Troubleshooting Agent Deployment in Data Protection Manager 2007 - DCOM
The DPM agent is a DCOM application - it cannot function correctly without proper DCOM configuration. This section covers the necessary configuration checks to make sure that DCOM is configured correctly.
Non-Clustered Member Servers:
As a rule, DCOM Settings for a working DPM 2007 Agent are evidenced by a lack of problems: You'll need to check Event Viewer, Add\Remove Programs, DCOMCNFG, and WBEMTEST in order to confirm the COM is working.
Event Viewer:
Make sure that there are no VSS or DCOM errors showing up in the event logs on the agent and the DPM server.
Here are some examples of what you might see on your DPM Server if DCOM needs to be checked out....
5/6/2008 8:46:46 AM 1 0 10006
DCOM N/A
<<DPMserverName>> 2148007941 <<DPM serverName fqdn>>
{C4EBD674-1457-4B79-BE30-B04735AED9D1}
Event Type: Error
Event Source: DPM-EM
Event Category: None
Event ID: 2
Date: 5/8/2008
Time: 9:02:00 AM
User: N/A
Computer: <<DPMserverName>>
Creation of recovery points for <<Protected ServerName>> on
<<Protected ServerName fqdn>> have failed.
The last recovery point creation failed for the following
reason: (ID: 3159)
The replica of <<Protected ServerName>> on
<<Protected ServerName fqdn>> is not consistent
with the protected data source. (ID: 30301)
DCOMCNFG:
Open DCOMCNFG, by clicking on Start\Run, and entering ‘DCOMCNFG’. Navigate down to
Console Root\Component Services\Computers\My Computer and open the properties of ‘My Computer’.
Note: If 'My Computer' has a red 'X' by it and the properties cannot be fully displayed, check the MSDTC (Distributed Transaction Coordinator) service to make sure it is running. If it doesn’t start, correct this problem before continuing. If the protected computer is a member server or workstation, try starting it and setting the service to 'Automatic' and rebooting. After logging onto the machine, open DCOMCNFG and 'My Computer' should appear without a red 'X' by it. If the system is a clustered server, make sure the cluster service is running as this will affect the MSDTC service's ability to run. MSDTC doesn’t, however, have to be a clustered resource in order for this to work correctly.
Check also for the existence of 2 DCOM Applications that are installed when the DPM Agent (recall that the DPM Agent is often called the "DPMRA") is installed on a server or workstation. Following are the settings for the DPMRA and WSSCmdletsWrapper DCOM applications.
‘DPM RA’ DCOM Application
Navigate through the "DCOM Config" tree to the DPM RA Service, as below, and select properties.
1. Under 'General', "Authentication Level - Default"
2. Under 'Location', only "Run application on this computer" should be checked
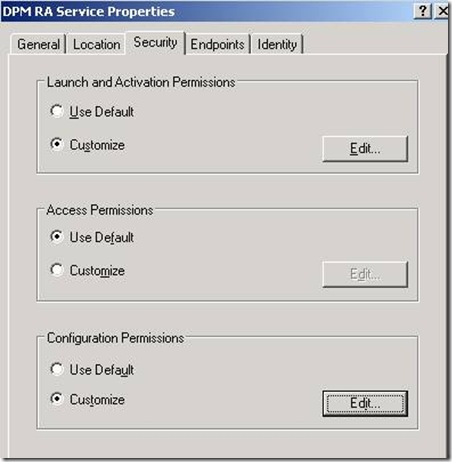
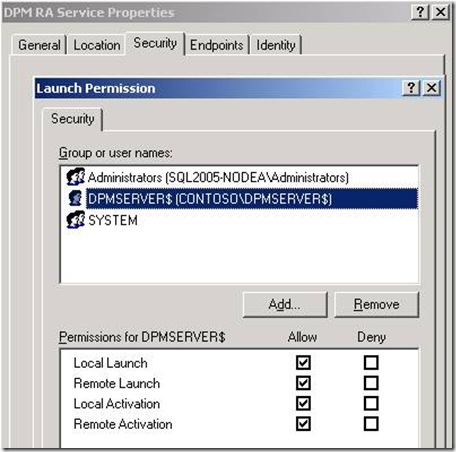
3. Under Security, verify that the "Launch and Activation Permissions" (select "Edit") include the machine account for the DPM Server as shown below.
