
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hello,
I am troubleshooting what appears to be cached credentials on domain joined windows servers and have been unable to solve it for quite some time.
Basically I have allowed users to use their domain account to RDP to certain servers which are joined to AADDS. This is working fine, however, the password policy dictates that users change their passwords every 90 days.
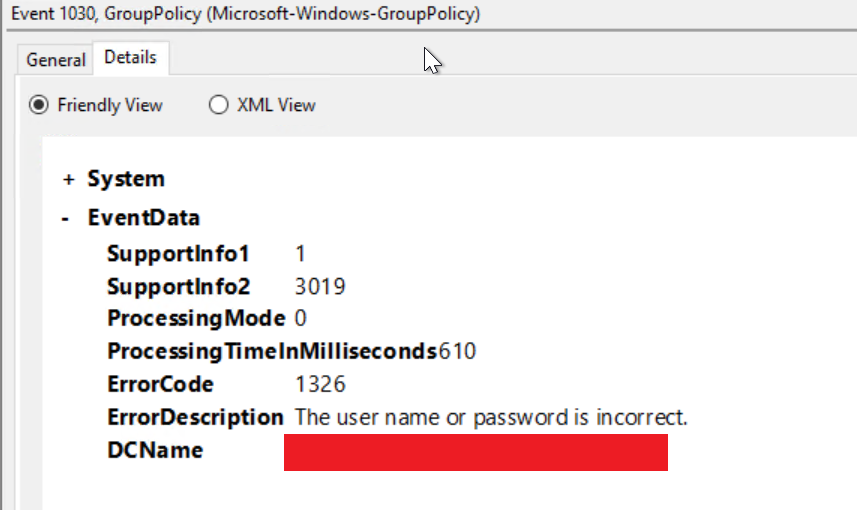
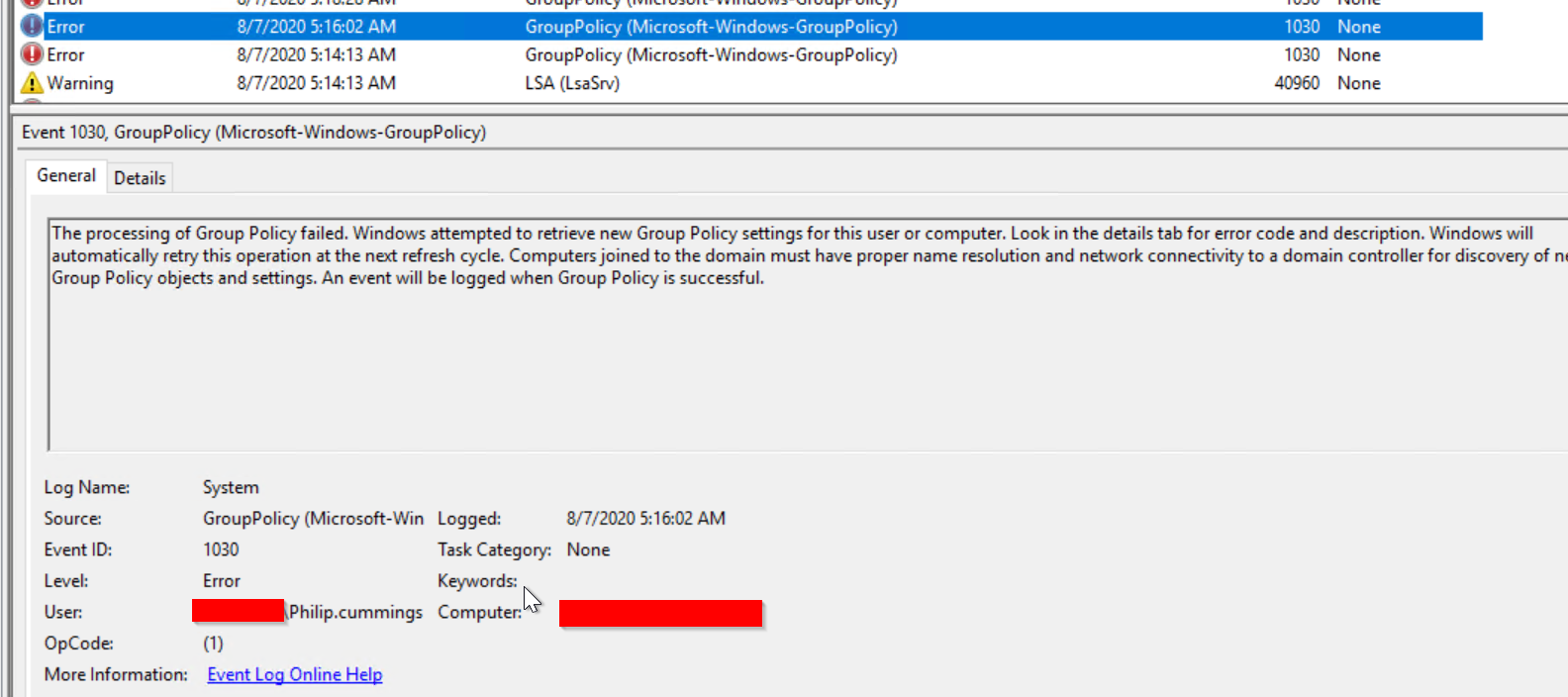
It seems that these domain joined servers are caching the credentials because whenever the users password is changed, the server starts generating event logs for failed group policy retrieval attempts for that specific user. If the user logs back into the server with their updated password, the events stop.
The biggest problem with this, is that the accounts start to lock themselves because of too many failed attempts. Meaning the user cannot log into other LDAP based services.
I hope i have explained it well. I've been working with microsoft for almost a year on this and have yet to find a solution. Please help!
Kind regards,
Philip