Seeing the exact same, Also wonder why a managed disk is try to access my Firewall, Also the Firewall it self try to access 443 to his own internal IP.
Any update on this @deherman-MSFT ?
Virtual Machine Connections to Managed Disks in Firewall Logs

Hi all! So this one is baffling me!
I have a Windows Server 2019 Azure Virtual Machine deployed into a virtual network with a 0.0.0.0/0 user defined route directing traffic to an Azure Firewall. There are no other user defined routes and the virtual machine is in the same virtual network as the virtual machine.
I have a network security group associated with the subnet that the VM resides in with overriding deny rules. Happy to share these however the important rule is that I'm allowing Internet connections outbound from the virtual network and controlling these connections with the Azure Firewall for more granular control.
While I see no IO errors on the virtual machine (it's not doing much, to be honest though) I'm denying access to several storage accounts I'm unaware of.
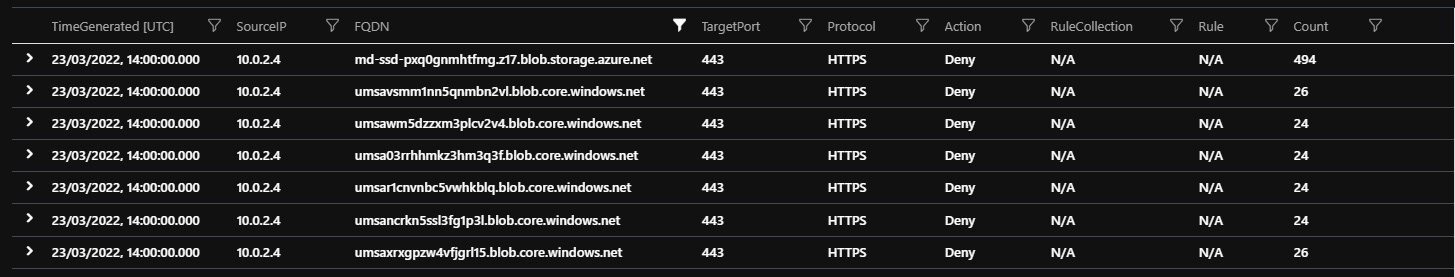
Disk export tells me that the FQDN starting md-ssd is the managed disk and I'm assuming the other storage accounts are those abstracted by the managed disk.
Anyway, the questions..
Do I need to allow this traffic through the Azure Firewall? How do I do so without allowing connections to all blob.storage.azure.net / blob.core.windows.net endpoints?
The only documentation I've found so far is that service endpoints aren't going to help: "Disk traffic from an Azure virtual machine: Virtual Machine Disk traffic for managed and unmanaged disks isn't affected by service endpoints routing changes for Azure Storage..." (From - virtual-network-service-endpoints-overview )
Some additional details that may or may not be relevant:
- The managed disk is encrypted with Azure Disk Encryption using a key encryption key
- The BitLocker encryption key is in the same vault as the key encryption key
- The key vault is locked down with a private endpoint in the same virtual network
- Firewall Logs/NSG Logs have been on since I started testing, happy to run log analytics queries to assist
4 answers
Sort by: Most helpful
-
 Robert Smit 1 Reputation point MVP
Robert Smit 1 Reputation point MVP2022-04-08T12:48:00.673+00:00 -
Andy Ball 11 Reputation points
2022-07-31T05:24:47.267+00:00 @Matthew Daines @Robert Smit hey you guys ever hear back about this noise with md- prefix in managed disks ?
Seeing same issue, have a call open with Premier Support but no response after several weeks
thx in advance
Andy -
Andy Ball 11 Reputation points
2022-09-25T01:42:07.727+00:00 @Matthew Daines @Robert Smit just thought i'd update , there is no update ... still working through it.
-
Woods, Jeffrey 1 Reputation point
2022-10-07T20:22:02.813+00:00 I ran across this today and the solution is to use Service Endpoints to allow the VM to do its admin storage account writes (analytics, etc) without leaving the virtual network, even if the VM and the storage account are on different subnets.
