Open Windows Firewall Ports for SQL Server the Easy Way
After installing a new SQL Server 2008 instance on my Windows 7 laptop I find myself unable to logon locally into the instance by using SQL Server Management Studio (SSMS). I know that due to the changes introduced in Windows Server 2008 and Windows Vista Firewall this was possibly due to an open port missing.
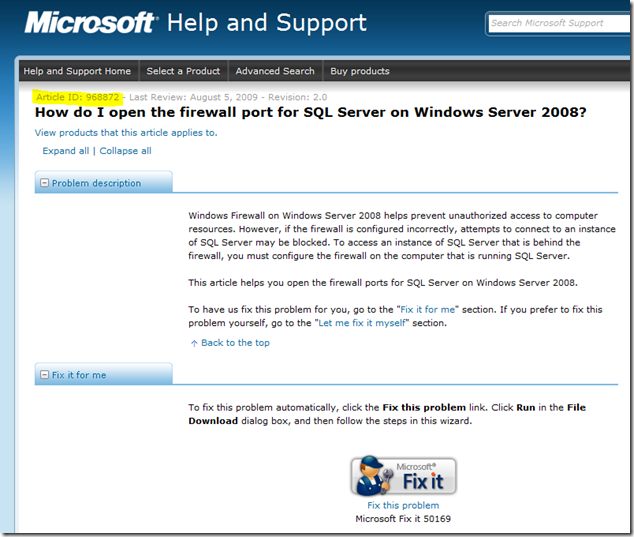
The Configuring the Windows Firewall to Allow SQL Server Access Books Online entry contains the information to open the required ports in Windows Firewall for each one of the SQL Server services. However, I recently discover a much easier way to open the required Windows Firewall ports for SQL Server on the following Knowledge Base Article (KB968872):
This article includes the Microsoft "Fix it" troubleshooter that allows to quickly fix the related problem using an easy-to-follow setup. The "Fix it" button is designed for Windows Server 2008 but the script that is executed by the setup is included on the same KB article and can be executed on Windows Vista or Windows 7 as well:
@echo ========= SQL Server Ports ===================
@echo Enabling SQLServer default instance port 1433
netsh firewall set portopening TCP 1433 "SQLServer"
@echo Enabling Dedicated Admin Connection port 1434
netsh firewall set portopening TCP 1434 "SQL Admin Connection"
@echo Enabling conventional SQL Server Service Broker port 4022
netsh firewall set portopening TCP 4022 "SQL Service Broker"
@echo Enabling Transact-SQL Debugger/RPC port 135
netsh firewall set portopening TCP 135 "SQL Debugger/RPC"
@echo ========= Analysis Services Ports ==============
@echo Enabling SSAS Default Instance port 2383
netsh firewall set portopening TCP 2383 "Analysis Services"
@echo Enabling SQL Server Browser Service port 2382
netsh firewall set portopening TCP 2382 "SQL Browser"
@echo ========= Misc Applications ==============
@echo Enabling HTTP port 80
netsh firewall set portopening TCP 80 "HTTP"
@echo Enabling SSL port 443
netsh firewall set portopening TCP 443 "SSL"
@echo Enabling port for SQL Server Browser Service's 'Browse' Button
netsh firewall set portopening UDP 1434 "SQL Browser"
@echo Allowing multicast broadcast response on UDP (Browser Service Enumerations OK)
netsh firewall set multicastbroadcastresponse ENABLE
Executing this on Windows 7 will show several warnings since the netsh firewall command in deprecated on this Windows version (netsh advfirewall firewall is the recommended method) but the script will perform its function nevertheless.
Kudos for the Microsoft "Fix it" team!
Comments
Anonymous
October 01, 2010
Thanks a bunch for posting this! Very helpful.Anonymous
October 07, 2010
Here is a version of the script I modified to use the new version of netsh. I'm stuck on the syntax of the final command so I had to leave it set to the old version. But if you are concerned about the 'depreciated' warnings this script resolves most of them. @echo ========= SQL Server Ports =================== @echo === THIS MUST BE RUN FROM AN ELEVATED COMMAND PROMPT! === pause @echo [ Using the new 'netsh advfirewall firewall' command ] @echo Enabling SQLServer default instance port 1433 :: DEPRECIATED - netsh firewall set portopening TCP 1433 "SQLServer (port 1433)" netsh advfirewall firewall add rule name="SQLServer (port 1433)" dir=in action=allow protocol=TCP localport=1433 @echo Enabling Dedicated Admin Connection port 1434 :: DEPRECIATED - netsh firewall set portopening TCP 1434 "SQL Admin Connection (port 1434)" netsh advfirewall firewall add rule name="SQL Admin Connection (port 1434)" dir=in action=allow protocol=TCP localport=1434 @echo Enabling conventional SQL Server Service Broker port 4022 :: DEPRECIATED - netsh firewall set portopening TCP 4022 "SQL Service Broker (port 4022)" netsh advfirewall firewall add rule name="SQL Service Broker (port 4022)" dir=in action=allow protocol=TCP localport=4022 @echo Enabling Transact-SQL Debugger/RPC port 135 :: DEPRECIATED - netsh firewall set portopening TCP 135 "SQL Debugger/RPC (port 135)" netsh advfirewall firewall add rule name="SQL Debugger/RPC (port 135)" dir=in action=allow protocol=TCP localport=135 @echo ========= Analysis Services Ports ============== @echo Enabling SSAS Default Instance port 2383 :: DEPRECIATED - netsh firewall set portopening TCP 2383 "Analysis Services (port 2383)" netsh advfirewall firewall add rule name="Analysis Services (port 2383)" dir=in action=allow protocol=TCP localport=2383 @echo Enabling SQL Server Browser Service port 2382 :: DEPRECIATED - netsh firewall set portopening TCP 2382 "SQL Browser (port 2382)" netsh advfirewall firewall add rule name="SQL Browser (port 2382)" dir=in action=allow protocol=TCP localport=2382 @echo Enabling port for SQL Server Browser Service's 'Browse' Button :: DEPRECIATED - netsh firewall set portopening UDP 1434 "SQL Browser (port 1434)" netsh advfirewall firewall add rule name="SQL Browser (port 1434)" dir=in action=allow protocol=TCP localport=1434 @echo ========= Misc Applications ============== @echo Enabling HTTP port 80 :: DEPRECIATED - netsh firewall set portopening TCP 80 "HTTP (port 80)" netsh advfirewall firewall add rule name="HTTP (port 80)" dir=in action=allow protocol=TCP localport=80 @echo Enabling SSL port 443 :: DEPRECIATED - netsh firewall set portopening TCP 443 "SSL (port 443)" netsh advfirewall firewall add rule name="SSL (port 443)" dir=in action=allow protocol=TCP localport=443 @echo Allowing multicast broadcast response on UDP (Browser Service Enumerations OK) :: NOTE While the following command will return a 'netsh is depreciated' warning, it still works. :: I could not find any reference to the correct syntax in 'netsh advfirewall' so I left the original command netsh firewall set multicastbroadcastresponse ENABLE :: NOTES :: The original version of this script came from: support.microsoft.com/.../968872 :: Although it used the depreciated 'netsh firewall' commands. You can find the updated 'netsh advfirewall firewall' :: command info here: support.microsoft.com/.../947709 :: NOTE: The 'set' command operates on existing rules. The 'add' command (and somehow the 'new' command) created new rules. :: This page: support.microsoft.com/.../287932 explains the details of a SQL connection and which ports are used for what. :: Finally, here is a great command reference on the new version: http://ss64.com/nt/netsh.htmlAnonymous
October 07, 2010
(This comment has been deleted per user request)Anonymous
October 29, 2010
The comment has been removedAnonymous
March 15, 2011
When I try to use this tool, I get an error saying that Microsoft FixIt does not apply to your operating system or Application version. I am using a 64 Bit version of Windows 7. Can you please tell me what I am doing wrong?Anonymous
March 15, 2011
(This comment has been deleted per user request)Anonymous
July 27, 2011
Thanks, I love you! :)))))))Anonymous
October 17, 2011
Props to the Fix It team AND to Robert who posted the updated version. Awesome! Simply, elegantly awesome. Thanks a million for a quick script that worked like a champ and saved me some keystrokesAnonymous
October 24, 2011
I'm assuming this fix also applies to 2008 R2 as it worked for me.Anonymous
March 26, 2012
@echo ========= SQL Server Ports =================== @echo Enabling SQLServer default instance port 1433 @netsh advfirewall firewall add rule name="SQLServer" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=1433 remoteport=any protocol=tcp interface=any @echo Enabling Dedicated Admin Connection port 1434 @netsh advfirewall firewall add rule name="SQL Admin Connection" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=1434 remoteport=any protocol=tcp interface=any @echo Enabling conventional SQL Server Service Broker port 4022 @netsh advfirewall firewall add rule name="SQL Service Broker" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=4022 remoteport=any protocol=tcp interface=any @echo Enabling Transact-SQL Debugger/RPC port 135 @netsh advfirewall firewall add rule name="SQL Debugger/RPC" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=135 remoteport=any protocol=tcp interface=any @echo ========= Analysis Services Ports ============== @echo Enabling SSAS Default Instance port 2383 @netsh advfirewall firewall add rule name="Analysis Services" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=2383 remoteport=any protocol=tcp interface=any @echo Enabling SQL Server Browser Service port 2382 @netsh advfirewall firewall add rule name="SQL Browser" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=2382 remoteport=any protocol=tcp interface=any @echo ========= Misc Applications ============== @echo Enabling HTTP port 80 @netsh advfirewall firewall add rule name="HTTP" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=80 remoteport=any protocol=tcp interface=any @echo Enabling SSL port 443 @netsh advfirewall firewall add rule name="SSL" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=443 remoteport=any protocol=tcp interface=any @echo Enabling port for SQL Server Browser Service's 'Browse' Button @netsh advfirewall firewall add rule name="SQL Browser" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=1434 remoteport=any protocol=udp interface=any @echo Allowing multicast broadcast response on UDP (Browser Service Enumerations OK) @netsh advfirewall firewall add rule name="SQL Browser" dir=in action=allow enable=yes profile=domain localip=any remoteip=any localport=1434 remoteport=any protocol=udp interface=any @netsh advfirewall set currentprofile settings unicastresponsetomulticast enable pauseAnonymous
September 11, 2012
Thank you!!!!!!!!!!!!! worked perfectly.Anonymous
November 19, 2012
The comment has been removed