Hello @Akhil joy ,
Below is the Self-Signed Process for MQTT Box. and MQTT.fx client
Pre-requisites on Windows Machine: Assuming you have already installed the below tools for this scenario.
**
- OpenSSL
- Powershell
- MQTTBox
- MQTT.fx
**
Let's see MQTT Box with Self-Signed Certificate:
STEP 1: Generate the IoT device's x509 Certificate and the Private Key Certificate by using the below OpenSSL command from a Powershell window.
Open Powershell & navigate to your desired working directory and run the following command.
openssl req -newkey rsa:2048 -nodes -keyout mydevkitkey.pem -x509 -days 365 -out mydevkitcertificate.pem
- mydevkitkey.pem is a the Private Key file
- mydevkitcertificate.pem is the actual x509 certificate file
Sample code is shown below:
PS C:\Users\sabodd> cd C:\Users\sabodd\Documents\AAA\X509SelfSignedCert
PS C:\Users\sabodd\Documents\AAA\X509SelfSignedCert> openssl req -newkey rsa:2048 -nodes -keyout mydevkitkey.pem -x509 -days 365 -out mydevkitcertificate.pem
Generating a 2048 bit RSA private key
.............................+++
writing new private key to 'mydevkitkey.pem'
-----
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:WA
Locality Name (eg, city) []:Redmond
Organization Name (eg, company) [Internet Widgits Pty Ltd]:OTravels
Organizational Unit Name (eg, section) []:.
Common Name (e.g. server FQDN or YOUR name) []:x509SelfSigned
Email Address []:satish@outlook.com
Validate your generated x509 mydevkitcertificate.pem by using the below command. [This step is optional, just to validate our work].
- openssl x509 -text -noout -in mydevkitcertificate.pem
Continue...
STEP 2: Capture the x509 certificate's Fingerprint either SHA1 or SHA256 type.[your choice]
SHA1: Command
openssl x509 -in mydevkitcertificate.pem -fingerprint -noout.
SHA256 : Command
openssl x509 -in mydevkitcertificate.pem -fingerprint -noout -sha256
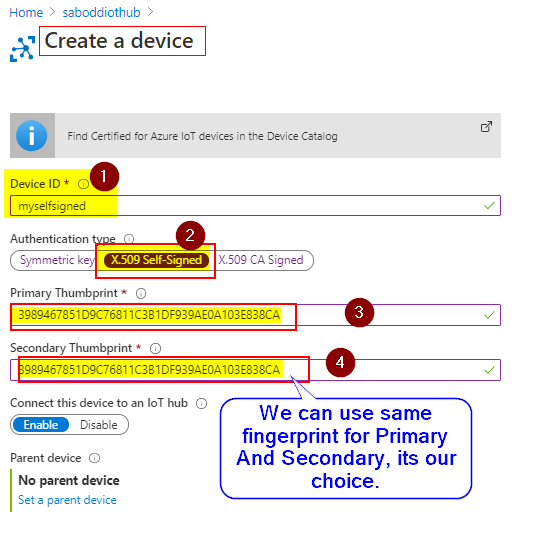
Copy the fingerprint hexadecimal number with 40 length [we used SHA1 type].
Remove the ':' from the fingerprint and it will look as shown below.
