@Nisarag Bhatt Welcome to Q&A forums! Great question!
IoT Hub is a shared resource, which means the IoT hub you provision is run on the same set of hardware running other IoT hubs.
IoT Hub was designed under the assumption that devices will constantly be sending telemetry data to the cloud. The goal is to get the data to the cloud first, then process it according to your business needs. We plan our capacity around intended use of the service rather than worst-case peak use (AKA, if all customers were to max out their units at the exact same time).
If we were to allow spikes in usage without any throttling limits, then we are unprotected against usage peaks that would take down the service. Instead of allowing that to happen, we protect the service and our customers by imposing throttling limits. Monitoring the service’s resource usage allows us to better forecast future resource needs and plan accordingly.
We have a temporary cap in place on the number of devices that can be registered to a single hub to protect the service from DoS attacks, but this limit can be increased this through Support.
You can use IoT Hub’s monitoring feature to get all your throttling errors sent to one endpoint. Look for which devices are the chattiest or if your devices are sending at different frequencies, and check whether or not that is expected for your scenario. Goto your Azure IoTHub -> Security to know more about this feature.
IoTHub Service implements throttling and some other limits. Please see: IoT Hub quotas and throttling
To understand more about the security and best practices, please see the below information.
In order to optimize security best practices, it is recommended that a typical IoT architecture is divided into several component/zones as part of the threat modeling exercise.
- Device,
- Field Gateway,
- Cloud gateways, and
- Services.
Zones are broad way to segment a solution; each zone often has its own data and authentication and authorization requirements. Zones can also be used to isolation damage and restrict the impact of low trust zones on higher trust zones.
Each zone is separated by a Trust Boundary, which is noted as the dotted red line in the following diagram. It represents a transition of data/information from one source to another. During this transition, the data/information could be subject to Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service and Elevation of Privilege (STRIDE).
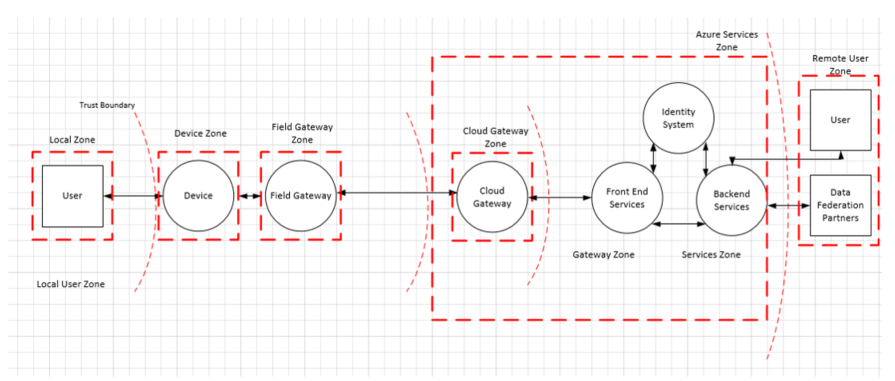
Microsoft uses the framework outlined previously to do threat modeling for Azure IoT. The following section uses the concrete example of Azure IoT Reference Architecture to demonstrate how to think about threat modeling for IoT and how to address the threats identified. This example identifies four main areas of focus:
- Devices and Data Sources,
- Data Transport,
- Device and Event Processing, and
- Presentation
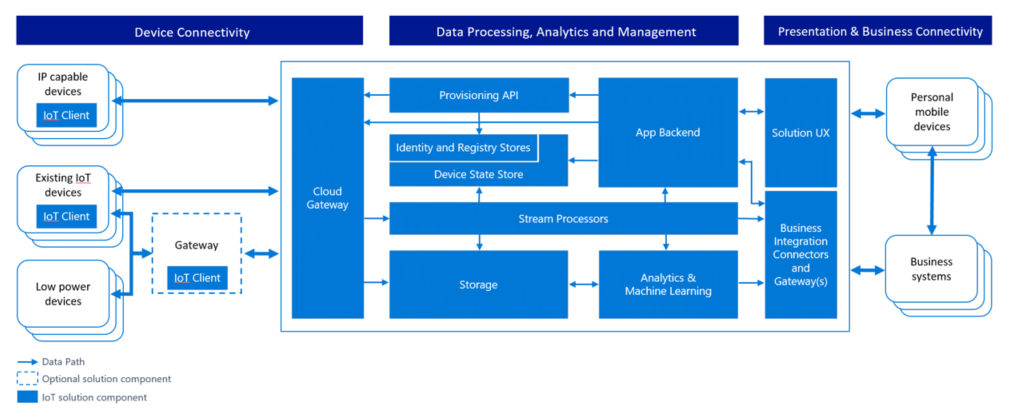
The following diagram provides a simplified view of Microsoft’s IoT Architecture using a Data Flow Diagram model that is used by the Microsoft Threat Modeling Tool:
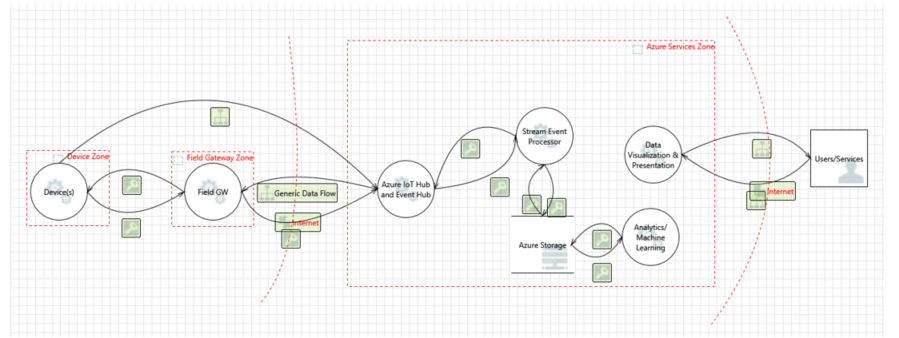
It is important to note that the architecture separates the device and gateway capabilities. This approach enables the user to leverage gateway devices that are more secure: they are capable of communicating with the cloud gateway using secure protocols, which typically requires greater processing overhead that a native device - such as a thermostat - could provide on its own. In the Azure services zone, assume that the Cloud Gateway is represented by the Azure IoT Hub service.
I would suggest you, kindly go through Internet of Things (IoT) security architecture to know more about the security architecture.
Also, please check the below documentations for more details regarding security best practices and handle threats.
Security best practices for Internet of Things (IoT)
Security recommendations for Azure Internet of Things (IoT) deployment
Azure Security Center for IoT frequently asked questions
IoT security—an overview
IoT Hub throttling and you
Do let us know if you have any further queries.