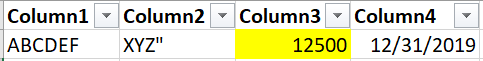
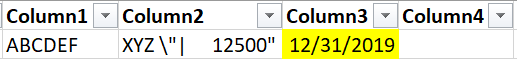
I see. I was confused when you mentioned corporate network. Is your corporate network a virtual network in Azure?
I noticed the connection strings included port number, so I had the thought, 'what if we changed the port number?'
I asked my colleague
Can Azure SQL Database be configured to use a port other than 1433?
and he replied
Not possible...on a VM where you have control of the server, you can change the server port the sql engine listens to but with Azure SQL DB as a PaaS service...this is not possible.
I did find the origin of the staging suggestion:
You don't want to open ports other than port 80 and port 443 in your firewall because of corporate IT policies. For example, when you copy data from an on-premises data store to an Azure SQL Database sink or an Azure Synapse Analytics sink, you need to activate outbound TCP communication on port 1433 for both the Windows firewall and your corporate firewall. In this scenario, staged copy can take advantage of the self-hosted integration runtime to first copy data to a Blob storage staging instance over HTTP or HTTPS on port 443. Then it can load the data into SQL Database or Azure Synapse Analytics from Blob storage staging. In this flow, you don't need to enable port 1433.
So, first step, do you have a self-hosted integration runtime in your corporate network?
Second step, go to your linked services and ensure that the integration runtime selected, is not the default azure-hosted one, but the self-hosted one you created.