4. Under Endpoints, leave "… default system protocols …" as the only entry.
5. Under Identity, the radio button "The system account (services only)." should be checked.
WSSCmdletsWrapper
This DCOM application appears under the same tree as above (My Computer / DCOM Config / WSSCmdletsWrapper / Properites). The related application is C:\Program Files\Microsoft Data Protection Manager\DPM\bin\WSSCmdletsWrapper.exe.
1. Under 'General', "Authentication Level - Default"
2. Under 'Location', only "Run application on this computer" should be checked
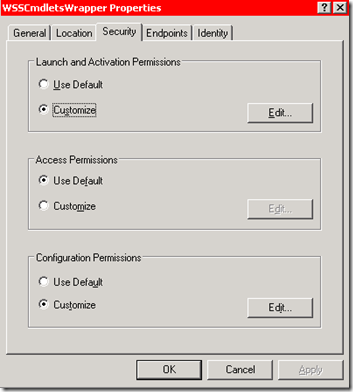
3. Under Security, you should see
4. Under Endpoints, leave "… default system protocols …" as the only entry.
5. Under Identity, the radio button, "The launching user" should be checked.
If you're concerned that the DCOM permissions have been modified, check the following registry key on both the protected server and the DPM server. There are up to 4 registry values added at the root of the OLE key.
HKLM\Software\Microsoft\Ole – check for the existence of the following value: ‘EnableDCOM’[REG_SZ] = ‘Y’ if not present, or if it is set to ‘N’ – either add the value or change it to ‘Y’. This is the registry storage location which tells if DCOM is enabled or disabled.
To reset the DCOM security, at the OLE registry key, delete all keys except for 'Default' and 'EnableDCOM'. Now reboot the server. When the server comes back up, the DCOM security will be at the default and you will need to open up DCOMCNFG in order to reconfigure it.
NOTE: Please backup the OLE key before you delete it. This will not cause the server to fail to boot but having a copy of the key will allow you to return it to its previous configuration if needed or desired.
The DPM Agent requires Distributed COM to work and does not require COM+ for agent installation or normal operation. Agents can be deployed on to systems that do not have the "Enable network COM+ Access" enabled within Add\Remove Programs.
Local DCOM Settings for DPM Agents are shown below.
1. Check to make sure that DCOM is enabled on the server that is going to be protected by DPM. This can be done in 2 ways. From within the UI, check the following in DCOMCNFG.
Open DCOMCNFG, by clicking on Start\Run, and entering ‘DCOMCNFG’. Navigate down to
Console Root\Component Services\Computers\My Computer and open the properties of ‘My Computer’.
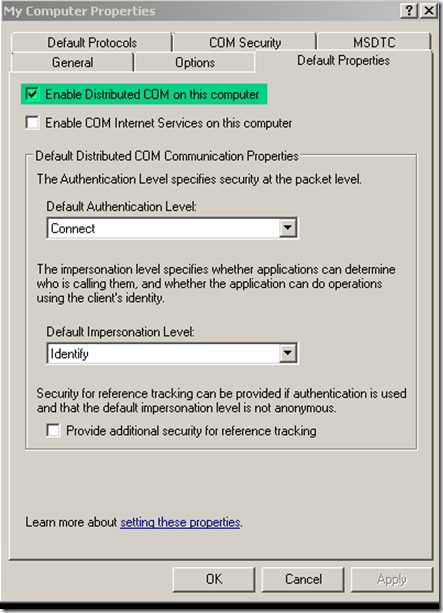
On the "Default Properties" tab, "Enable Distributed COM on this computer" should be checked.
