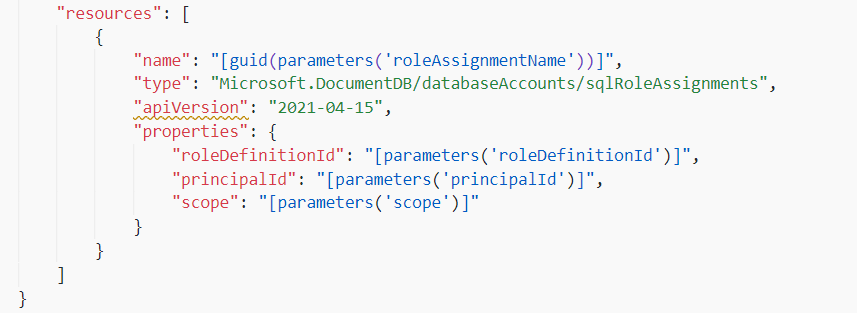
Hi @Marco Papst , for existing role definition, could you please try below template once?
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"databaseAccounts_cosmos_name": {
"defaultValue": "<yourcosmosaccname>",
"type": "String"
},
"accountName": {
"defaultValue": "<yourcosmosaccname>",
"type": "String",
"metadata": { "description": "Cosmos DB account name, max length 44 characters" }
},
"principalId": {
"defaultValue": "<prinicipalId>",
"type": "String",
"metadata": { "description": "Object ID of the AAD identity. Must be a GUID." }
},
"guidValue": {
"type": "string",
"defaultValue": "[newGuid()]"
}
},
"variables": {
"accountName": "[toLower(parameters('accountName'))]",
"roleDefinitionId": "[guid('sql-role-definition-', resourceId('Microsoft.DocumentDB/databaseAccounts', variables('accountName')))]",
"roleAssignmentId": "[guid('sql-role-assignment-', resourceId('Microsoft.DocumentDB/databaseAccounts', variables('accountName')))]",
"unique_string": "[uniqueString(parameters('guidValue'))]"
},
"resources": [
{
"type": "Microsoft.DocumentDB/databaseAccounts/sqlRoleAssignments",
"apiVersion": "2021-05-15",
"name": "[concat(parameters('databaseAccounts_cosmos_name'), '/',guid('newguid', variables('unique_string')))]",
"properties": {
"roleDefinitionId": "[resourceId('Microsoft.DocumentDB/databaseAccounts/sqlRoleDefinitions', parameters('databaseAccounts_cosmos_name'), '00000000-0000-0000-0000-000000000002')]",
"principalId": "parameters('principalId')",
"scope": "[resourceId('Microsoft.DocumentDB/databaseAccounts', parameters('databaseAccounts_cosmos_name'))]"
}
}
]
}