In the subnet that contains the VM that is making the problematic requests, configure the service endpoints thusly:
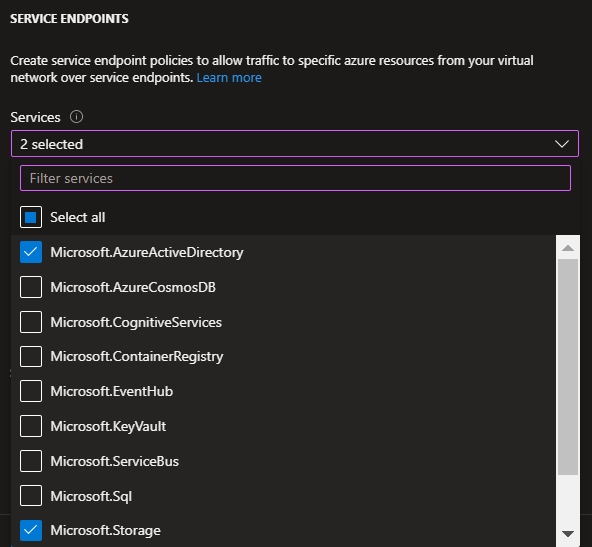
Then, the entries you're seeing in the log will cease, as shown in this image, taken 20 minutes after I established the service endpoint.
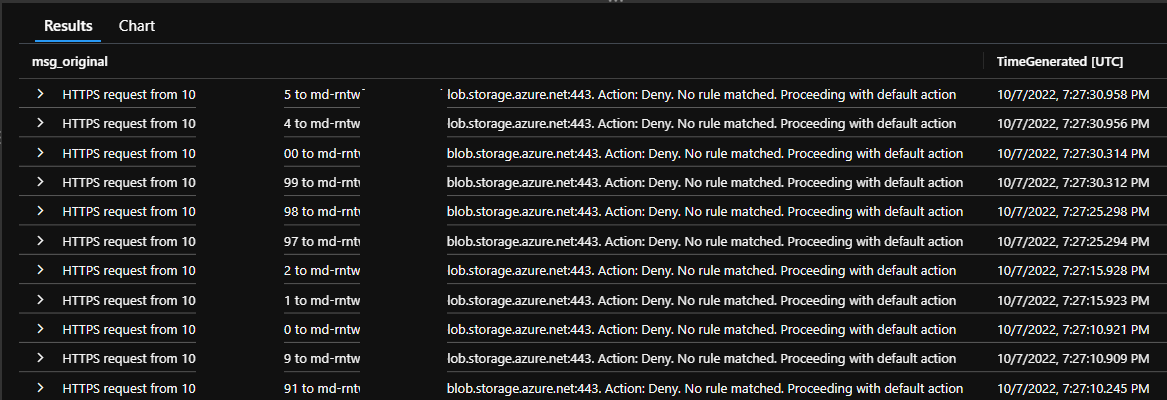
As a colleague in InfoSec wrote to our team after this was found:
Here is a quick explanation.
• The Firewall blocks outbound traffic from our machines to random blob storage accounts, as it should.
• Attempts to send traffic to blob storage accounts we have no visibility into appear suspicious but in this case turn out to be expected behavior
• Microsoft creates storage accounts in our tenant that are not visible to us for things such as this md-* storage and for certain configurations of SQL.Obviously we can’t allow traffic to any blob storage account on the Internet but Microsoft has a solution called Service Endpoints. Service Endpoints are a special type of routing on a subnet that cause connections from your subnet to specific services that you own to go direct and bypass the firewall. You can enable Service on a per service basis. The solution for this problem is to turn on service endpoint for Storage on the subnets that are running the VMs. Doing this means that the traffic will flow and not hit the FW – a win win.
So, hopefully there you have your answer. Best of luck!
Jeff Woods
Technical Architect
