Hi,
Thanks for your update.
Based on my knowledge, windows 2008 CA server can issue certificate to windows server 2019. And if you need configure new certificate for VPN server, in Properties of New Template, we don't need to modify the compatibility and the provider Settings. For certificated needed for configuring AOVPN, please kindly refer to following steps which we have test in our lab.
Prerequisites: if you need to configure AlwaysOn VPN, 3 certificate templates are needed.
- The first certificate template (we will name it "Computer <Domain Name>") will be used for the NPS server to authenticate RADIUS requests using EAP-TLS, PEAP-MSCHAPv2 or PEAP-TLS. Also, we will use this certificate for clients who are going to authenticate using a machine certificate for IKEv2 ( NOTE: Machine certificate authentication only possible in IKEv2).
- The second certificate template (we will name it "User <Domain Name>") will be used for the users that perform EAP-TLS and PEAP-TLS authentication methods.
- The third certificate template (we will name it "RAS SSL <Domain Name>") will be used by the VPN server for the SSL binding in SSTP tunnel. Also, we can use this certificate for IKEv2 tunnel connection ( IKEv2 requires a certificate in the VPN server as well ).
Configure your Certificate templates
Please kindly note that we do not have such windows 2008 server to test, just posted the screenshot from server 2012, but the configurations also apply for server 2008. Thank you for your understanding.
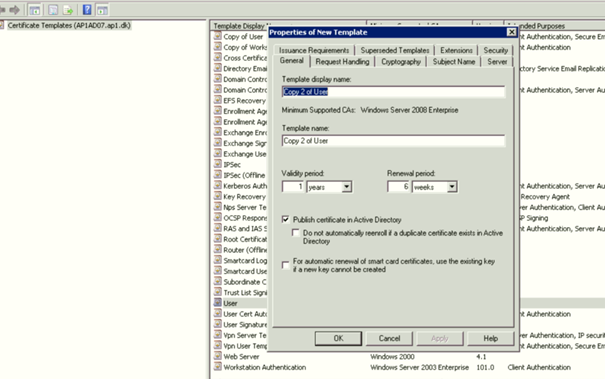
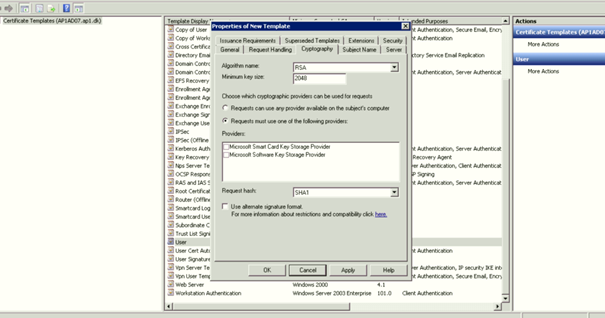
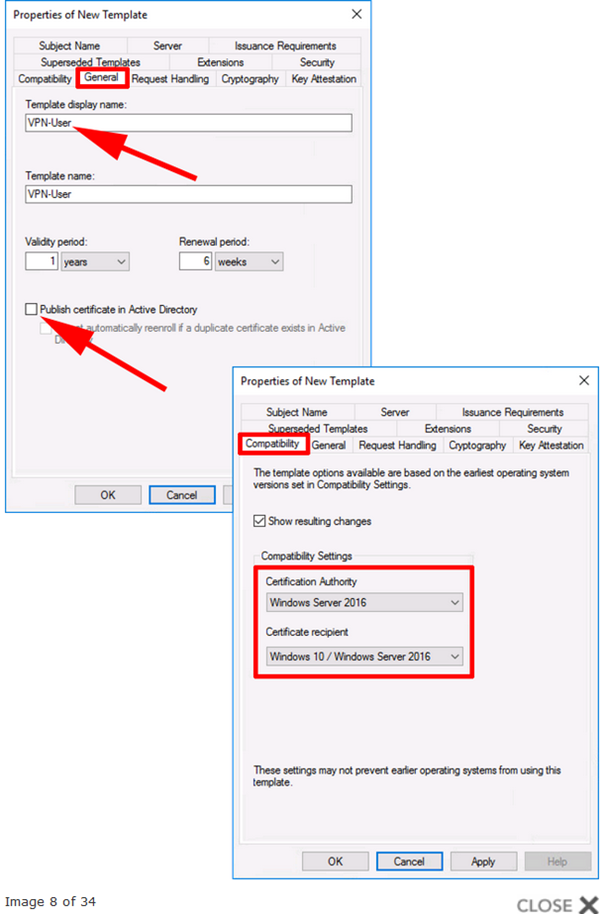
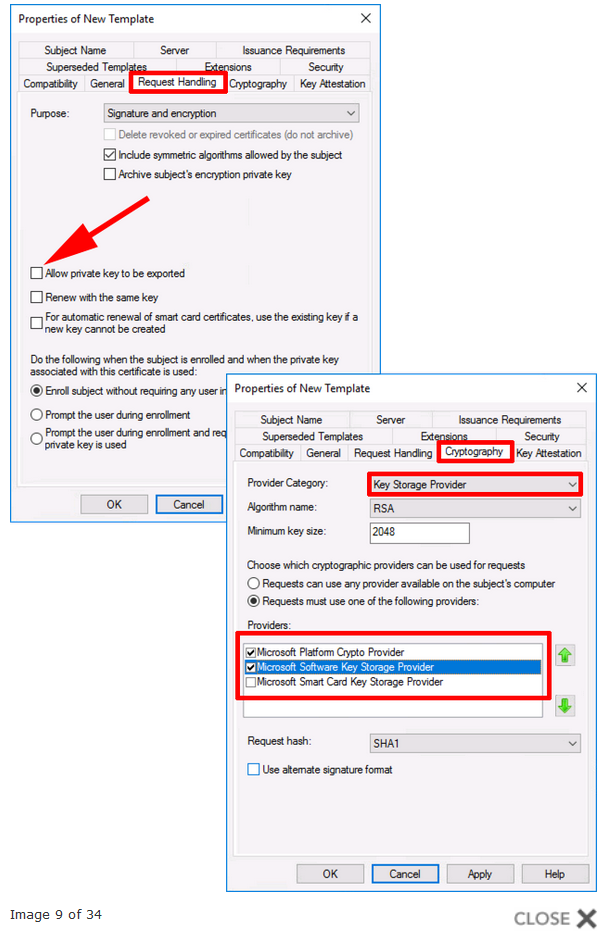
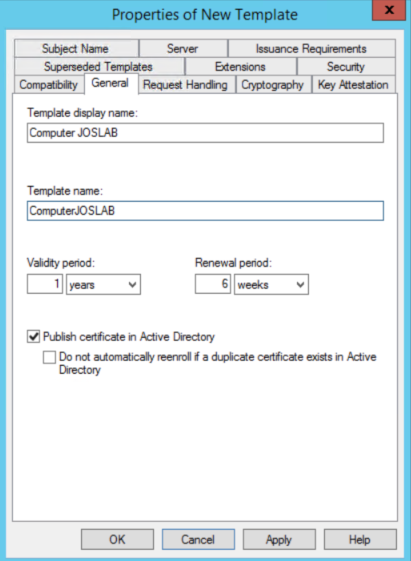
a. Open Certificate Authority Console: click certificate templates. Right click the Computer Certificate and click Duplicate Template. Go to the General tab and add the name Computer "<Domain Name>". Select Publish certificate in Active Directory (This option will allow you the autoenrollment of the certificate by GPO if you are planning this for the future).
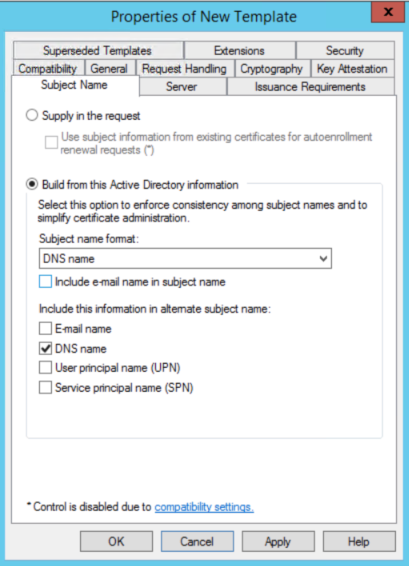
b. Go to the Subject Name tab and in the dropdown button for Subject name format, select DNS name.
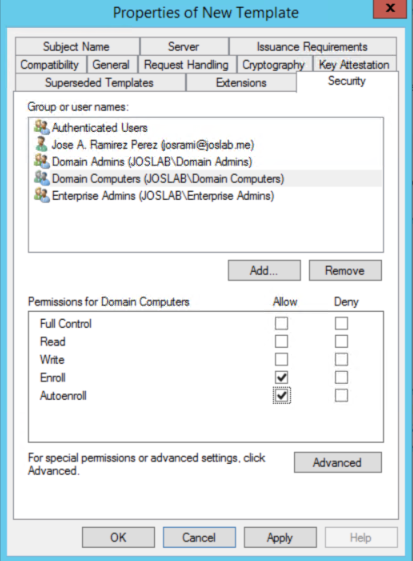
c. Go to Security tab. Make sure Authenticated users group is there and has Read permissions. Also, make sure Domain Computers group is there and has Enroll Permissions. If you are planning to deploy Autoenrollment GPO for this certificate, you would need to select also Autoenroll for Domain Computers group.
