Take Control of Your Privacy
1 to 7 May 2011 is Privacy Awareness Week. It’s a great time to take a few moments to look at simple things we can all do to look out for our own personal privacy in our day to day computing.
Your privacy matters, and if you want to stay in control, there may even be some new tricks to learn.
The simplest way to control your information is to be careful about how and when you give it out. Never give your passwords to strangers, always type in web addresses for banks and online services yourself rather than following links (which could conceal a scam), and be aware of scammers who are out to trick people into giving up personal information and credit card details in all sorts of underhand ways.
A little net savvy goes a long way!
The focus of this article is on some simple steps you can take as a home user to control the information you do choose to share. It’s to help make sure you’re the one pulling the strings with:
- Your Personal Computer
- Your Web Browser
- Your Wireless Home Network
- Your Personal Internet “Cloud”
- Your Toys and Gadgets
This blog post covers each of these in turn.
This article provides a checklist, but doesn’t provide step-by-step instructions. So, if you’re not sure how to carry out any of the steps described here, ask for help from a professional, a tech savvy friend, or an online community.
Your Personal Computer
The first thing to be sure of is that your personal computer really all yours, without any malicious software that could be collecting information about you. Simple steps to take:
- Make sure your software is up to date with security patches, and set to automatically stay that way.
In Windows 7, that means a visit to Windows Update. Once you’ve done the updates there, check for updates for any other software you have installed. For example: Web browsers, Adobe PDF Reader and Adobe Flash, your anti-virus software, iTunes and Java. If the software doesn’t have a way to check for updates (often in the Help or Tools menu), check the website of company that made it for a newer version. Secunia has a complimentary tool to help you keep up to date.
- Run a full virus scan of your computer.
If your anti-virus software has expired or you don’t have any, try the complimentary Security Essentials anti-virus and anti-spyware software from the Microsoft website. A full scan can take a couple of hours, so if you don’t want it to get in the way of your computing you can start it just before bed time.
- Consider using standard user accounts , parental controls and/or a household agreement about installing only trusted software to keep your computer safe.
Beware of scams that try to get personal information out of you, or pressure you into installing and paying for software to remove viruses or enhance computer performance. Many of these scams will try to scare you by saying there some sort of problem with your computer, or entice you with something that’s too good to be true. They try to get to you through websites, email, or even a call to your phone. Don’t fall for it. Make sure that you only install software from websites you can trust. If you are ever unsure, you can do a free check of your Windows PC.
If you’re using a computer that you don’t know you can trust, think twice about entering passwords or other personal information. If the computer is infected with malicious software, you could be sending your personal information to a criminal without knowing. Some services provide temporary passwords that you can use on unfamiliar computers, and you should use this option whenever you can. Otherwise, if you must use a computer you are not sure you can trust, be sure to change your passwords as soon as possible when you have access to a trusted computer.
Your Web Browser
Now that you have peace of mind about what’s on your computer, turn your attention to one of the most important computer programs you have: Your web browser.
Use it right, and it’s a powerful tool. With great power, comes great responsibility!
What you do in your web browser is often tracked across many websites, even if you use “private” browsing or delete your cookies regularly. This tracking often happens without people realising it, because most web browsers automatically download all sorts of bits that can be used for tracking from many websites other than the one people think they are visiting.
Internet Explorer 9 is the only web browser that gives you built-in control over this type of tracking, so if you want to enhance private browsing with a minimum of fuss we suggest you upgrade to Internet Explorer 9, then add a tracking protection list.
Here are some more tips for using Internet Explorer 9 features to keep yourself private.
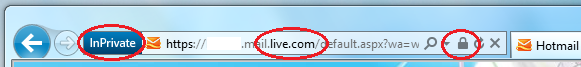
- If your family shares a trusted PC without separate user accounts, use InPrivate browsing so that your passwords and browsing history don’t get stored on the PC. Just hit CTRL-SHIFT-P to start an InPrivate browsing session, and close the web browser when you are done. You can see you’re “InPrivate” in the address bar (left circle below).
