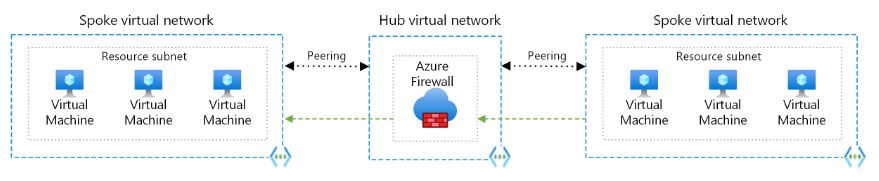
Hi @Jean-Claude Kalunga , Thank you for your question. I believe you should have a route table on each spoke described as below:
RT1: Spoke1-VM:
Destination: 10.2.0.0/16
Next hop Type: Virtual Appliance
Next hop IP: 10.0.1.4
RT2: Spoke2-VM:
Destination: 10.1.0.0/16
Next hop Type: Virtual Appliance
Next hop IP: 10.0.1.4
Since each spoke is already peered with the Hub VNET, the AzFW knows how to reach each spoke's VM.
You can open a port like 3389 on each VM using a NSG applied on their subnet, then use PsPING to run the test: psping <vm_ip>:3389