Advanced Spam Filtering and X-CustomSpam
When a legitimate message is marked as spam, the first question usually asked is “why?” It can sometimes, but not always, be quite difficult to find the explanation. If an enabled Advanced Spam Filter (ASF) option has caused the spam detection, this will be called out directly in the header. In these cases, finding the “why?” is very easy!
Advanced Spam Filtering Options
Advanced Spam Filtering options, which are located in the Content Filter, allow you to increase the aggressiveness of the Exchange Online Protection spam detection engine. If one of the ASF options has caused a message to be marked as spam, there will be an additional header present in the message, X-CustomSpam.
X-CustomSpam
This header will spell out in plain text which ASF option caused the message to be marked as spam. If the X-CustomSpam header is not present in a message that was marked as spam, it means that an ASF option did not trigger and was not the reason for the spam detection.
Example: I enabled the ASF option “URL redirect to other port.”

I then sent a message which contained the link "https://www.contoso.com:123" in the body. This message triggered the above ASF in the Content Filter and caused the message to be marked as spam. Looking in the headers of this message I see the following.
X-CustomSpam: URL redirect to other port
This tells me exactly which ASF option caused the message to be marked as spam and I can now think about adding exceptions in place if the message was legitimate.
A complete list of X-CustomSpam entries can be found on TechNet at Advanced Spam Filtering Options.
Test Mode
Except for the last four ASF options, all other options have three configuration states. Off, On, and Test.
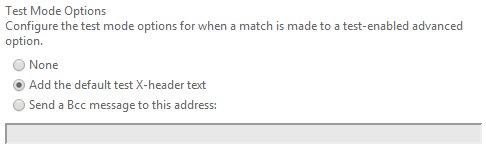
To configure how test mode works, scroll to the bottom of the ASF options window and you will see the following.
Test Mode will allow you to evaluate the impact that an ASF option without actually having it officially mark a message as spam. The “Add the default test X-header text” refers to the X-CustomSpam header and “Send a Bcc message to this address” is self-explanatory.
Best Practices
When educating customers on ASF options I often recommend the following.
When configuring EOP for the first time, don’t initially enable all ASF options as this can cause a large number of false-positives. Instead, leave the off and after evaluating mail flow, turn them on one at a time. I have found that the top four ASF options are the most prone to causing false-positives.
For organizations concerned about phishing, it is recommended to enable both SPF record: hard fail and Conditional Sender ID filtering: hard fail ASF options.
Before enabling an ASF option, when possible, put it in Test Mode to evaluate what impact it will have.