[Azure Purview] Access Control policy update: Purview artifact permissions managed through Collections
With the recent policy update, as documented here. Permissions for Purview artifacts/assets should be managed through collections, not Access Control (IAM).
Here, for example. We have created this purview account named purview-synapse-account, and a service principal named purview-app-registration.
Now, if we want to update Purview Account assets using the Service Principal, we can go through Purview Studio UI first, give the needed roles for Service Principal as illustrated in the screenshot, and then make REST API calls. Which works as expected.
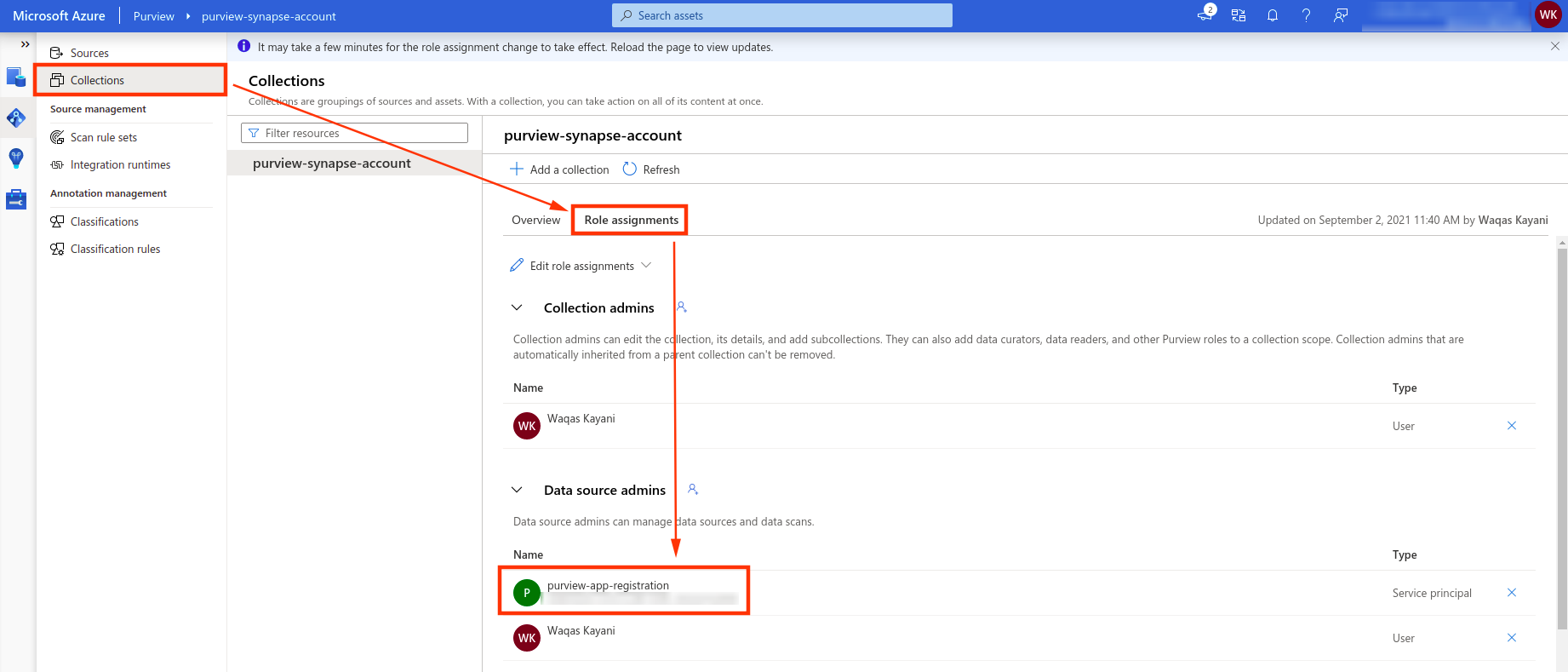
Previously, when a Service Principal was given subscription level permissions, for Purview account, it automatically inherited the IAM permissions, and allowed for the Service Principal to make API calls to add/update assets without any manual steps. With the recent changes, if we want to use REST APIs to make changes, we first have to do this manual step from the Purview Portal.
Is there any possible way, the Role Assignments for Purview Account's Root collection can be modified for an entity (e.g. Service Principal) without the Portal? Either through the APIs or CLI/Powershell.
It would be great to have any ideas/suggestions on this.
Thanks.
