics however the sst files are backing up in /var/opt/microsoft/azuremonitoragent/events/ as if the connection is failing. The mdsd.warn log has these two entries repeated over and over...
2022-11-15T16:11:04.2607920Z: [/source/external/GenevaMonAgent-Shared-CrossPlat/src/XPlatLib/src/MSIToken.cpp:159,GetAzureMSIResponseUsingDefault]Exception occurred [Request canceled by user.] when calling Azure IMDS for MSI token with default identity. URI [/metadata/identity/oauth2/token?api-version=2018-02-01&resource=https://monitor.azure.com/] ErrorCode:-2146041343
2022-11-15T16:11:04.2608200Z: [/source/external/GenevaMonAgent-Shared-CrossPlat/src/XPlatLib/src/MSIToken.cpp:159,GetAzureMSIResponseUsingDefault]Exception occurred [Request canceled by user.] when calling Azure IMDS for MSI token with default identity. URI [/metadata/identity/oauth2/token?api-version=2018-02-01&resource=https://ingestion.monitor.azure.com/] ErrorCode:-2146041343
Is anyone else having this issue or know of a reason?