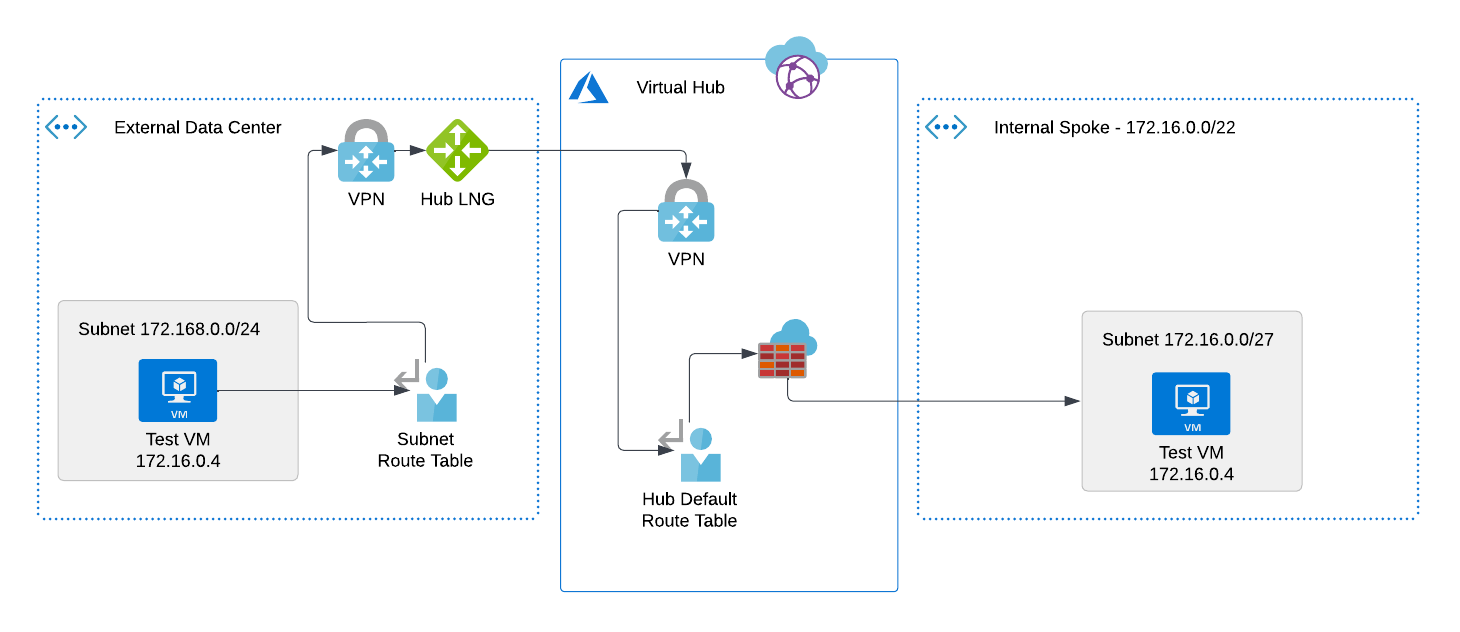
I have a VWAN/Secure Hub topology in Azure with the hub and all of its internal spokes living in the 172.16.0.0/16 -> 172.24.0.0/16 spaces. Internally, this all works just fine.
Now I need to be able to integrate external data centers by Site-to-Site VPN, and I don't control the IP addressing of those data centers - they're other companies.
All of the Microsoft examples show internal spokes that don't conflict with branches - the branches can target internal spokes because those addresses don't conflict with that of the data center. I don't have that situation.
All of the documentation about integrating branch networks suggests using SNAT in the VPN gateway in the hub - translate the data center IP into something branch-specific, and off you go. That isolates branches from one another. But what about internal spokes? I need a data center to be able to target an internal spoke resource, like a VM.
My understanding would be that I could use DNAT in the firewall policy to translate traffic into the appropriate spoke.
Here's the problem - I can't create a DNAT rule without using the public IP of the firewall - I don't want to do that, because I want the traffic to be completely internal to the hub. I also don't want to have to 1) allocate a public IP to every resource, and/or 2) play games with custom port numbers to keep the IP count down.
Ultimately, I want a completely private network way of allowing a customer to target one of my internal resources, where our addresses may overlap. A diagram of what I'd like to accomplish is attached.
Can I do this without other infrastructure? Can I do it at all?