@ankit kumar Let me explain how this roles works and the define of the RBAC.
Only roles explicitly defined for data access permit a security principal to access blob or queue data. Roles such as Owner, Contributor, and Storage Account Contributor permit a security principal to manage a storage account, but do not provide access to the blob or queue data within that account.
Access to blob or queue data in the Azure portal can be authorized using either your Azure AD account or the storage account access key. For more information, see Use the Azure portal to access blob or queue data.
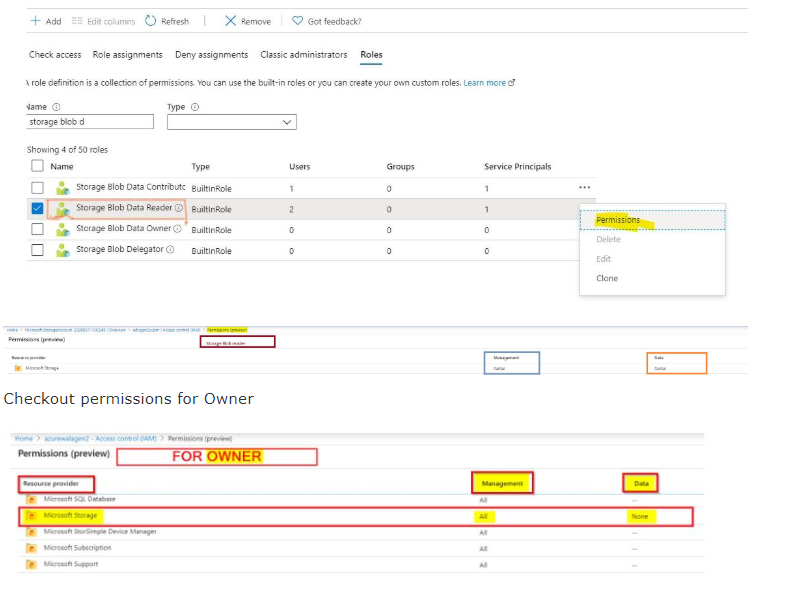
Only roles explicitly defined for data access permit a security principal to access blob or queue data. Roles such as Owner, Contributor, and Storage Account Contributor permit a security principal to manage a storage account, but do not provide access to the blob or queue data within that account.
You can grant the right to create a user delegation key separately from right to the data.
https://video2.skills-academy.com/en-us/rest/api/storageservices/get-user-delegation-key is performed at the account level, so you must give this permission with something like the Storage Blob Delegator built-in role at the scope of the storage account.
The User Delegation Token can then be generated to grant a subset of the users permissions for a limited time, and can be granted for an entire blob container OR for individual blobs.
Based on the error message you can refer to Troubleshoot Azure RBAC.
Please look into the article Add or remove role assignments using Azure RBAC and the Azure portal
As per this article video2.skills-academy.com/en-us/rest/api/storageservices/… Get Blob should just require read contributor permissions
Data operations example: https://video2.skills-academy.com/en-us/azure/role-based-access-control/role-definitions#data-operations-example
Please refer to this GitHub thread on Clarity on Reader role
If the issue still persists, Try using Azure Storage Explorer to grant portal access to blobs/queues to a user, you need to also assign them the Azure Resource Manager Reader role. That will give them the permissions they need to navigate through the portal to view blob and queue resources.
Hope this helps!
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------------
Please don’t forget to "Accept the answer” and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.
