Azure Security Center now in Public Preview
Hey Azure security community!
Today’s a big day for us on the Azure Security Team.
AZURE SECURITY CENTER is now in Public Preview!
What is Azure Security Center?
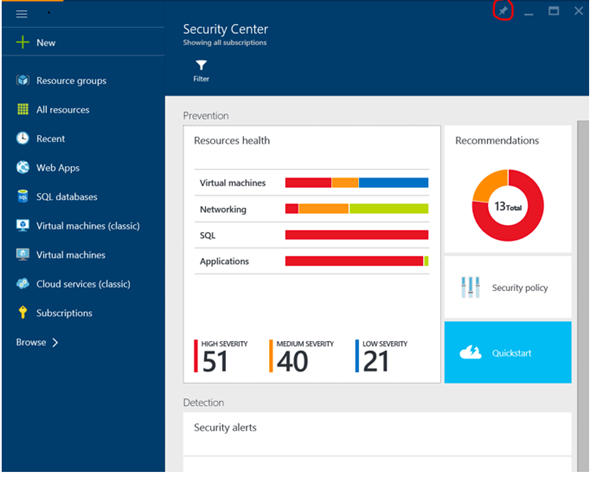
In a nutshell, Azure Security Center is a cloud-based solution that helps you prevent, detect, and respond to threats and vulnerabilities by giving you increased visibility into, and control over, the security of your Azure resources.
With Azure Security Center you get integrated security monitoring and policy management across your subscriptions. This helps you detect threats that might otherwise go unnoticed. Not only that, it also works with a broad ecosystem of security solutions.
Of course, there’s a lot more to Azure Security Center than we can put into a nutshell.
For example, you can use Azure Security Center to:
- Create security policies on a per-subscription basis. Some subscriptions contain high value assets or sensitive data that need higher levels of security. Other subscriptions might require a lower level. You can tailor the security policy to meet the security needs of each of your subscriptions.
- Assess the current security state of your Azure resources. You need to know what Azure-based resources need attention. Azure Security Center gives you with a dashboard that surfaces the security health of your resources in a single glance. You can drill down and get more details or take action to address issues.
- Get expert recommendations and enable them. Whether you’re an Azure security expert, an aspiring expert, or even a non-security professional, everyone wants to make sure their Azure resources are secured using best practices. Azure Security Center helps you by evaluating the security status of Azure resources and gives you recommendations. Pick some or all of them, based on your requirements. You can even enable many of them in the Azure portal.
- Manage and respond to security alerts. Get alerted to security threats detected by Azure Security Center and integrated partner solutions, like antimalware and firewalls. You can see details about the threat, impacted resources and recommended mitigations.
Are you in? Yes! Here are your next steps:
- Get a free Azure trial account if you don’t already have an Azure account
- Check out Sarah Fender’s Azure Security Center post on the Azure Blog
- Watch Sarah’s presentation at AzureCon 2015,
- Read the Azure Security Center docs
- See the Azure Security Center announcement
- Ask questions on the Azure Security Center MSDN forum
Stay tuned here at the Azure Security Team blog for more information, insights, tips, tricks and more on Azure Security Center.
Thanks!
Tom
Tom Shinder
Program Manager, Azure Security
@tshinder | Facebook | LinkedIn | Email | Web | Bing me! | GOOG me!
Comments
Anonymous
January 04, 2016
Enabled data collection on one subscription and it automatically created a storage account. I turned off data collection, waited a while for agents to be removed from VMs and then deleted the storage account. I waited a while and went to enable the data collection once again so I could point to my named storage account but it keeps referring back to the deleted storage account. I went ahead an enabled to see what would happen. It enabled the data collection but the storage account is no where to be found, at least showing in the portal.Anonymous
January 04, 2016
Hi Daryl - It could be that the deleted storage account wasn't completely deleted? Maybe try again after a few minutes. If that doesn't work, I'll see if I can repro. Thanks! -TomAnonymous
January 04, 2016
Tom thanks for the response. I did wait for about 30 mins for the storage account to delete prior to re-enabling. It appears that its collecting data but the storage account is not exposed in the Azure Portal under Storage accounts, but it does show in the Security Policy. I checked using PowerShell as well and that particular storage account is not being shown as a deployed resource. I will give it a while and see if it eventually shows up. if not, I will disable data collection once again and wait a few days before trying again.Anonymous
January 04, 2016
Thanks for the update. I'll take this back to the product group and see if this is expected behavior right now during public preview. Let me know what happens when you test again in a few days and I'll report back here on what I find out. Thanks! -Tom