3989467851D9C76811C3B1DF939AE0A103E838CA
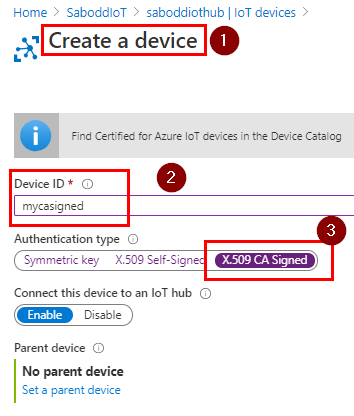
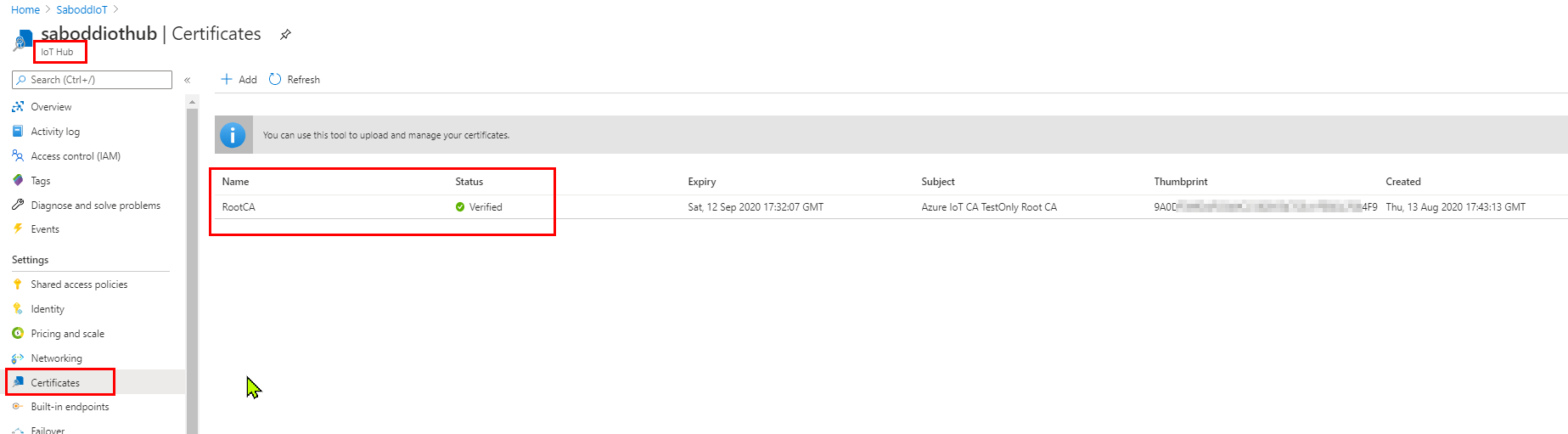
