Hello @Anonymous ,
Thank you for posting here.
Based on the description above, I did a test in my lab.
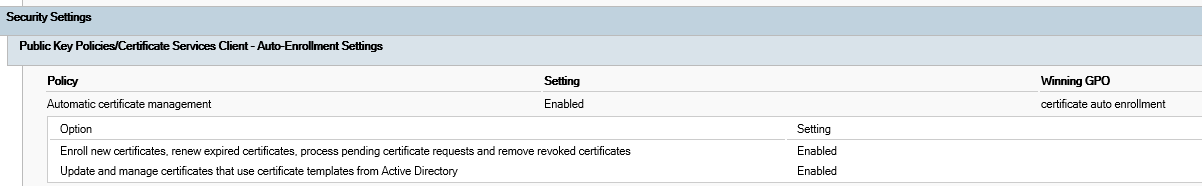
1.When I configured the following GPO settings for domain users, and after I revoked user certificates, it will remove the revoked user certificates automatically.
Automatic certificate management => Enabled
Enroll new certificates, renew expired certificates, process pending certificate requests and remove revoked certificates => Enabled
Update and manage certificates that use certificate templates from Active Directory =>Enabled
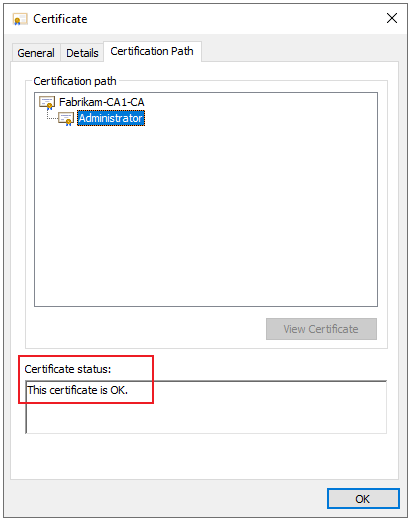
2.But when I do not configure the GPO settings above for domain users, and after I revoked user certificate, then the revoked certificate is still in user personal store and the certificate is OK after I view the certificate status on certificate path.
3.However, when I verify by running command certutil -verify certificatefile, the certificate shows it is revoked.
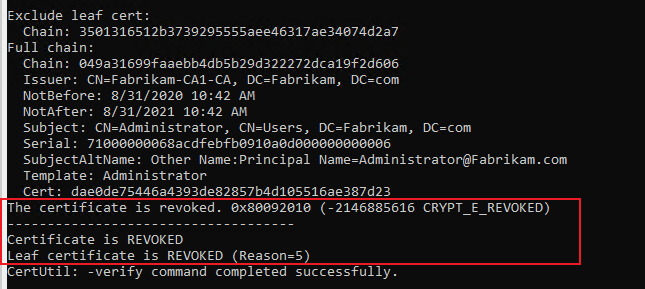
So you can check the certificate status you mentioned and if it is actually revoked, these certificates should be not used any more.
If you want to delete the revoked user certificates without user GPO settings, we can remove them manually.
If I misunderstood you, please correct me.
Best Regards,
Daisy Zhou
