Sharing the solution with broader community!
Here is a summary of this case for your reference:
Issue Definition:
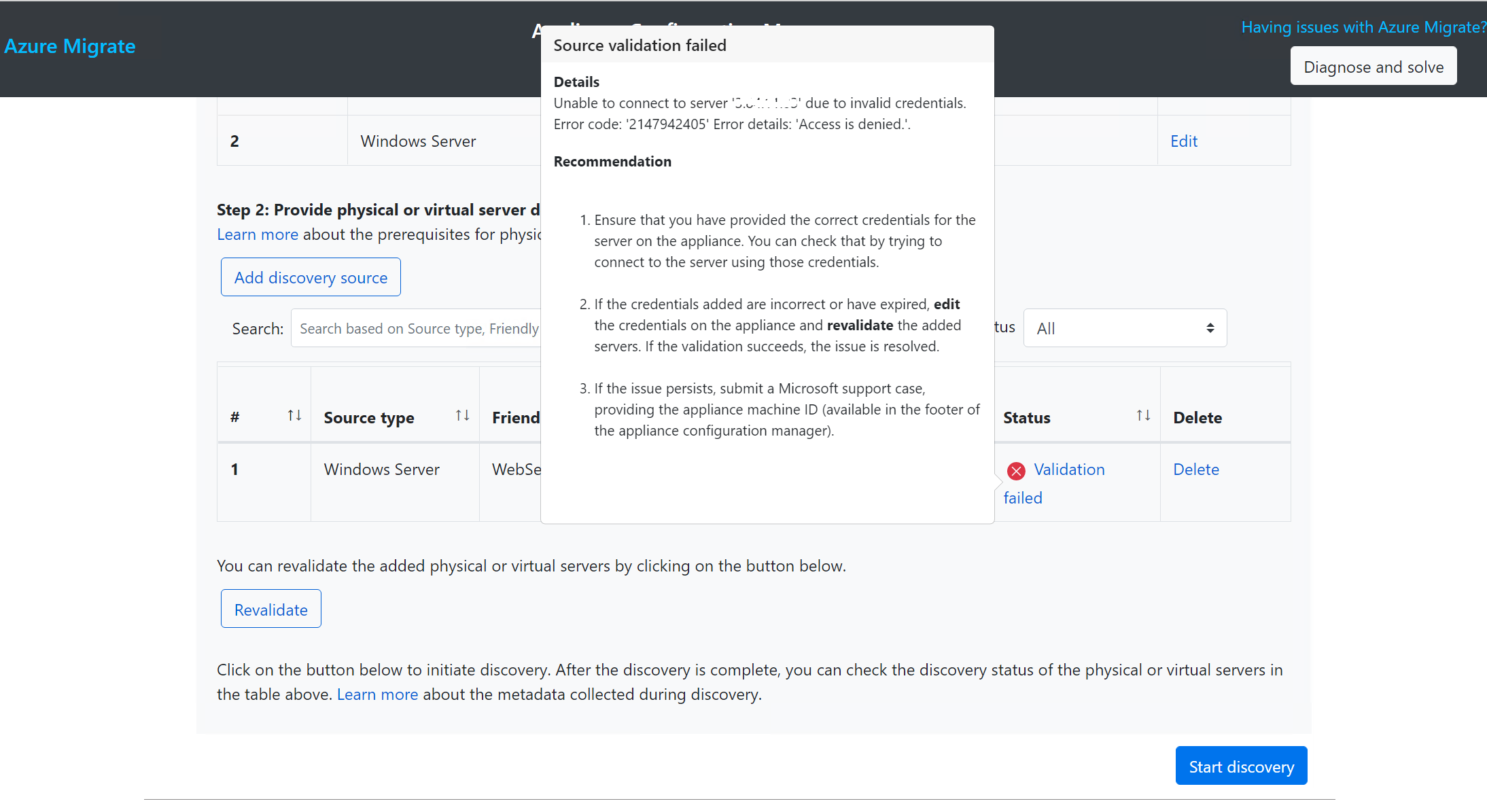
Source validation failed with "Access is denied" when connecting to physical server.
