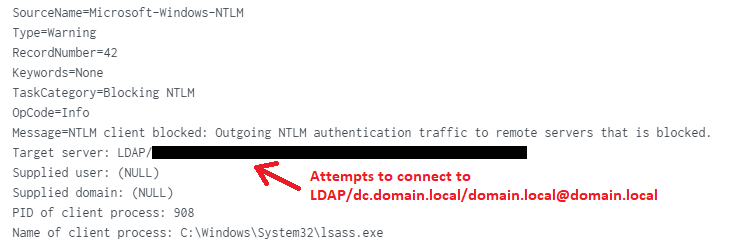
Hi there,
Firstly, check if the CRLs are up-to-date on the root CA server.
- Logon to the root CA with the domain Administrator.
- Open Certification Authority.
- Click Revoked Certificates\All Tasks\Publish\New CRL\OK.
- Refresh PKIview.msc console.
Second, check if CRLs or AIAs are configured correctly on the root CA server.
- Logon to the root CA with the domain Administrator.
- Open Certification Authority.
- Check the AIA and CDP on the Extensions tab of root CA Properties based on my example below.
AD CS - Unable to Request Certificates from Certificate Authority
---------------------------------------------------------------------------------------------------------------------------
--If the reply is helpful, please Upvote and Accept it as an answer–