STEP 3: Create the new IoT Device from Azure Portal-IoTHub.
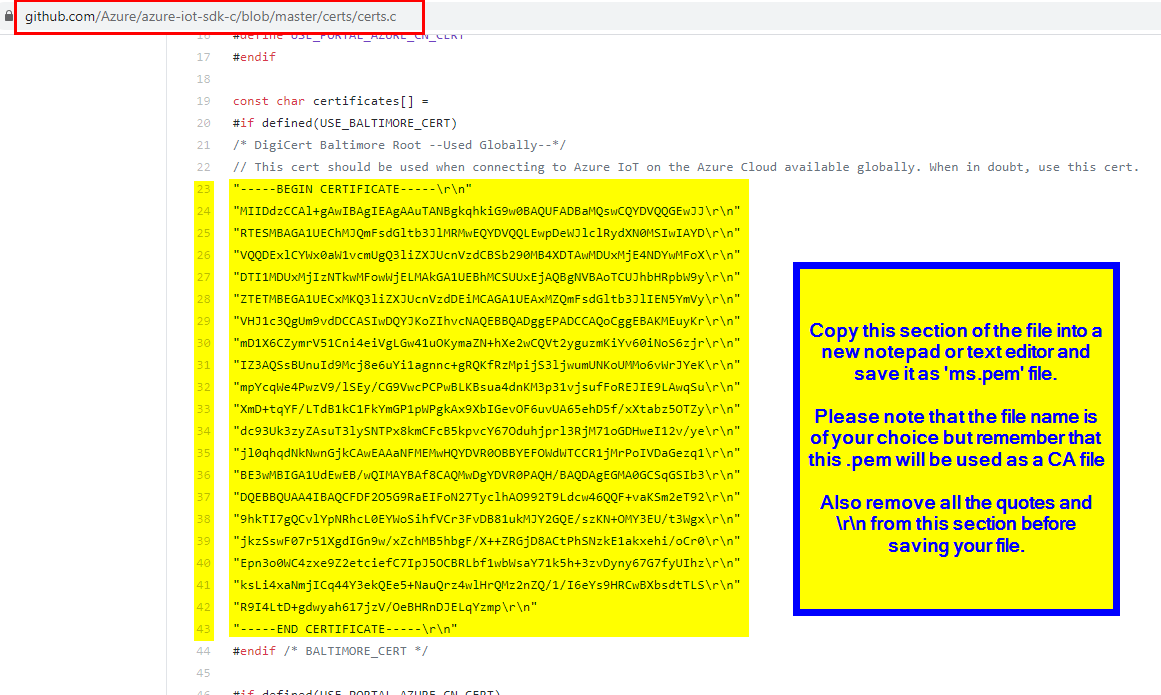
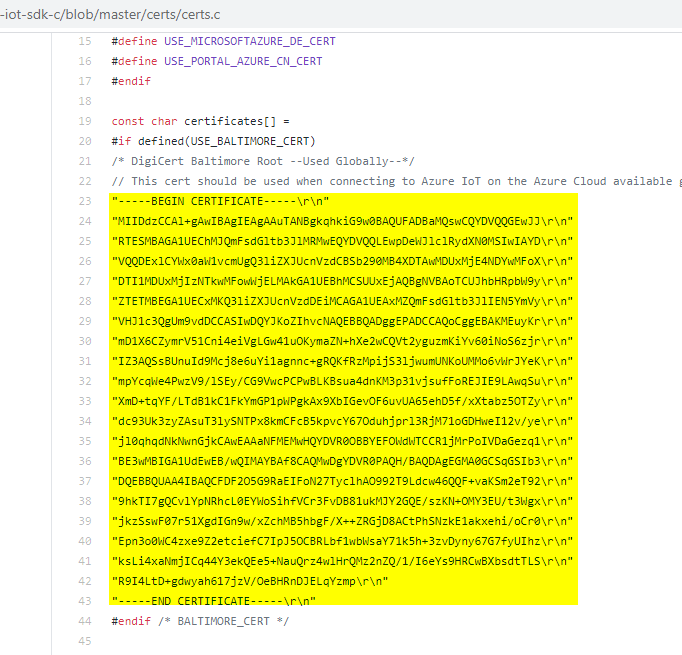
