Hello Ant-4544,
Thank you for posting here.
Here are the answers for your references.
Q1: Should I delete the on-premise AD site or will this prevent on-premise clients/users from being able to authenticate via the DCs (all now located in Azure)?
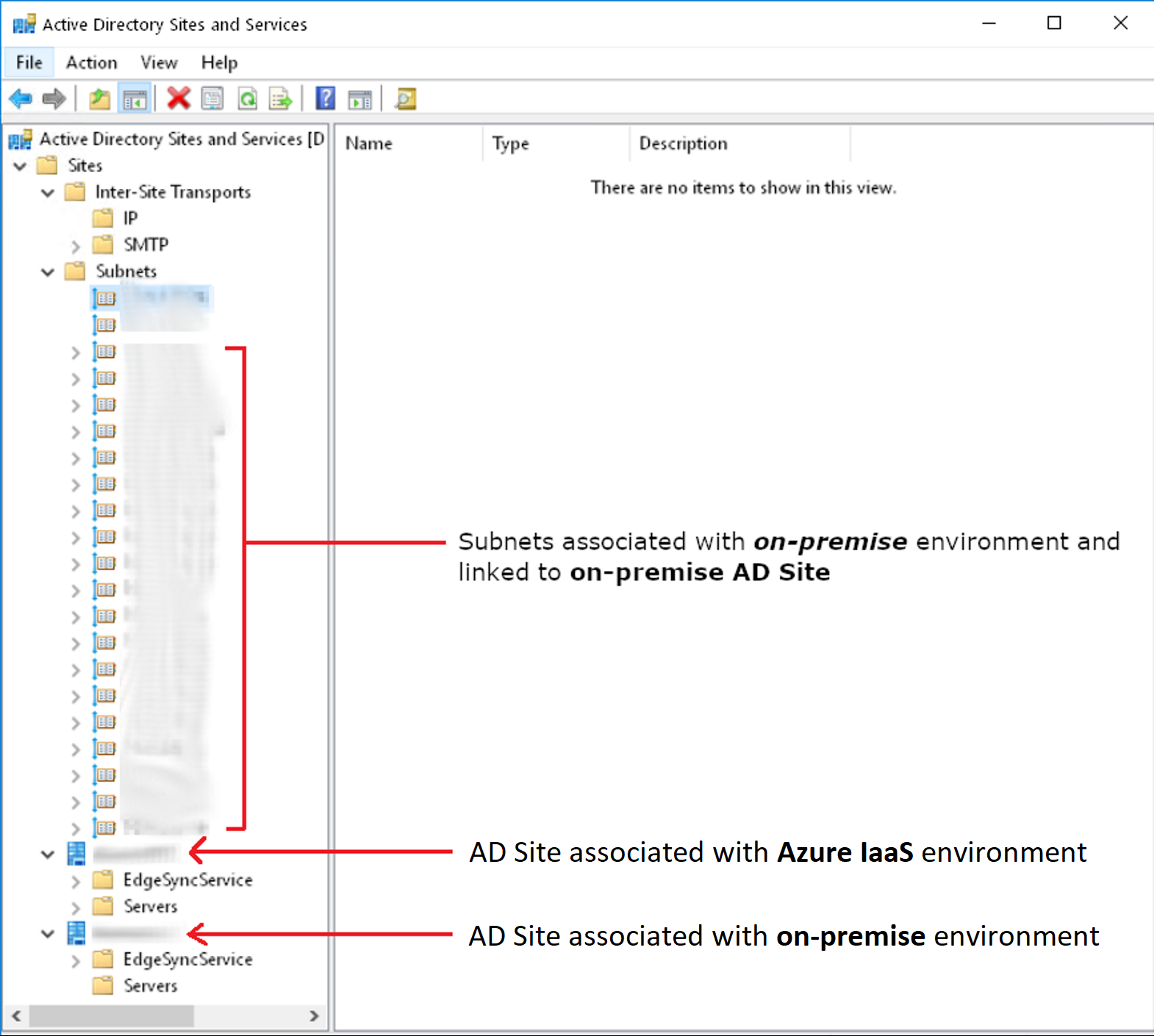
My understanding is that AD Site Subnets exist both to control the flow of AD replication and also to guide clients/users to the closest DCs for authentication.
A1: If we do not need on-premise AD site any longer in the future. We should delete the on-premise AD site.
If we delete on-premise AD site without DCs, it will not prevent on-premise clients/users from being able to authenticate via the DCs.
If you keep the on-premise AD site without DCs, this on-premise AD site will register SRV records using its closest DC information, then clients/users will find their closest DCs to authenticate.
We should delete the on-premise AD site If we do not need it any longer in the future. Before deleting it, we should link those on-premise subnets to the AD site associated with the Azure IaaS environment. Then clients/users will find DCs in Azure IaaS environment to authenticate.
Q2: If I should delete the on-premise AD site, do I first need to link those on-premise subnets to the AD site associated with the Azure IaaS environment
I'm doubtful this is correct given those subnets represent IP ranges that physically exist only within the on-premise environment.
A2: We should delete the on-premise AD site and we should first link those on-premise subnets to the AD site associated with the Azure IaaS environment.
Hope the information is helpful. If you have any questions or concerns, please feel free to let us know.
Best Regards,
Daisy Zhou