- If you ever use unsecured networks, get in the habit of typing in https:// (with an “s”) any time you are going to enter a password or personal information. For example, https://hotmail.com or https://facebook.com. Check your web browser to make sure the connection is secure (encrypted) before you type in any password or personal information. This is shown with a “lock” in the address bar (right circle below). If you don’t do this, anyone else on the same network as you could watch much of what you are doing.
- Check that you recognise the domain name and trust it. In modern web browsers this is highlighted to make it easier to see (middle circle below).
If you’re following all three of the steps above, your address bar in Internet Explorer 9 would look like something like this when you’ve securely logged in to Hotmail (live.com):
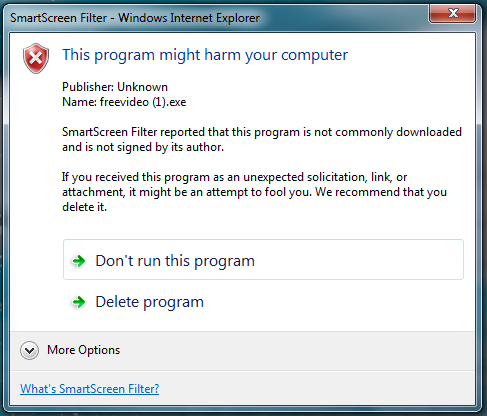
- Internet Explorer 9 has an in-built SmartScreen Filter that provides warnings about suspected malware and phishing attacks. It is also the only major web browser with an integrated download filter that checks the reputation of program files that you download. Keep an eye on any warnings that Internet Explorer 9 gives you about websites visit or files you download.
An example of this protection in action is shown below:
Your Wireless Home Network
That’s two pieces of the privacy and information security picture in place. If you have a wireless home network, it’s critical that you’re trust everyone who’s using it. Otherwise you could find that someone parked in the street outside is using up your limited monthly Internet allowance, watching your online activity, or even doing something illegal using your wireless network that could get you in hot water.
All wireless networks should be:
- secured with at least Wi-Fi Protected Access (WPA),
- given a unique access point (network) name, and
- protected with a strong password.
If you’re concerned that your wireless home network is not secure, or you would simply like to update the password to make sure only authorised people have access, you need to configure the wireless modem, usually by typing a special address for its control panel into your web browser.
The user manual for your wireless modem will have instructions for how to access the control panel. If you can’t find the instructions, try looking your wireless modem’s model number (usually on the modem itself) on the manufacturer’s website. If you don’t feel confident about this, it’s best to ask a professional (or a trusted tech savvy friend) to help.
Once you are in the control panel, choose the best security that is supported by every computer and gadget that connects to your wireless modem. Gadgets that are less than three years old probably support WPA2 encryption, but it’s worth checking each of them first to be sure. Changing the name of the wireless access point (the name of the wireless network) to something quirky or unusual is recommended, and go for a long password (say, 40-60 random characters). The password can be generated quickly (just combine three of these random strings into one password), but be sure to write it down carefully somewhere secret, or keep it safely on a USB data stick or computer in your house for when you need it.
Finally, you’ll need to re-connect each computer and gadget to newly named wireless network using the new password.
Make sure you have a reliable way to remember your new password.
Your Personal Internet “Cloud”
Your personal computer, your web browser and your home network are the foundations and they need to be in shape. But you probably use a webmail services like Hotmail, social media sites like Facebook, and services like SkyDrive to store documents and photos in the cloud. In fact it’s hard to imagine being without them. Unfortunately people’s accounts are compromised all too often, exposing their most personal data and that of their friends. And it doesn’t need to happen.
Take a few moments to make sure you’re in complete control of your personal “cloud”.