STEP4: Copy the Microsoft DigiCert Baltimore Root cert as MS.pem file--Used Globally. make sure to remove the double quotes and the line feeds.
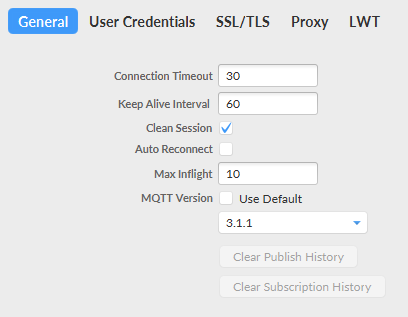
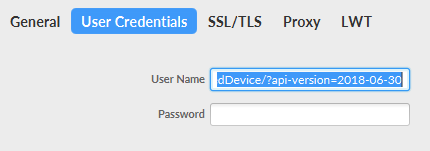
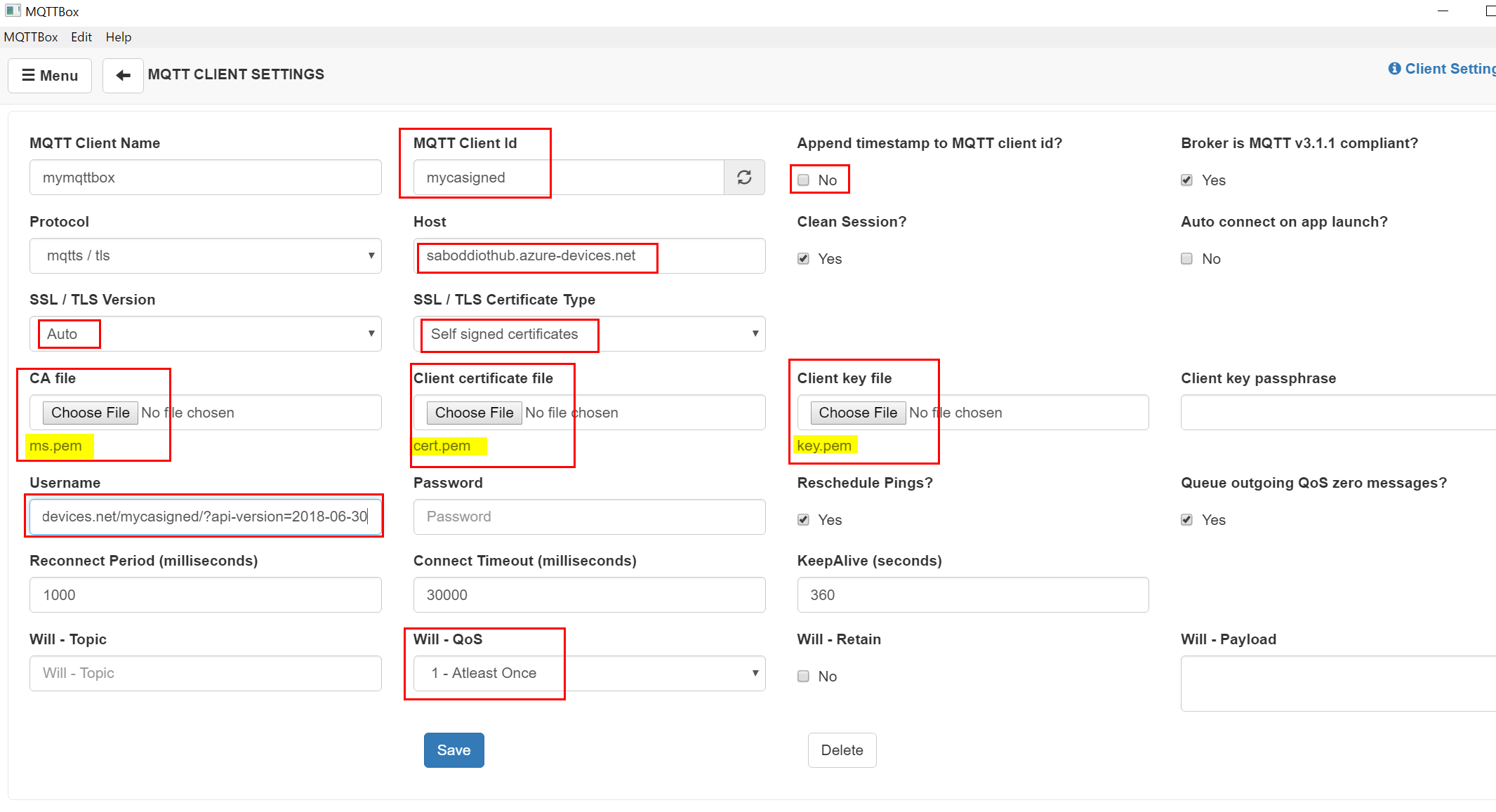
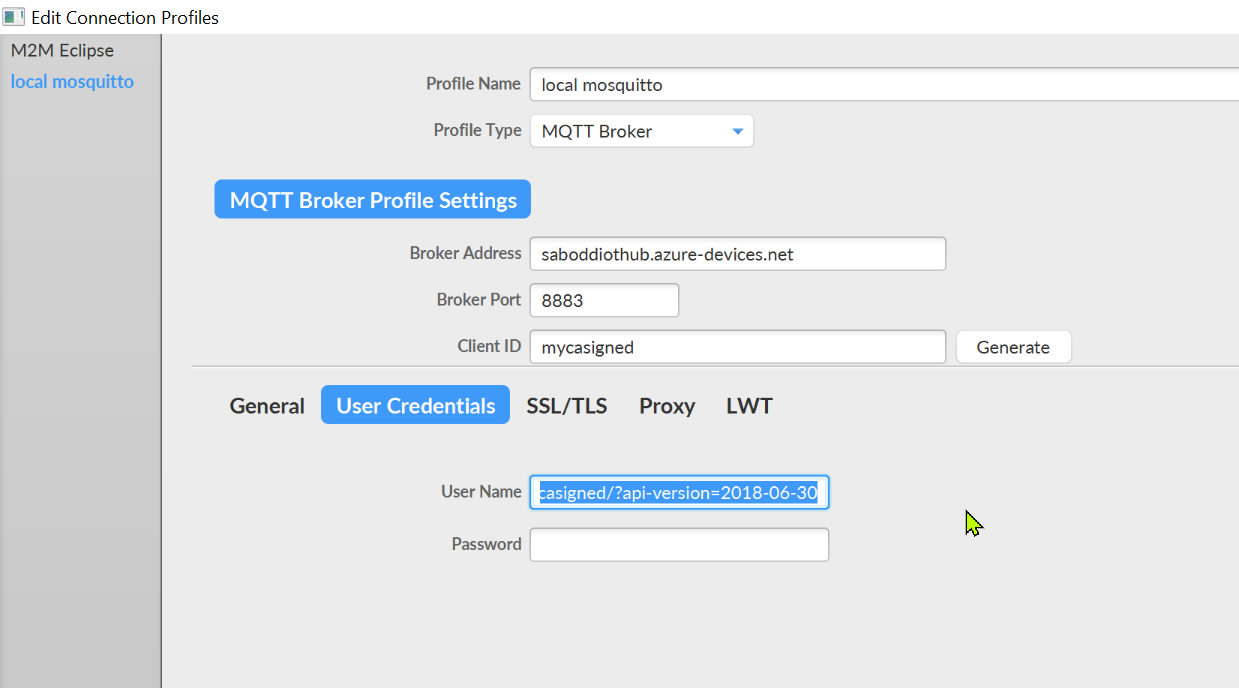
