How to restrict RDP access in Windows Azure Virtual Machines
Recently, a Microsoft partner asked me how to restrict access by Remote Desktop to virtual machines hosted in Windows Azure.
In this post, I present the solution to the Partner's request.
Next sections introduce the request as submitted from the partner and the method to fullfill it.
Objectives
- Only one virtual machine accessible by RDP: this machine will be used to administer other virtual machines in the cloud
- Restrict RDP access only to authorized ip addresses
Scenario
The testing scenario is based on:
- A Windows Azure Virtual Network used for connecting virtual machines
o 1 Address Space 10.0.0.0/8
o 1 Subnet 10.0.0.0/24 named Subnet-1
- 3 Windows Azure Virtual Machines connected to subnet10.0.0.0/24. Windows Azure will offer DHCP and DNS services
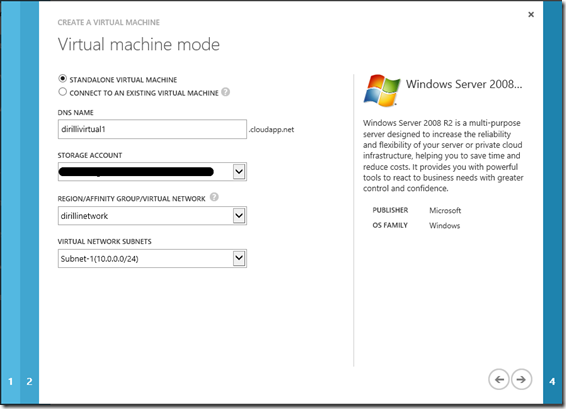
o Virtual Machine 1: Dirillivirtual1
o Virtual Machine 2: Dirillivirtual2
o Virtual Machine 3: Dirillivirtual3
- Each virtual machine is accessible by Internet or external network using endpoints: You can associate specific ports and a protocol to endpoints. Resources can connect to an endpoint by using a protocol of TCP or UDP. The TCP protocol includes HTTP and HTTPS communication.
In this example, we will create an endpoint for the TCP port 3389 (RDP) and we will associate it to virtual machine "Dirillivirtual3": no endpoints will be configured for the other virtual machines, Dirillivirtual1 and Dirillivirtual2.
Configuration
We will perform the following tasks:
- Virtual Network Configuration
- Virtual Machines creation: each VM will be connected to the virtual network created in the previous step
- Firewall configuration on "Dirillivirtual3" virtual machine to permit access by RDP from specific IPs
- RDP connections to Dirillivirtual1 and Dirillivirtual2 Creation from Dirillivirtual3 console
- RDP endpoints removal on Dirillivirtual1 and Dirillivirtual2 to prevent connections from external networks
1 Virtual Network configuration
In this section, we create the virtual network named "Subnet-1"
2 Virtual Machines creation
Each virtual machine will be connected to the virtual network "Subnet-1" created in the previous step.
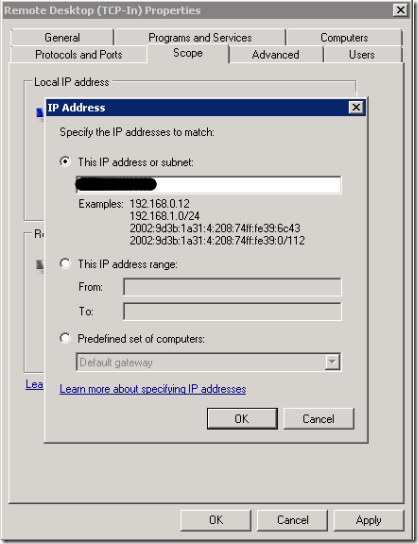
3 Firewall configuration
In this step, we will restrict access to "Dirillivirtual3" machine only to authorizaed IP addresses and configure RDP connections to "Dirillivirtual1" and "Dirillivirtual2" . An endpoint associated to RDP 3389 will be defined only on "Dirillivirtual3" .
You can administer "Dirillivirtual1" and "Dirillivirtual2" using Remote Desktops snap-in available on "Dirillivirtual3"
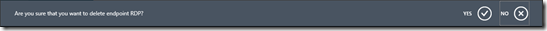
4 Endpoints Removal on "Dirillivirtual1" and "Dirillivirtual2"
The last step we will perform is to delete endpoints on "Dirillivirtual1" and "Dirillivirtual2" to prevent external access
Now, you can perform administrative task on windows Azure virtual machines using an unique access point
Francesco
![clip_image002[4] clip_image002[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/7103.clip_image0024_thumb_35D4BD25.jpg)
![clip_image004[4] clip_image004[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/7870.clip_image0044_thumb_6C626869.jpg)
![clip_image006[4] clip_image006[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/6283.clip_image0064_thumb_22F013AE.jpg)
![clip_image008[4] clip_image008[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/3122.clip_image0084_thumb_3962B235.jpg)
![clip_image012[4] clip_image012[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/7607.clip_image0124_thumb_76C2F0EF.jpg)
![clip_image016[4] clip_image016[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/6874.clip_image0164_thumb_317A73F9.jpg)
![clip_image018[4] clip_image018[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/7774.clip_image0184_thumb_5FA449E6.jpg)
![clip_image020[4] clip_image020[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/65/36/metablogapi/5001.clip_image0204_thumb_56680EA5.jpg)