Cloud Security as a Shared Responsibility
I thought it would be valuable to start a series of conversations on how Microsoft thinks, acts and enables cloud infrastructure security from an Azure perspective. Cloud security is a shared responsibility between Microsoft and all our tenants. We (Azure) protect the infrastructure, we detect fraud and abuse and we respond to incidents by notifying customers. These are the three foundational pillars of the Azure security infrastructure: are the three foundational pillars of the Azure security infrastructure:
Protection
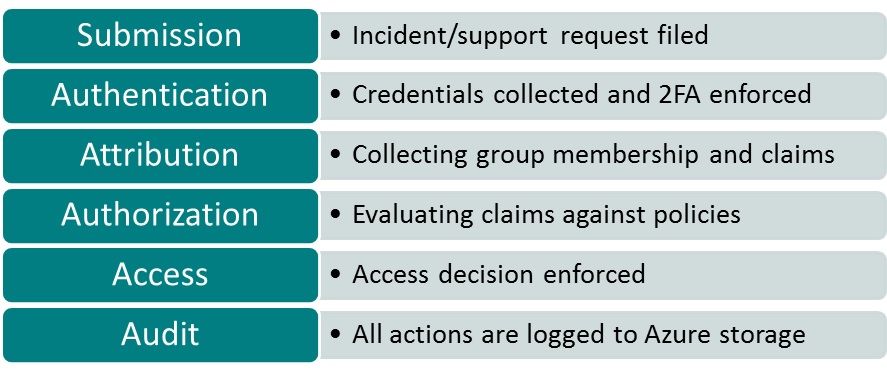
Let’s start with protection. The protection pillar is based on the core infrastructure. And, accordingly, the protection of the infrastructure is all about infrastructure access control and management. In Azure, we have very strict restricted access workflows in place whenever access is required, requested or needed for troubleshooting:
But protection is also dependent on infrastructure access control and management. In Azure, we have very strict restricted access workflows in place that require specific elevation requests and approvals whenever access is required for troubleshooting or assisting customers. We require two-factor authentication, using smart cards issued to engineers, for these DevOps and support activities that occur in Azure. This two-factor authentication is required to even request access the infrastructure where all approvals, actions and activities are always logged and monitored.
Detection
On the detection side, one basic scenario I would like to share today is how we monitor network flows, to not actually analyze/inspect your data or traffic, but to actually monitor the greater network infrastructure to help identify unusual traffic flows and volumes that very expected in size, volume or connections. Cloud security requires both Azure and cloud tenants to monitor all assets deployed in the cloud end-to-end. It is not a strict wall between the two responsibilities.
Another scenario, even if the Azure infrastructure is patched and protected, if customer VMs are not patched by their owners, they can be quickly compromised and then used to attack other tenants. A good example was the ShellShock vulnerability that was used against Linux VMs very quickly once the vulnerability was announced last September. This is where our commitment steps back in and we perform breach notifications with our customers to take immediate action within 48 hours or we will disable/suspend deployments to ensure other customers are not affected, attacked or damages by compromises tenants. As you can see, this is where our response pillar comes into play.
Last, but not least, one more critical area in the detection pillar is how we use machine learning to detect attacks, anomalous behaviors or discover malicious activity. We use machine learning analytics to detect not only attacks, but also fraud, unusual user activities and also phishing attacks across Azure Active Directory and Office 365. This is will be an upcoming topic in a future blog, so stay tuned to this channel!
Response
Next, let’s talk about cybersecurity abuse cases and how we respond to these. Azure investigates every report submitted to Microsoft CERT (https://cert.microsoft.com). Without question, the volume and intensity of abuse attacks is continuing to grow over time. Examples of activity we see and respond to are:
- SPAM
- Phishing
- DoS
- Hacking
- Copyright Infringement
- Illegal Activities
- Serving/Hosting Malware
If we discover abuse of fraud through an external report or malicious traffic from a tenant’s VM, we send out notifications from Azure Safeguards team. This team’s charter is to protect Azure’s IP address reputation which often means notifying customers that they have been compromised. This is a great example in our response pillar when we often work with customers to help them in performing forensic analysis of large scale breaches.
We only perform this action or analysis when asked and explicitly approved by customers. We are often helping tenants identify potential source of compromise or even zero days in third party software or applications. This is just one of the ways we work with our customers to ensure we have end-to-end security through shared responsibilities and collaboration.
David B. Cross
Engineering Director, Azure Security
Comments
- Anonymous
February 21, 2016
Great Article..It was very informative..I need more details from your side..include some tips..I am working in <a href="http://www.excelanto.com">Cloud Erp Software Companies In India</a>