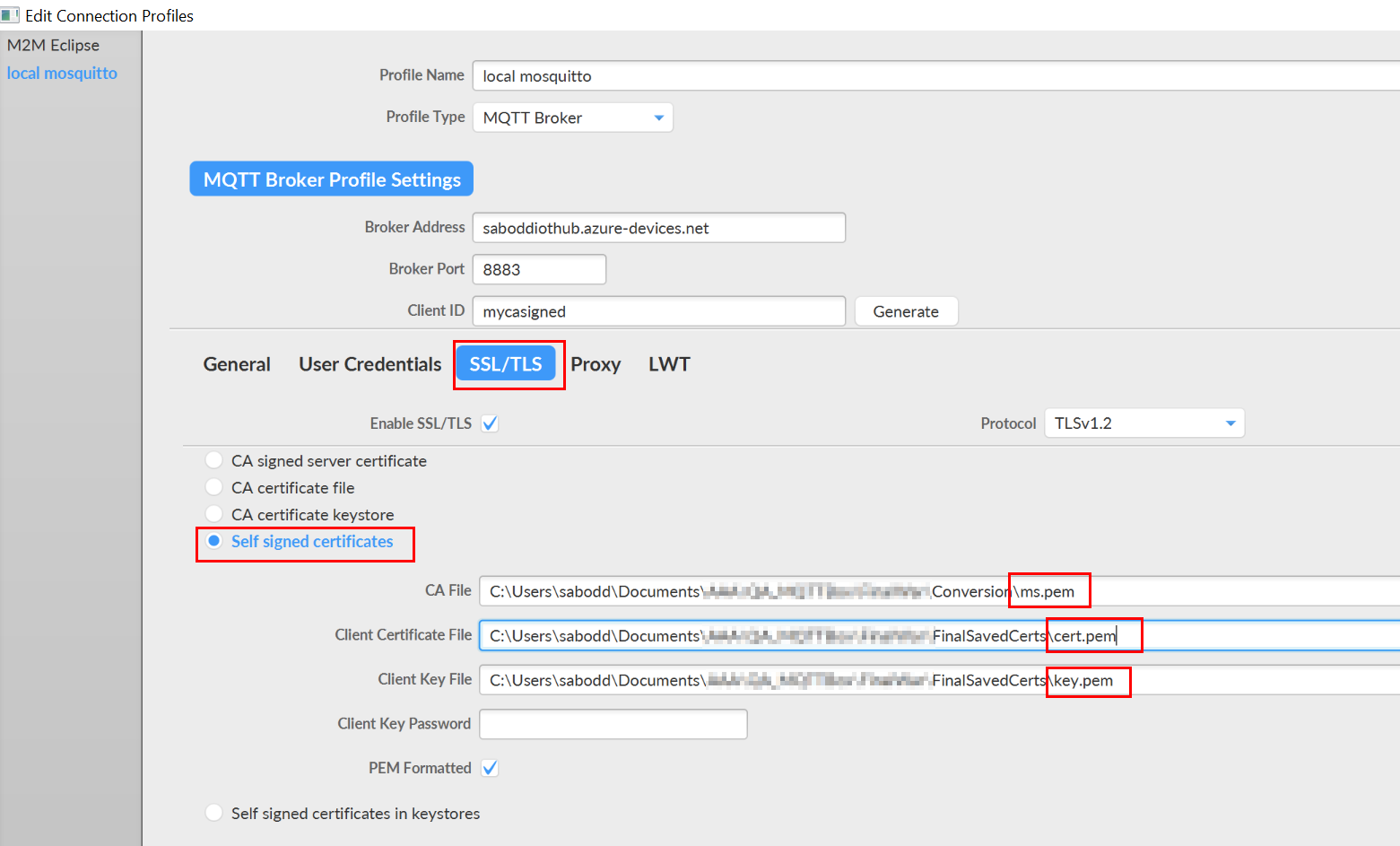
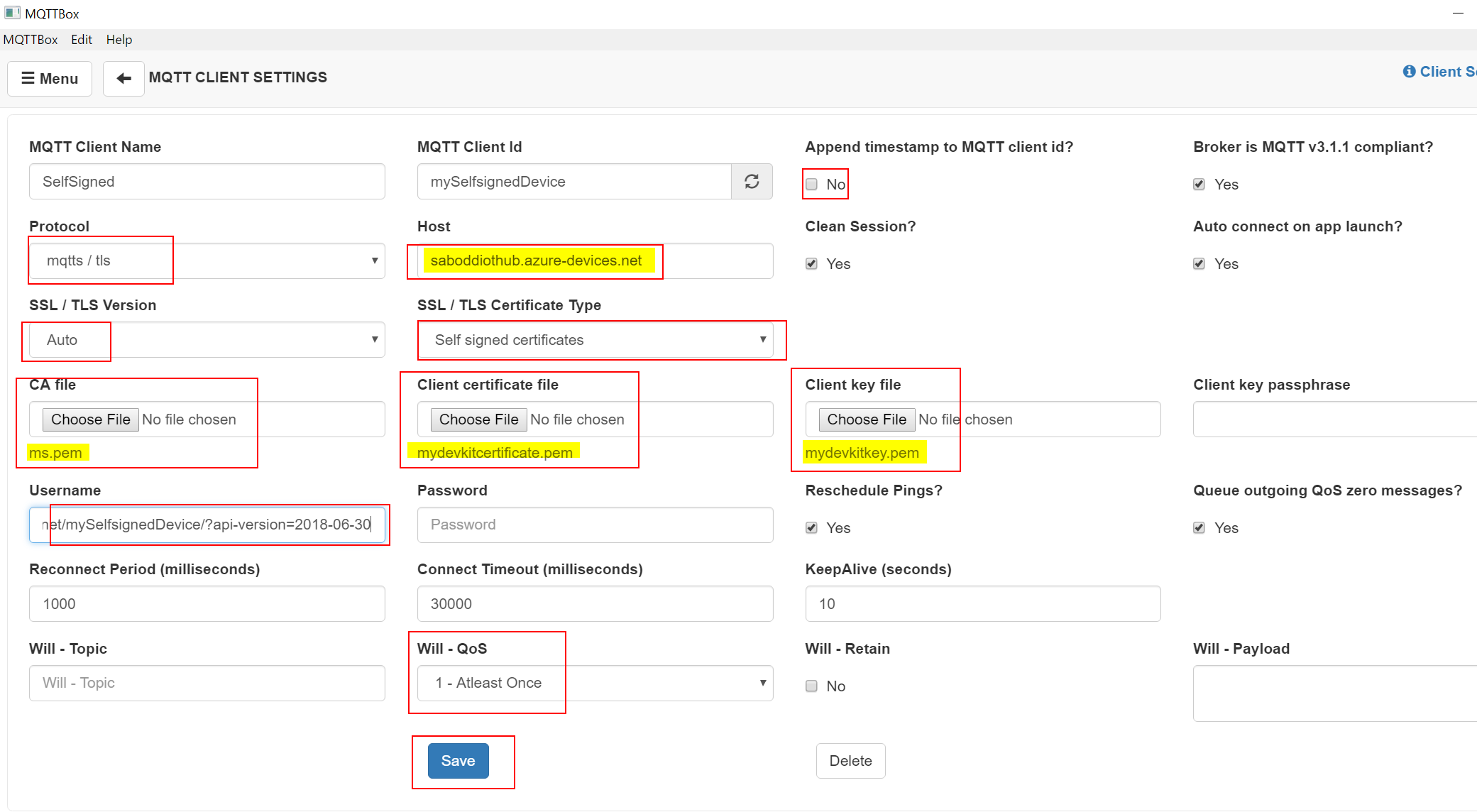
STEP 5: Open MQTT Box and configure the values.