Here are steps to take for each of your online accounts, from a trusted personal computer:
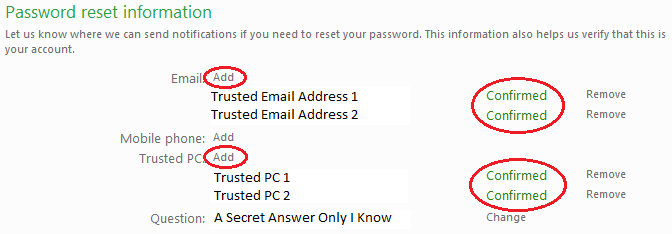
- Log in to your online account and make sure you have securely configured as many account password recovery options as possible.
For example, in Hotmail you would click on your account name in the upper right corner, choose Account, and then set at least one trusted email address for password resets, and at least one Trusted PC (example below). Make sure you go through all the necessary steps so that these show up as Confirmed (as shown below). Taking these simple steps will make it so much easier to get back control of your account if anyone ever gets unauthorised access.
- Check your privacy settings to make sure you are only sharing what you want to.
For example, in Hotmail you would click on your account name in the upper right corner, choose Privacy Settings, and choose the settings you prefer. In many services there is an Advanced option which is probably worth a look if you want more precise settings.
- Update your passwords regularly, at least once a year. Passwords are like a good story about a magical ring: They should be mysterious, and they should be kept secret, and safe.
You should have a different password for each service you use. Weak passwords are short, or contain words, names, dates or obvious sequences of numbers. Try to avoid these mistakes in your passwords.
- Strong passwords are long (ideally at least 14 characters), and ideally random. One technique for creating good passwords is to memorise a sentence with more fourteen words, and then to create password from the first letter of each word.
For example, I could choose a sentence like ,“I am feeling great about my online privacy with this new password for SkyDrive online storage.” This could become a password like iafgamopwtnpfsos and then to add a small twist I might tweak it like this: !@fgm0pwtnpfSOS . Now that’s quite hard for someone else to guess, but quite easy for me to remember. And don’t use this password – take a few minutes to create your own!
Make sure you have a reliable way to remember all your new passwords.
Your Toys and Gadgets
If you’ve done all that you should be feeling a lot better about your privacy. But if you’ve got toys and gadgets that connect to the Internet, there’s still a bit more to do. If you have a smartphone, say, the snazzy new Windows Phone 7, or you have an Xbox 360 entertainment system, bear with us a just a little longer. 
Toys and gadgets that connect to the Internet use information in new ways to deliver services to you, and they give you choices about the way your information is used. Just be sure to check you’re happy with the settings.
If you want them to, modern game consoles can tell your friends when you’re playing and what. They provide online stores that let you rent videos and buy games without getting up from your couch. And with a Kinect sensor, you can also upload priceless videos of yourself jumping around your living room that will have anyone who sees them rolling on the floor laughing. This is lots of fun, and when we think you might be uncomfortable the default is not to share, but know that you are in control and can change these settings at any time for the Xbox 360 itself and the Kinect sensor.
Smartphones are a hub of activity, and they have the potential to collect an enormous amount of information about what we do, and where we do it. But if you’ve ever lost a smartphone, you’ll probably agree it’s a really good idea to lock access to your smartphone with a pin. Another great thing smartphones offer is location based services, which can be extremely helpful. However, be sure that you understand how the phone and the applications you install on it are using information about your location. Make sure you’re not sharing more than you feel comfortable with.
Additional Resources
- Privacy Commission (New Zealand)
- NetSafe (New Zealand)
- Ministry of Consumer Affairs – Scamwatch (New Zealand)
- Microsoft Safety & Security Centre
- Privacy Settings in Microsoft products and services
- Family Settings in Microsoft products and services
Community Support
If you would like help to carry out any of the steps described here you could try asking a tech savvy friend, or experts on an online forum like the New Zealand PCWorld Press F1 community or the Microsoft Answers community.
Comments
- Anonymous
April 28, 2011
A great post that sums up every step you should take to stay safe online - the Trusted PC step on Hotmail was news to me and the smartphone security tips for Windows Phone 7 much appreciated, we'll let our helpline callers know about this resource. Chris @ NetSafe