Thank you for posting your query on Microsoft Q&A, from above description I could understand that you have following queries:
- Logging onto test machine with windows hello pin prompts you for credentials when accessing SMB share.
- Conditional access policy to require MFA to access the SMB share is ignored by global secure access.
Please do correct me for any discrepancies by responding in the comments section.
PFB answers inline:
- Logging onto test machine with windows hello pin prompts you for credentials when accessing SMB share.
This could be due to On-prem SMB shares being configured with Kerberos authentication, and windows hello is not configured with cloud Kerberos trust
You may validate this with event logs on you device by accessing User Device Registration admin log under Applications and Services Logs > Microsoft > Windows.
The cloud Kerberos trust prerequisite check isn't done on Microsoft Entra joined devices. If Microsoft Entra Kerberos isn't provisioned, a user on a Microsoft Entra joined device will still be able to sign in, but won't have SSO to on-premises resources secured by Active Directory.
- Conditional access policy configured to prompt for MFA while accessing the SMB share is ignored by global secure access.
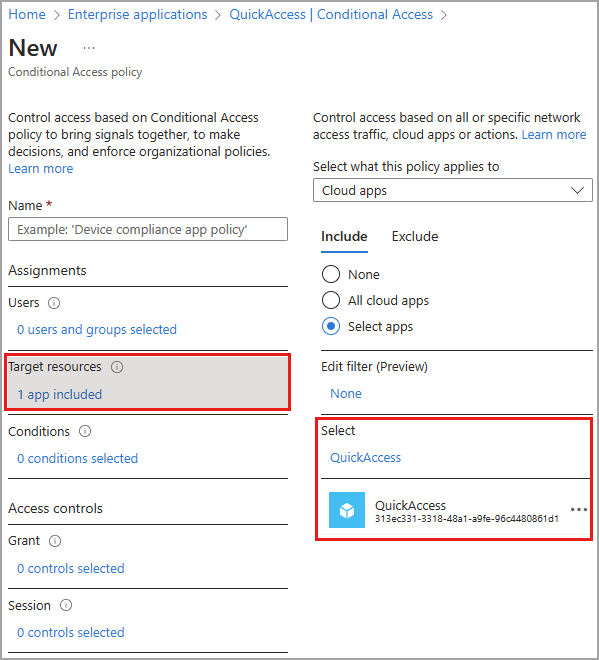
This could have been because of known limitation for private access traffic, according to which:
"Applying Conditional Access policies to Private Access traffic is not currently supported. To model this behavior, you can apply a Conditional Access policy at the application level for Quick Access and Global Secure Access apps. For more information, see Apply Conditional Access to Private Access apps."
However, if above mentioned is not the case, then kindly share the sign in logs with CA evaluation information by eliminating the PII say username, UPN or tenant id.
Please "Accept the answer", "Upvote" and rate your experience. This will help us and others in the community as well. Thanks, Akshay Kaushik


 Thanks,
Akshay Kaushik
Thanks,
Akshay Kaushik