----------
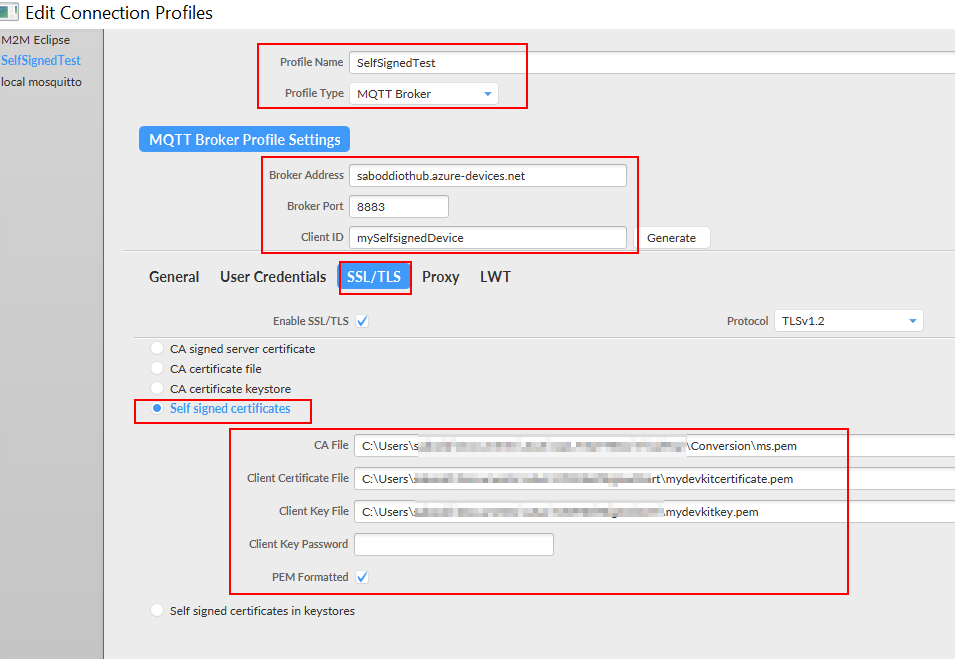
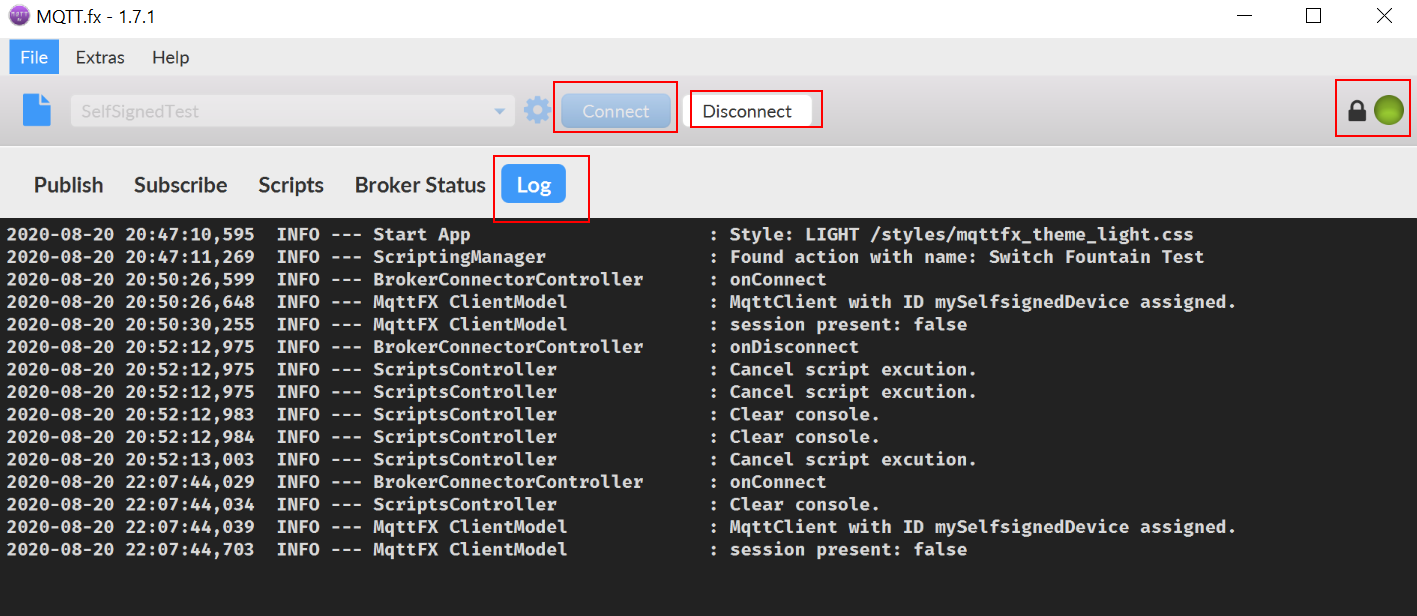
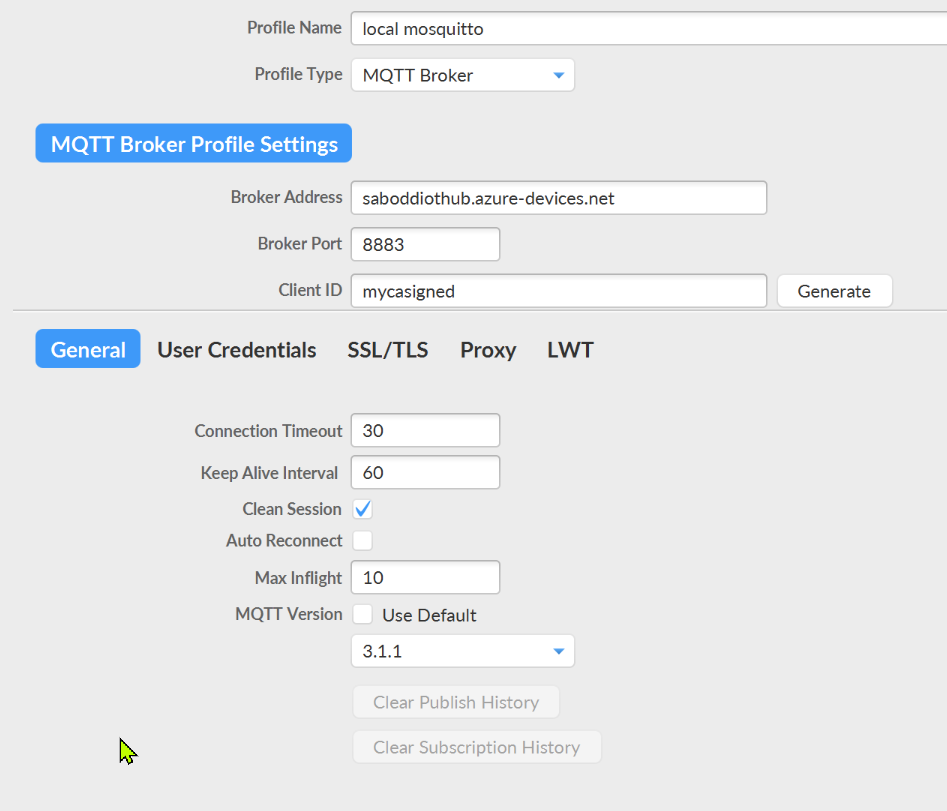
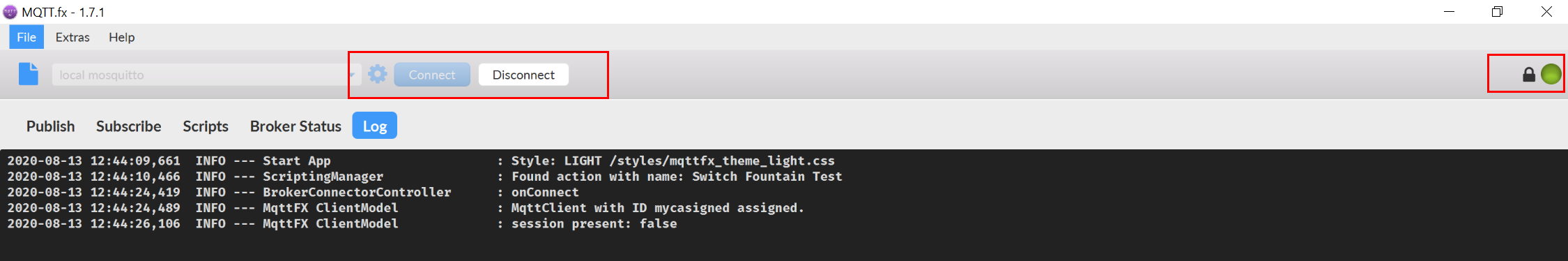
Let's now connect MQTT.fx to IoT HUB. [Please disconnect the MQTTBox before we proceed with MQTT.fx, since only one client can connect]