Using Internet Explorer Enhanced Security Configuration on Terminal Servers
Hi, Axel Rivera again with information about IE Enhanced Security and how it could affect users when browsing from Terminal Servers.
As many of you know, when you first install Windows 2003 and 2008 Servers, IE Enhanced security is enabled. Because Internet Explorer Enhanced Security Configuration is applied only to servers, it typically affects only administrators and has little impact on users. This is true because users rarely log on to servers; few organizations allow users to log on to a server and then to start browsing the Internet. An exception to this rule is terminal servers. If Internet Explorer Enhanced Security Configuration is enabled on a terminal server, Internet Explorer Enhanced Security Configuration settings apply to any user logging on to that server. As a result, users may find it difficult to access Web sites or intranet resources.
If your users have only limited rights to the terminal server (as is usually the case), consider enabling Internet Explorer Enhanced Security Configuration for administrators but not for users. Having limited rights to the server means that the user can cause only a limited amount of damage if he or she accesses a Web site with malicious content. The limited damage might be preferable to the number of help desk calls that are likely to arise if users find themselves unable to access resources in the expected manner (particularly if those users are accustomed to accessing those resources without problem from their desktop computers).
NOTE:
If Terminal Servers users are unable to browse Internet or Intranet sites, one of the first troubleshoot action items is to determine if IE Enhanced Security is enabled. For more information see the troubleshoot section below on this document.
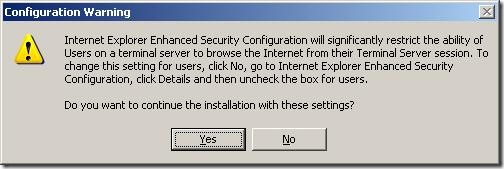
If you install Terminal Server by using unattended installation, consider disabling Internet Explorer Enhanced Security Configuration for both users and administrators (if you want to enable Internet Explorer Enhanced Security Configuration, enable it post-installation, or include the proper commands within your unattended answer file). If you attempt to install Terminal Server while Internet Explorer Enhanced Security Configuration is enabled, Windows prompts you with the message box shown in Figure 14.
Figure 14 Attempting to Install Terminal Server While Internet Explorer Enhanced Security Configuration is Enabled
If you decide to manage Internet Explorer Enhanced Security Configuration differently on terminal servers than you do on other servers, you must determine which computers are terminal servers and which ones are not. If all of your terminal servers are in the same organizational unit (OU) in Active Directory, this task is straight-forward. If this is not the case, you can use a script to determine whether a computer is a terminal server. A sample script that carries out this task is shown in Listing 17.
Listing 17 Identifying Terminal Servers
On Error Resume Next
strComputer = "atl-2003-01"
Set objWMIService = GetObject("winmgmts:!\\" & strComputer & "\root\cimv2")
Set colTerminalServiceSetting = objWMIService.ExecQuery _
("SELECT * FROM Win32_TerminalServiceSetting")
For Each objTerminalServiceSetting in colTerminalServiceSetting
If objTerminalServiceSetting.AllowTSConnections = 1 Then
Wscript.Echo "Terminal Server is enabled on this computer."
Else
Wscript.Echo "Terminal Server is not enabled on this computer."
End If
Next
If you enable or disable Internet Explorer Enhanced Security Configuration by using Group Policy, you can create a WMI filter that either includes or excludes terminal servers from the GPO. For example, suppose you want to enable Internet Explorer Enhanced Security Configuration on all of your computers running Windows Server 2003 that are not terminal servers. In that case, you can create a GPO and then use the following WMI filter to ensure that terminal servers are not affected by the policy:
Select * From Win32_TerminalServiceSetting Where AllowTSConnections <> 1
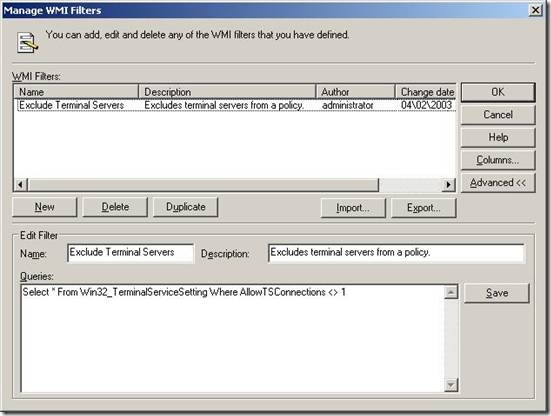
If you create a filter to exclude terminal servers from a GPO, the Manage WMI Filters dialog box will look similar to Figure 15.
Figure 15 Excluding Terminal Server from a GPO
Troubleshoot Steps/scenarios:
Article 933991 described most of the issues related to IE Enhanced security affecting regular users. It also outlines steps we must take to resolved these issues. Consider the issue to be related to default profiles with tattooed IE Harden settings inherited from the time the server was build and in order to remedy these issues, the default profile must be updated.
In other scenarios, where Security Zone policies are also implemented on servers where IE Enhanced Security is enable, it is important to understand that IE Enhanced Security will more likely override the IE Policy settings and should be disabled to fully benefit of IE Administrative and IE Maintenance policies.
Standard users cannot turn off the Internet Explorer Enhanced Security feature on a Windows Server 2003-based terminal server
Articles:
Managing Internet Explorer Enhanced Security Configuration
Internet Explorer Enhanced Security Configuration changes the browsing experience
Regards,
The IE Support Team
Comments
- Anonymous
May 06, 2009
The comment has been removed - Anonymous
September 09, 2009
I have the same issue. The batch file didn't fix it. - Anonymous
September 23, 2009
Same problem, batch file didn't work for me either. Any other ideas? - Anonymous
November 04, 2009
The comment has been removed - Anonymous
December 12, 2009
Has anyone found a fix for this yet? It is causing problems for my Citrix Xenapp users on Server 2008 as well. There must be a way to use GPO to turn off IE ESC for terminal server users. - Anonymous
January 21, 2010
The comment has been removed - Anonymous
February 25, 2010
The batch file works, what it is that Windows 2008 have a time Refresh interval for their UI which is set to 2 minutes. - Anonymous
August 12, 2010
The batch file worked for me. You are a life saver!!! - Anonymous
May 02, 2011
Normally, you ahve to run the batch under the user context to fix the problem. Also, enabling and diasable IE Enanced Securit from the UI will also fix the problem.