2. Check to make sure that the "Default Authentication Level" is set to "Connect" and “Default Impersonation Level" is set to "Identify".
3. The other option is to check the registry. Look for the key " HKLM\Software\Microsoft\Ole\EnableDCOM = Y"<REG_SZ> – check for the existence of this key and if not present, or if it is set to 'N' – either add the value or change it to 'Y'.
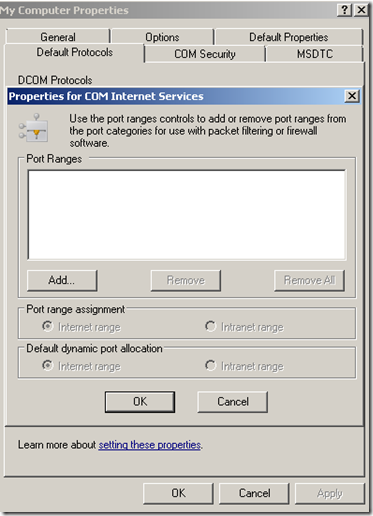
4. Back to the GUI on the Default Protocols tab - confirm that "Connection-oriented TCP\IP" is at the top. Also check the properties for DCOM port range to see if there are any restrictions (by highlighting "Connection-oriented TCP\IP" and selecting properties). Most likely, the screen will be blank, as below.
There are several registry settings that control the DCOM port restriction functionality. All of the named values listed below are located under the
HKEY_LOCAL_MACHINE\Software\Microsoft\Rpc\Internet
registry key. This registry key does not appear in the registry by default and must be created. If you find a need to restrict the DCOM ports, you should add the same port restrictions to both the DPM server and the protected server.
Note: You must reboot your machine any time you make changes to any of the following registry settings in order for them to take effect. Warning: Serious problems might occur if you modify the registry incorrectly by using Registry Editor or by using another method. These problems might require that you reinstall your operating system. Microsoft cannot guarantee that these problems can be solved. Modify the registry at your own risk.
NAME TYPE
VALUE
Ports
REG_MULTI_SZ
Specify one port range per line. Example: 3000-4000 5141
DESCRIPTION: One or more port ranges. The options below determine the meaning of this named value.
PortsInternetAvailable REG_SZ "Y" (don't include quotes)
DESCRIPTION: Always set this to "Y".
UseInternetPorts REG_SZ "Y" or "N" (don't include quotes)
DESCRIPTION: If this value is set to "Y", then the Ports named value indicates which ports should be used for DCOM applications. If this value is set to "N", then the Ports named value indicates which ports should NOT be used for DCOM applications.
Examples:
1. Add the Internet key under: HKEY_LOCAL_MACHINE\Software\Microsoft\Rpc
2. Under the Internet key, add the values "Ports" (MULTI_SZ),
"PortsInternetAvailable" (REG_SZ), and "UseInternetPorts" (REG_SZ).
In this example ports 5000 through 5100 inclusive have been arbitrarily selected to help illustrate how the new registry key can be configured. For example, the new registry key appears as follows:
Ports: REG_MULTI_SZ: 5000-5100
PortsInternetAvailable: REG_SZ: Y
UseInternetPorts: REG_SZ: Y
3. Restart the server. All applications that use RPC dynamic port allocation use ports 5000 through 5100, inclusive. In most environments, a minimum of 100 ports should be opened, because several system services rely on these RPC ports to communicate with each other.
You should open up a range of ports above port 5000. Port numbers below 5000 may already be in use by other applications and could cause conflicts with your DCOM application(s). Furthermore, previous experience shows that a minimum of 100 ports should be opened, because several system services rely on these RPC ports to communicate with each other.
Note: The minimum number of ports may differ from computer to computer and depends on the configuration of the computer.
