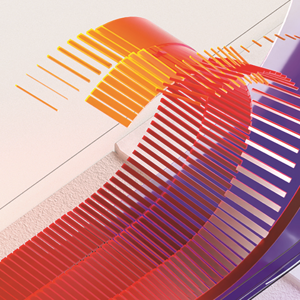
I created a certificate signing request for a new intermediate CA. The CSR was created with the critical flag on the KeyUsage property. I can verify this by running certutil -dump certificate.req.
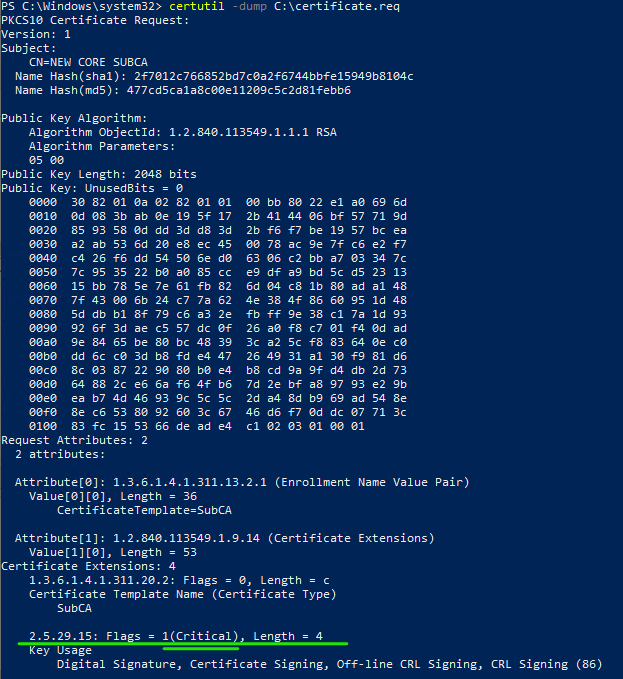
Upon importing the CSR into the (standalone) root CA, it does not recognise the critical flag on the CSR. The root CA seems to even completely omit the KeyUsage from the CSR, as the KeyUsage origin is set to Policy instead of Request.
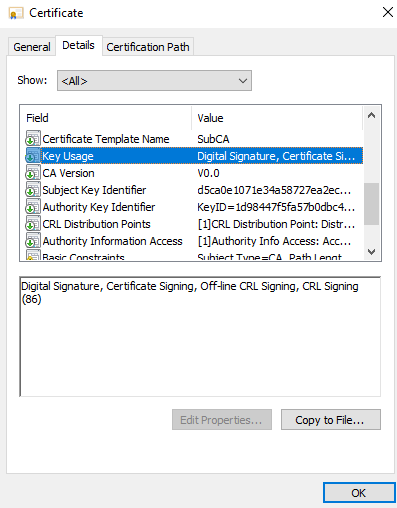
In the next image you can see that the critical flag is not present in the issued certificate.
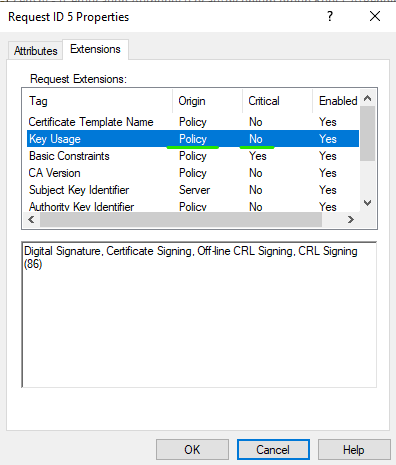
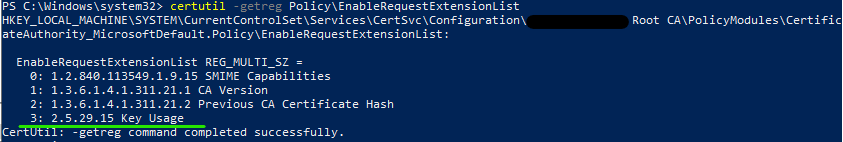
Next, I checked if the CA is configured to even transfer the KeyUsage from the request to the certificate, by running **certutil -v -getreg Policy\EnableRequestExtensionList* and checking if OID 2.5.29.15 is included. In the next image you can see, that it is.
Why is my root CA ignoring the flag in the request and how can I make it respect the request flag?