Hello,
Thank you so much for posting here.
Frankly speaking, I am not professional with this issue. I tried to research for some information but failed. Hope someone could share their knowledge or experience here.
Crypt32 asked how we created the first cross-certificate. We could reply to this question.
As per my understanding, when duplicating the template, such as Kerberos authentication, the certificate purposes are determined.
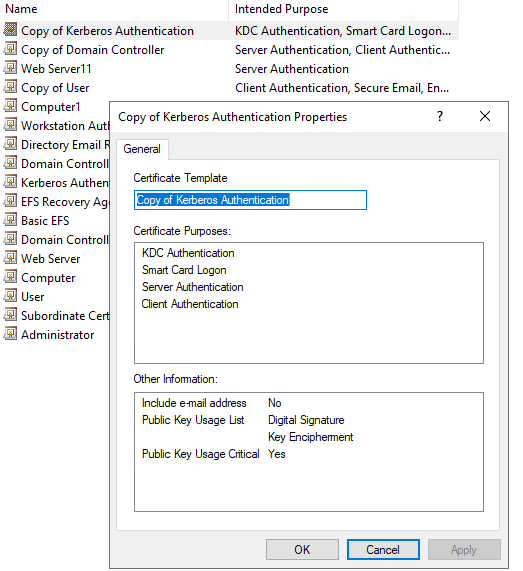
Then the servers could request this certificate. When viewing the requested certificate, we could check the Enhanced Key Usage under Details tag of the Certificate.
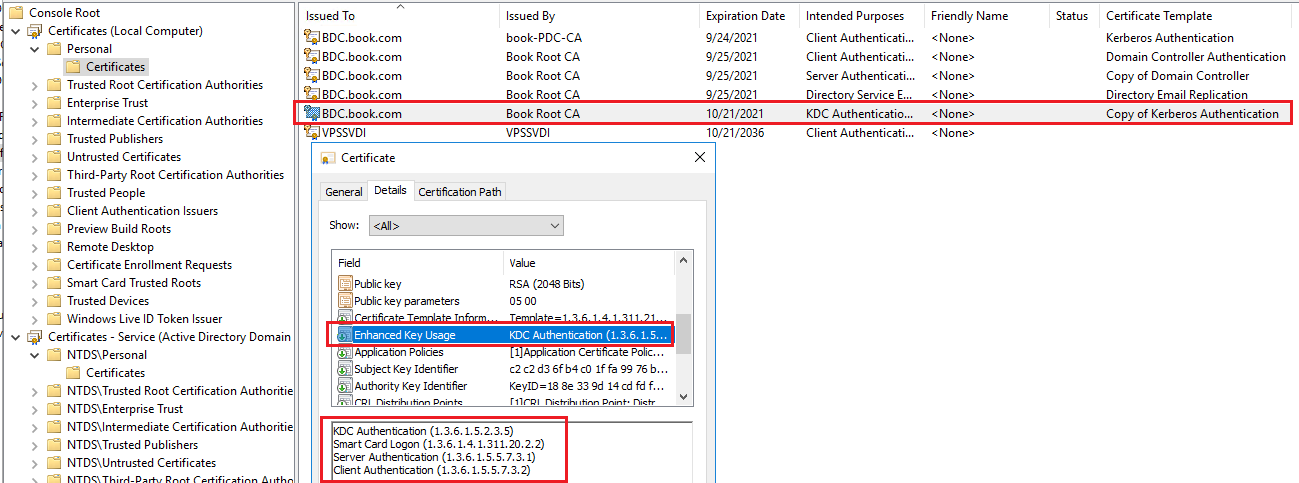
Thank you so much for your understanding and support.
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
