Hello @Badr HOUSSNI ,
If you have two IPs on the same subnet, then the below default NSG rule will come into picture:
AllowVNetInBound
Priority Source Source ports Destination Destination ports Protocol Access
65000 VirtualNetwork 0-65535 VirtualNetwork 0-65535 Any Allow
AllowVnetOutBound
Priority Source Source ports Destination Destination ports Protocol Access
65000 VirtualNetwork 0-65535 VirtualNetwork 0-65535 Any Allow
This means all the VMs within the same subnet connected to a default NSG will be able to talk to each other on all the ports (if open).
However, it's also important to note that security rules in an NSG associated to a subnet can affect connectivity between VM's within it. For example, if a rule is added to the subnet associated NSG which denies all inbound and outbound traffic, VM1 and VM2 will no longer be able to communicate with each other. Another rule would have to be added specifically to allow this.
In your case if you have denied all inbound and outbound traffic on the NSG with high priority rules, then you have to add specific rules to allow communication between the VMs which you would like to connect. So you can use either one of the approaches you have specified above.
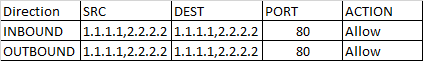
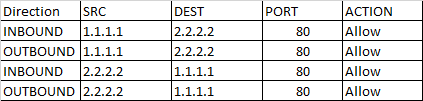
The ability to specify multiple individual IP addresses and ranges in a rule is referred to as augmented security rules.
Please refer : https://video2.skills-academy.com/en-us/azure/virtual-network/security-overview
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please don’t forget to "Accept the answer" wherever the information provided helps you, this can be beneficial to other community members.