Hello,
I'm using Windows 2016 standard server that is joined in a domain. The domain admins are placed in the local administrators group, but I don't want the domain admins to be able to write or change data on the D-drive of the server. I've set the following security access rights on the D-Drive:
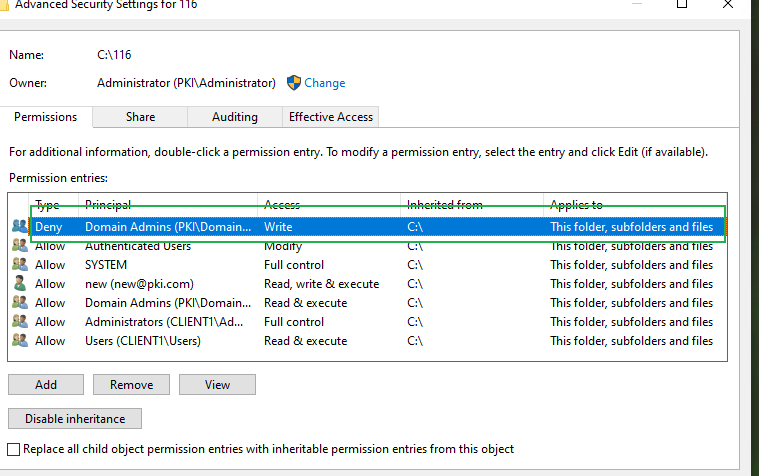
User Access Acces type Scope
SYSTEM Full Control allow This folder, subfolders and files
CREATOR OWNER Full control allow Subfolders and files only
Users Read & execute allow This folders, subfolders and files
Administrators Full Control allow This folder, subfolders and files
Domain Admins Special* deny This folders, subfolders and files
*: Create Files/write data; Create folders/append data; Write attributes; Write extended attributes; Delete subfolders and files; Delete; Change permissions; Take ownership
I would assume that due to the deny rights (overriding the allow rights), the Domain Admins should not be able to write/change anything on the D-Drive, but I can freely change anything on that drive when attaching the D drive from any computer in the network using a Domain Administrator account!
On the other hand, after explicitly denying the ('personal') DOMAIN\Administrator write access to the D-Drive (using the same special rights as for the Domain Admins group) , the access rights are enforced correctly and the administrator cannot change anything on the drive
Why are the Domain Admins group deny rights not enforced, while the 'personal' account is?
Regards,
Ge.