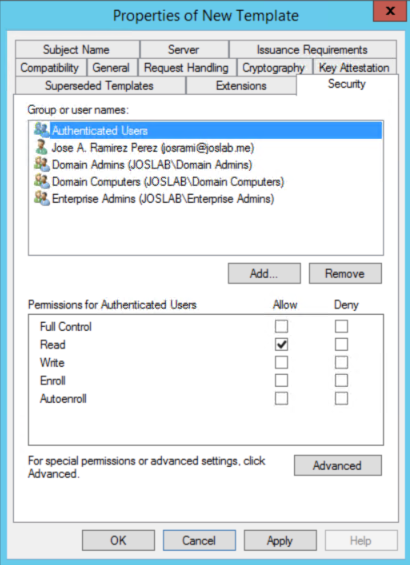
d. Right click the User certificate template and click Duplicate Template. Go to the General tab and add the name "User <Domain Name>". Select Publish certificate in Active Directory (This option will allow you the autoenrollment of the certificate by GPO).
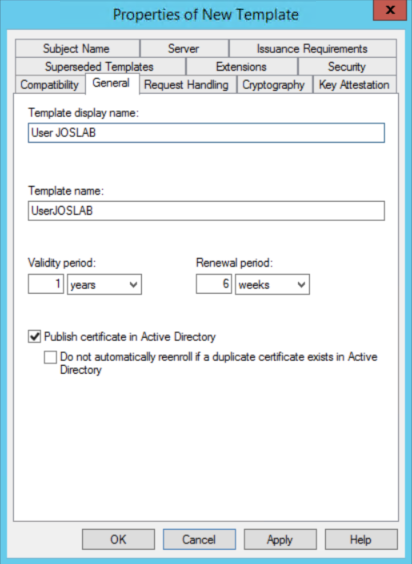
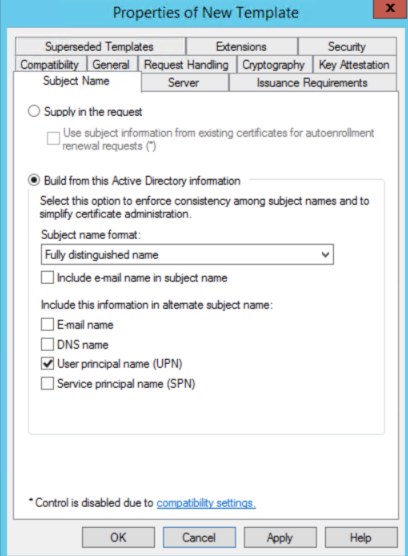
e. Go to the Subject Name tab, uncheck the options "Email name" and "Include e-mail name in subject name".
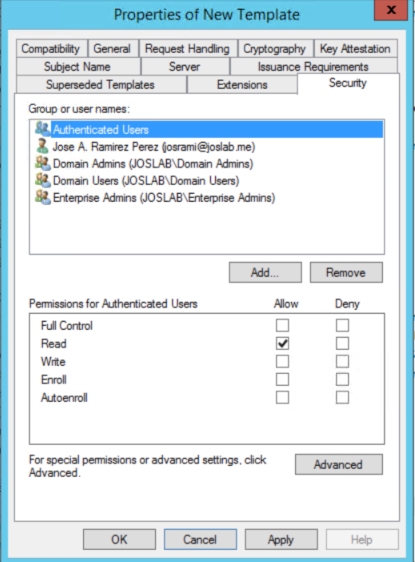
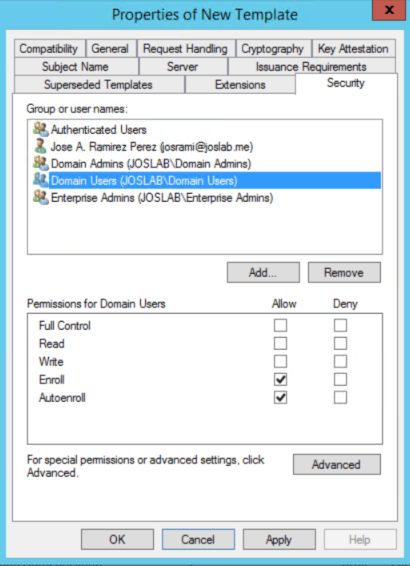
f: Go to Security tab. Make sure Authenticated users group is there and has Read permissions. Also, make sure Domain Users group is there and has Enroll Permissions. If you are planning to deploy Autoenrollment GPO for this certificate, you would need to select also Autoenroll for Domain Computers group.
g: Right click again the Web Server template and click Duplicate Template. Go to the General tab and add the name "RAS SSL <Domain Name>".