To test and verify connectivity after making this registry change you can utilize the DCOMtest.exe tool. To download the tool and get additional details regarding the use and results you can leverage the following article.
KB259011 “SAMPLE: A Simple DCOM Client Server Test Application”
<support.microsoft.com/default.aspx?scid=kb;EN-US;259011>
For additional details on Using Distributed COM with Firewalls you can leverage the following links:
KB154596 “How to configure RPC dynamic port allocation to work with firewalls”
<support.microsoft.com/default.aspx?scid=kb;EN-US;154596>
<<msdn2.microsoft.com/en-us/library/ms809327.aspx>>
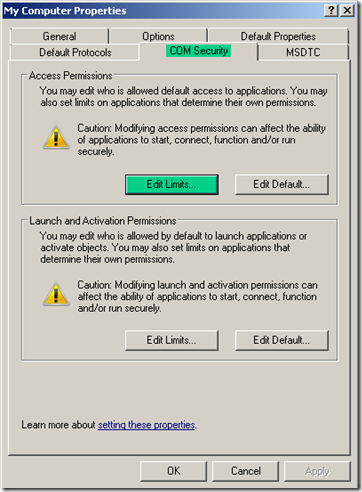
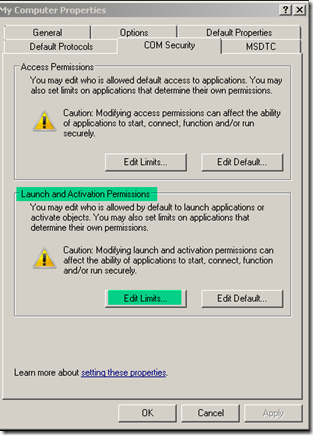
4. Check the COM Security tab for the following settings. The 'Edit Default' settings do not have to be modified.
On the COM Security tab, under Access Permissions, click Edit Limits.
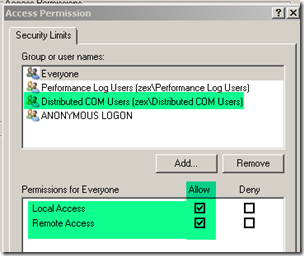
Verify that the “Distributed COM Users” group is allowed both Local Access and Remote Access permissions. This is the group where the DPM Server's machine account has been added. This group is available after SP1 for Windows Server 2003 is applied, and after Windows XP SP2 has been applied.
after checking "Edit Limits" you'll see
6. On the COM Security tab, under Launch and Activation Permissions, click Edit Limits.
Verify that the Distributed COM Users group is allowed the following permissions:
· Local Launch
· Remote Launch
· Local Activation
· Remote Activation
Be sure to run secpol.msc and make sure that local security policy is not preventing network access.
1. Check ‘User Rights Assignment’ to confirm that the DPM Server’s machine account
or authenticated users is specified here.
2. Make sure that “Deny access to this computer from the network” does not include
the DPM Server's machine account, Everyone, Administrators, or Authenticated Users
as these will prevent the DPM Server from connecting.
Troubleshooting Security is beyond the scope of this article, but for a good reference, check out:
909887 Error message when you try to view a Web site that is hosted on Internet
Information Server 6.0 by using anonymous access: "401.1 Unauthorized: Logon failed"
support.microsoft.com/default.aspx?scid=kb;EN-US;909887
If Agent issues have been preventing consistency checks and/or replication, you may need to now reboot, uninstall the DPMRA, reboot, and reinstall.
Authors:
Victor Reavis
Tom Acker
Microsoft Corporation Enterprise Support
Comments
Anonymous
May 29, 2009
I've tried all the troubleshooting steps you've outlined and still cannot get the DPM Agent to work on a Server 2008 domain controller. It seems like I've tried everything and I'm still getting Data Protection Manager Error ID 270.Anonymous
January 22, 2010
We had same problem and resolved it by adding DPM server object to Domain Admins group