Root Cause Analysis:
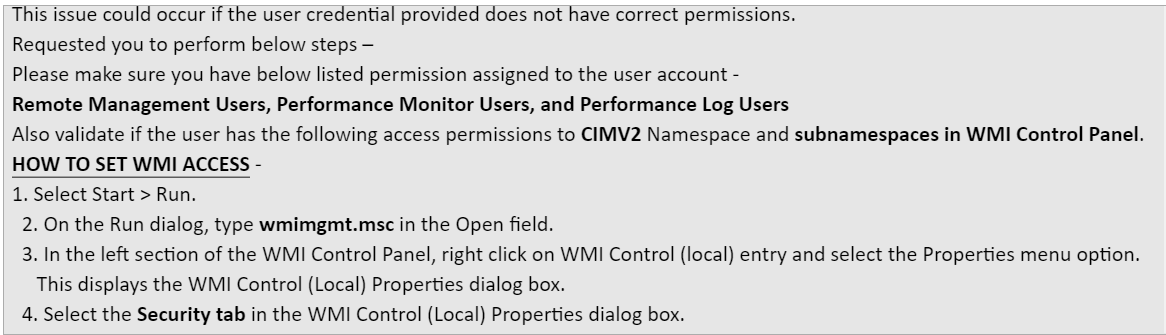
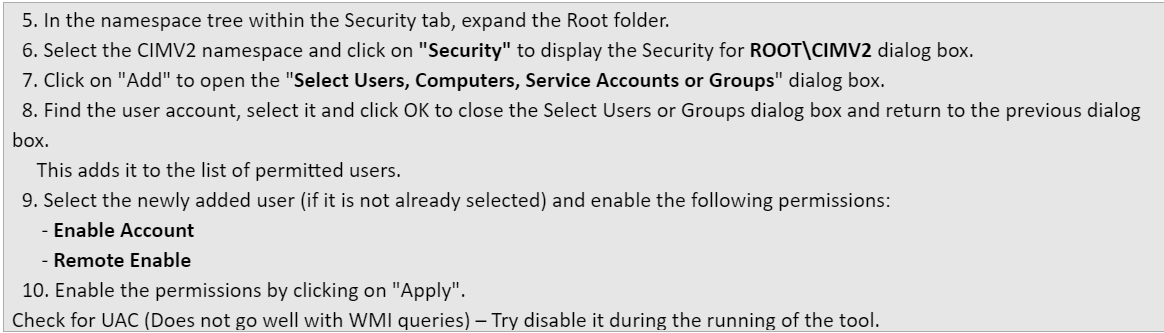
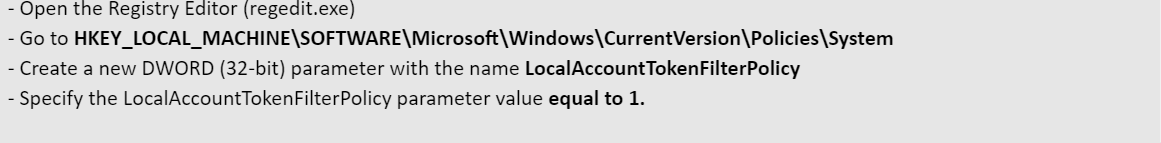
We confirmed the user account has the documented privileges and checked registry for UAC and appliance. Confirmed the WinRM is working fine.
Per testing, we added host name and public IP in hosts, then we can pass the validation by using host name and local host, but still failed validation with public IP.
Discovery completed successfully as expected.
Per investigation by Ipsit, the machines created are configured as default with a private VPC. This would explain the reason why the Public IP failed to validate successfully. The loopback path as verified from nslookup stands correct as it uses a Private IP defined DNS network. Now we had 2 machines A and B:
A trying to connect to A with a public IP address failed since A being part of a private Network was using the local DNS to identify the destination. The local VPC usually does not have global NAT data so the address translation of the public IP to a Private IP fails. The reason for this being public IPs of a machine are assigned and stored by the network provider which in this case is AWS.
In the scenario where B connects to A or A connects to B wherein they are both part of the subnet but created independent of each other. The address translation was possible as B lies outside A’s VPC, so global AWS NAT for that environment was able to get the private IP of A associated public IP of A. Hence the connection from B to A and A to B were successful.
More details can be found in the AWS documentation.
---------------------------------------------------------------------------------------------------------------
If the response helped, do "Accept Answer" and up-vote it.