In theory we can build such rules. But in practice there are several challenges...
The user doesn't exist on the other side. So we can't use the DN (distinguishedName) of the user but we need to build the Foreign Security Principal DN from the user's SID. For example the DN should be something like:
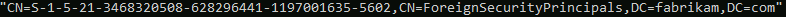
and not
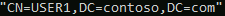
Not a big deal I know but that matters.
Then the 1.2.840.113556.1.4.1941 operator will need the group DN not the user's DN as in your scenario it is not the user member of the group in the other forest but one of its group it is a member of. So you would have to enumerate all the users' groups, get their SIDs, craft the Foreign Security Principal DN and then send the LDAP queries (one for each group) with the aforementioned operator. We could do some filtering if not all the groups have to be considered in you know in advance which groups should be queried on the other side. Or, you could use the operator with the user's Foreign Security Principal DN if the user were to be a direct member of the groups in the trusted forest. Then you need only one query.
And finally, the biggest issue in my opinion, is still about the operator 1.2.840.113556.1.4.1941. It is EXTERMLY inefficient and greedy. In large environments (i.e. an environment with a lot of objects) such an operator can bring DCs to 100% CPU for few seconds (minutes) and take a very long time to get done (could be minutes too), which is not only a terrible user experience (the browser is idled on the user's side) and you impact all applications using domain controllers if you hit one of these perf issues.
So even if we can make it work, it would not scale.
