UAG 2010 SP1: The New and Improved DirectAccess Features
We received some great feedback from customers about deploying DirectAccess in their organizations. One notable quote was “it works like magic!” Our customers also told us how we can make the product better by adding features and making existing features easier to manage.
After discussions and prioritization we are now proud to present the DirectAccess enhancements in service pack 1:
- One-time-password support including: Integrated RSA SecurID agent and support for other 3rd party RADIUS based OTP products
- Added optional settings in each step for advanced deployment scenarios
- Support for deploying DirectAccess Group Policy across multiple domains, and pre-created GPOs
- Support for the “I only want to manage my computers” scenario using integrated UAG UI
- Support for Force Tunneling scenario using integrated UAG UI
- Integrated NAP for simplified endpoint policy enforcement with simple “for dummies” setup of NAP+DA and integrated NAP troubleshooting tools included in Web Monitor
- Improved monitoring and troubleshooting
One Time Password Integration
We’ve been hearing this request a lot from customers and potential customers – so we’ve gone ahead and did it.
Server side
On the server side UAG now provides a choice between smartcards and OTP. We did this by adding support for OTP in the UAG UI as part of the UAG DA Wizard’s optional settings. UAG comes out-of-the-box with an RSA SecureID agent so you can be up and running in no time if you have SecurID tokens.
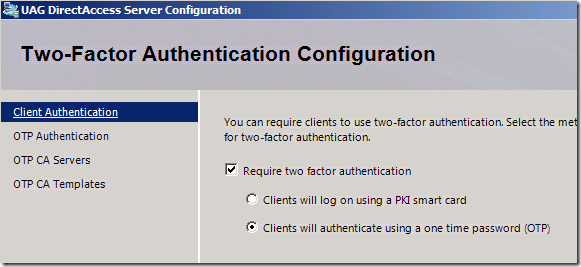
Figure 1: UAG DA UI with OTP
You can use OTP solutions from other 3rd party vendors as long as they are RADIUS based (OATH compliant).
Client side
On the client side the users are given the same experience and look & feel as the smartcard authentication “pop-up”. Our implementation is not based on credential provider so that requiring OTP for authentication in the UAG DA server UI does not enable the user to login to Windows on the client using an OTP token.
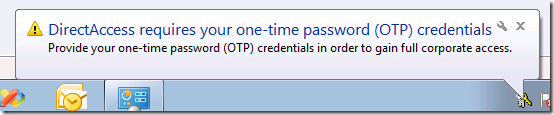
Figure 2: OTP authentication balloon
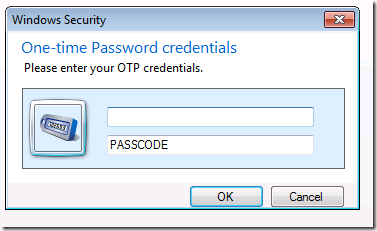
Figure 3: OTP authentication popup
Deployment
When deploying OTP you need to set up a dedicated Certificate Authority server (CA) and cannot use an existing CA. UAG makes life easier by generating a script which you can apply on the dedicated CA for use with OTP instead of performing CA configuration manually. Another bonus is that you do not need to make changes to the existing RSA ACE servers.
NAP Integration
NAP setup
NAP integration in UAG 2010 seemed easy enough. All you had to do was select a checkbox and NAP was enforced. In reality, there is more to it than that. Someone needs to install and configure an NPS, HRAs and CAs. This is not a simple task. In SP1 we decided to ask a few more questions, but have UAG do the bulk of the work for you. We did this by installing and configuring NAP roles on the UAG server, and by adding the NAP settings to the client GPO. You still need to set up a dedicated CA server and health template, and point to them in the UAG UI.
In the wizard you can choose between enforcing and monitoring health. If you select to enforce, client machines cannot create the second (intranet) tunnel until they can obtain a health certificate. Monitor only, on the other hand, will make sure that client health is checked and reported, but unhealthy clients will not be blocked.
NAP client health troubleshooting
Another non-trivial task that administrators face when using NAP is trying to understand why a particular client machine is considered unhealthy. Although the data exists, it is buried in the Windows EventLog and the actual events are not very clear. We’ve decided to add NAP troubleshooting to the UAG DA UI, specifically to the Web Monitor. You can query the last event for a specific machine, the last five events, or all of the events in a range of dates.
