I am unable to create a private endpoint for my postgres SQL flexible server
My bicep file is like this
// Parameters
param location string
//param env string
param nameAffix string
param administratorLogin string
// existing resource name params
param vnetName string
param privateEndpointsSubnetName string
param pgSQLSubnetName string
@description('Virtual Network RuleName')
param virtualNetworkRuleName string = 'AllowSubnet'
@secure()
param administratorLoginPassword string
// Variables
var serverName = 'psql-${nameAffix}-${uniqueString(resourceGroup().id)}'
var pgsqlPrivateEndpointName = 'pep-${serverName}'
var pgsqlDnsZoneName = 'privatelink.postgres.database.azure.com'
var pgsqlDnsGroupName = '${pgsqlPrivateEndpointName}/default'
// ---- Existing resources ----
resource vnet 'Microsoft.Network/virtualNetworks@2022-11-01' existing = {
name: vnetName
resource privateEndpointsSubnet 'subnets' existing = {
name: privateEndpointsSubnetName
}
resource pgSQLSubnet 'subnets' existing = {
name: pgSQLSubnetName
}
}
// Postgres
resource server 'Microsoft.DBforPostgreSQL/flexibleServers@2022-12-01' = {
name: serverName
location: location
sku: {
name: 'Standard_D4ds_v4'
tier: 'GeneralPurpose'
}
properties: {
version: '16'
administratorLogin: administratorLogin
administratorLoginPassword: administratorLoginPassword
network: {
delegatedSubnetResourceId: vnet::pgSQLSubnet.id
privateDnsZoneArmResourceId: pgsqlDnsZone.id
}
highAvailability: {
mode: 'Disabled'
}
storage: {
storageSizeGB: 128
}
backup: {
backupRetentionDays: 7
geoRedundantBackup: 'Disabled'
}
}
resource virtualNetworkRule 'virtualNetworkRules' = {
name: virtualNetworkRuleName
properties: {
virtualNetworkSubnetId: vnet::pgSQLSubnet.id
ignoreMissingVnetServiceEndpoint: true
}
}
}
// private endpoint
resource pgsqlPrivateEndpoint 'Microsoft.Network/privateEndpoints@2022-11-01' = {
name: pgsqlPrivateEndpointName
location: location
properties: {
subnet: {
id: vnet::privateEndpointsSubnet.id
}
privateLinkServiceConnections: [
{
name: pgsqlPrivateEndpointName
properties: {
privateLinkServiceId: server.id
groupIds: [
'postgresqlServer'
]
}
}
]
}
}
resource pgsqlDnsZone 'Microsoft.Network/privateDnsZones@2020-06-01' = {
name: pgsqlDnsZoneName
location: 'global'
properties: {}
}
resource psqlDnsZoneLink 'Microsoft.Network/privateDnsZones/virtualNetworkLinks@2020-06-01' = {
parent: pgsqlDnsZone
name: '${pgsqlDnsZoneName}-link'
location: 'global'
properties: {
registrationEnabled: false
virtualNetwork: {
id: vnet.id
}
}
}
resource pgsqlDnsZoneGroup 'Microsoft.Network/privateEndpoints/privateDnsZoneGroups@2022-11-01' = {
name: pgsqlDnsGroupName
properties: {
privateDnsZoneConfigs: [
{
name: pgsqlDnsZoneName
properties: {
privateDnsZoneId: pgsqlDnsZone.id
}
}
]
}
dependsOn: [
pgsqlPrivateEndpoint
]
}
The error I got from deployment of the bicep above is
The given server xxxxxxxxxxxxxx does not support private endpoint feature. Please create a new server that is private endpoint capable. Refer to https://aka.ms/pgflex-pepreview for more details.
My desired architecture is something similar to this
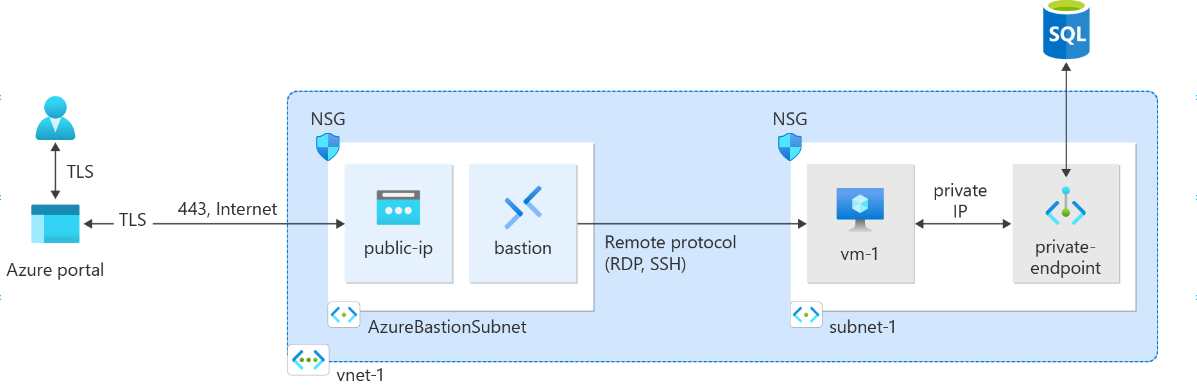
With jumphost in one subnet, app service app in one subnet, private endpoint in one subnet, postgres sql flexible server in one subnet and the jumpost and app service can access the postgres sql flexible server via the private endpoint
Is it feasible on Azure and how to set it up with bicep?
