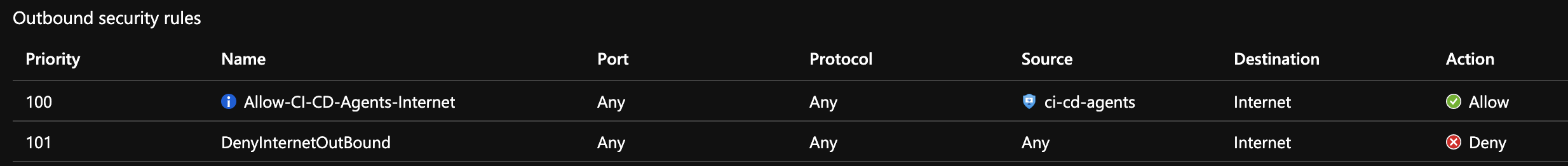
@PB "If WEBSITE_VNET_ROUTE_ALL is set to 1 and you don't have any routes that affect public address traffic on your integration subnet, all of your outbound traffic is still subject to NSGs assigned to your integration subnet. If WEBSITE_VNET_ROUTE_ALL isn't set, NSGs are only applied to RFC1918 traffic."
Source: https://video2.skills-academy.com/en-us/azure/app-service/web-sites-integrate-with-vnet#network-security-groups
Can you please verify that you have set the above app setting? I'm thinking that might be the cause of the behavior your're noticing. If that doesn't work, please reply back and we can continue troubleshooting. Let us know if this helped as well. We look forward to your reply.