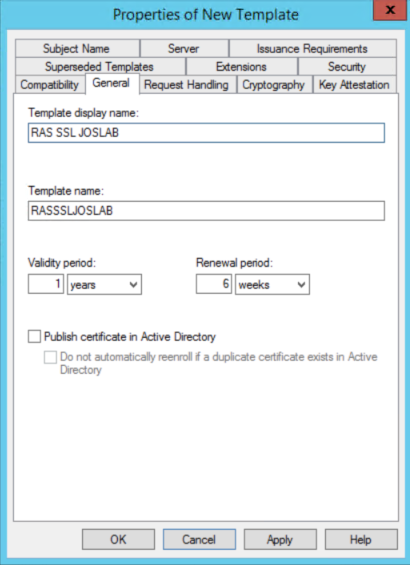
h: Go to the Subject Name tab, select the option Supply in the Request.
i: Go to Extensions tab and click Edit, then click Add and select Client Authentication. Then click Ok.
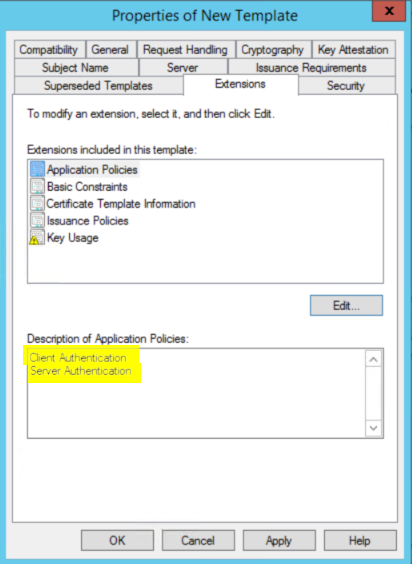
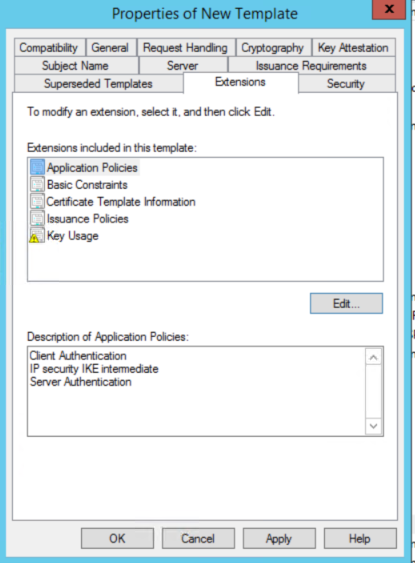
NOTE: The certificate we are currently creating would be for the SSL binding used by SSTP. If you are planning to deploy IKEv2 in your infrastructure, you will require to use this certificate as well. However, IKEv2 requires the EKU "IP Security IKE Intermediate". So, Click on Edit again, then click Add and select IP Security IKE Intermediate. Then click Ok. If you are not going to use IKEv2, you can skip this note.
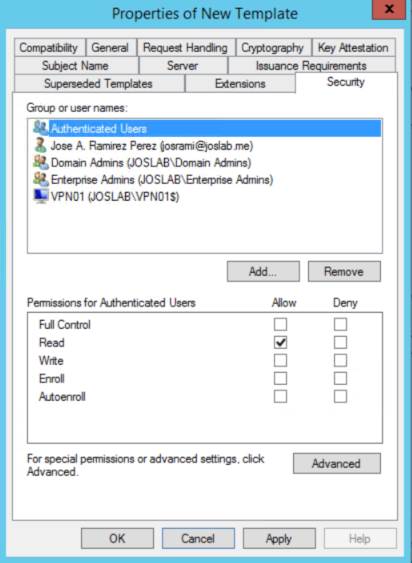
j: Go to Security tab. Make sure Authenticated Users group is there and has Read permissions. Click on Add. Click Object Types, select Computers, and then search for your VPN server's account, then click Ok. Select Read and Enroll permissions for the VPN server's account. Then, click Apply and Ok.
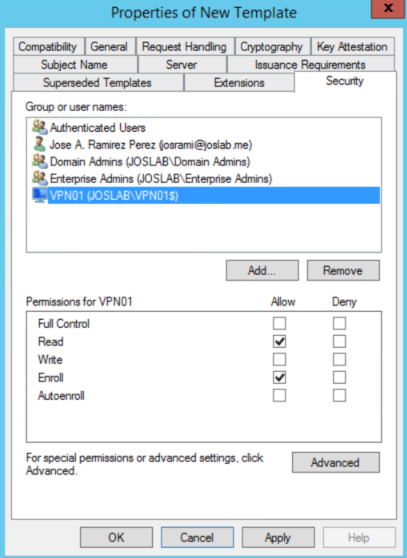
k: Close the Certificate Templates Console. We have now created the necessary certificate templates. We just need to publish them to be available for enrollment. Right Click Certificate Templates and click New and then Certificate template to issue. Select all 3 certificates templates we have created before.
Best Regards,
Sunny
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.