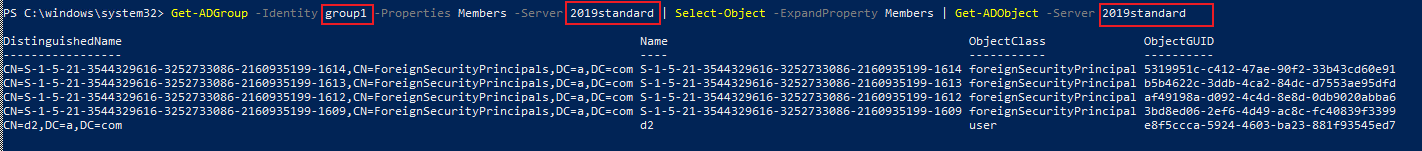
Hello
Thank you for posting here.
Maybe the link blow explains the situation you mentioned, it seems it is by design. But you do not need to perfom the solution.
Get-ADGroupMember returns error for domain local group to members from remote forests
https://support.microsoft.com/en-us/help/3171600/get-adgroupmember-returns-error-for-domain-local-group-to-members-from
And I did two tests in my lab:
Two forests (Fabrikam.com and a.com) have two-way forest trust.
Test one
Fabrikam.com: usertest3
A.com: group1 (usertest3 is the member in group1)
I migrate usertest3 with SID history in fabrikam.com to a.com, then I run the command below on DC in domain named a.com, I have the same error as you.
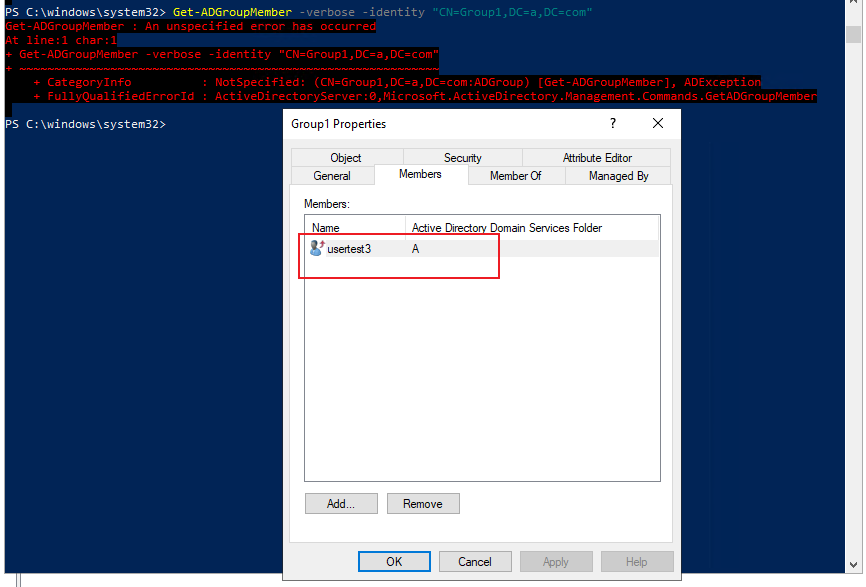
But I can logon machine with usertest3 in fabrikam successfully.
Test two
Fabrikam.com: u3
A.com: group1 (u3 is the member in group1)
I deleted u3 in fabrikam.com. Then run command on DC in domain named a.com:
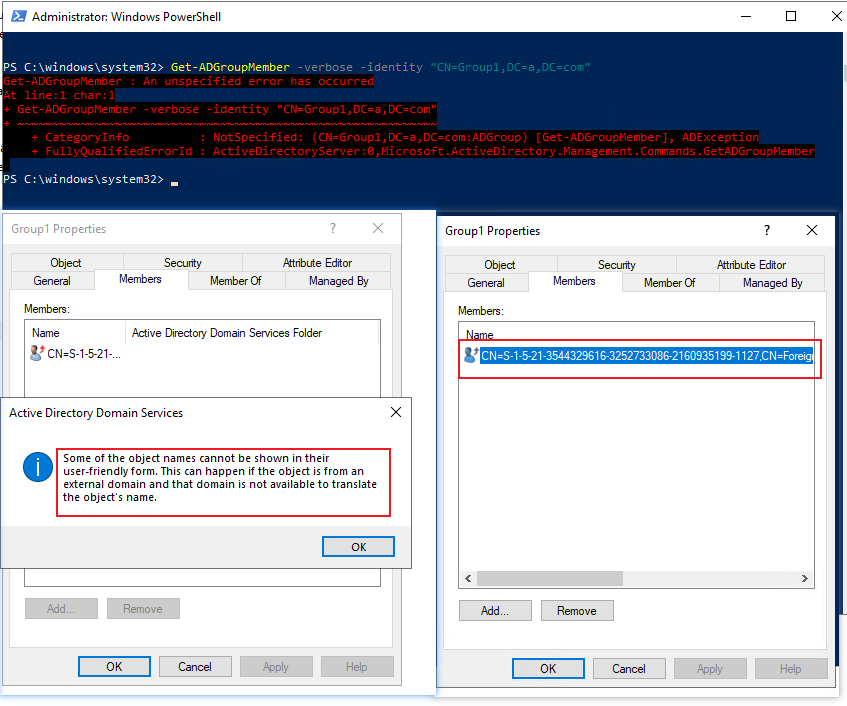
Best Regards,
Daisy Zhou