Existing NAP infrastructure
If you already have a NAP infrastructure or just want to have separate NAP and UAG servers, you can select not to use the internal NAP server, no questions asked. You then have to:
- Setup the NPS, HRA and CA server
- Create your own client GPO to turn on NAP client settings
- Use Event Viewer on your NPS server to troubleshoot client health problems
- Replicate the NPS configuration if you have more than one deployed
Integrated Multi Domain Support
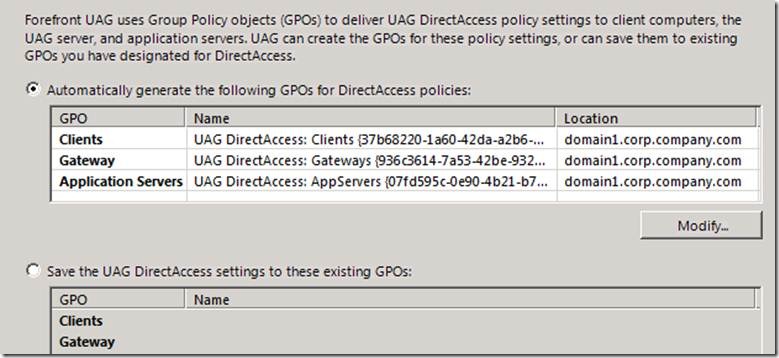
Many of our customers have more than one domain. We have added support for managing DirectAccess in a multi domain deployment.
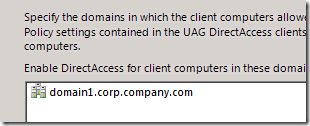
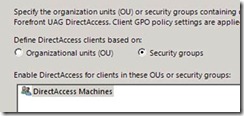
Using the UAG DirectAccess UI you can specify which domains the DirectAccess GPOs will be applied to. You can also specify which GPO the UAG will use, allowing for better role separation between the DirectAccess admin and the UAG admin. In addition, the GPOs can now be linked to OUs, not only to whole domains.
|
|
Figure 4: Selecting client computer domains |
Figure 5: Selecting OUs/Security groups |
Figure 6: Selecting Preconfigured/New GPO
Domain controller auto-discovery has also been extended to discover DCs across all selected domains.
Always managed
Some customers wanted to deploy DirectAccess for the purpose of managing remote client machines, but do not wish to have users connect to application servers on the intranet. Using a new setting located on the first page of the client wizard, the admin can now choose to enable only the first (infrastructure) tunnel, without enabling the second (intranet) tunnel.
Force tunneling
Some customers want to enable client machines to connect via DirectAccess, but while connected they do not want the clients to connect to anywhere else (i.e. creating a split tunnel). The UAG DirectAccess UI enables you to specify force tunneling in one of two flavors:
- Web-only through the intranet web proxy
- All traffic, using DNS64 and NAT64 to translate every IPv4 address returned in DNS
If you are thinking of utilizing this feature, please read Tom Shinder’s blog post (https://blogs.technet.com/b/tomshinder/archive/2010/03/30/more-on-directaccess-split-tunneling-and-force-tunneling.aspx) in full prior to deployment.
Improved monitoring and troubleshooting
Server side
Since UAG has a built in monitoring tool called Web Monitor, we’ve integrated DirectAccess information into it, providing a unified monitoring experience. The information is stored in an internal SQL database. You can display a list of currently logged on users, access level (infrastructure/intranet), NAP health status, machine account, user account and other fields.
At the array level, there is a “SCOM-like” health indication for each UAG array member. Everything is presented at the array level so that the admin can access all the information from the console of any node of the array.
The user monitoring PowerShell snap-in can now present the user and server monitoring information at the array-level, without enabling the Security auditing event logs.
Client side
DirectAccess Connectivity Assistant (DCA) is an application that runs on the DirectAccess clients. DCA enables the user to easily check the status of the DirectAccess connection to the corporate network and resources. It also provides troubleshooting features that will help in solving connectivity issues.
In SP1 you can centrally configure the DCA using the UAG DirectAccess UI. Configuration is propagated to clients via GPO. The DCA binary distribution is not done by UAG – you need to do it manually or automate it via GPOs, SCCM or other means.
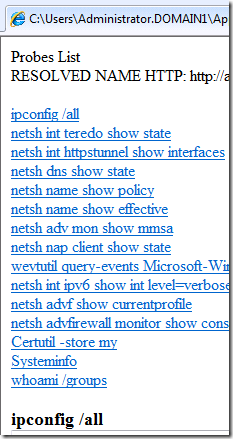
We’ve added 7 new diagnostics to DCA, E.g. “IPv6 is disabled on the client” and now provide an HTML based troubleshooting summary.
Figure 7: HTML Summary with Hyperlinks
We are excited about this new release and we encourage you to share with us any feedback you have.
Noam
Comments
Anonymous
November 17, 2010
Will it be possible to have more than one DirectAccess client GPO?Anonymous
November 17, 2010
Hi Tony. If you are using the predefined GPOs mode, it is possible to create multiple instances of the client GPO, one GPO for each domain. However, the GPOs must have the same name.Anonymous
November 30, 2010
Specifically we are looking to see if we can have two or more DirectAccess policies that could be applied to different groups of computers, in the same domain.Anonymous
November 30, 2010
Is there an expected date for UAG 2010 SP1 to be formally released?