How to Perform an Authoritative System State Restore in SBS 2008/2011 Standard
[Today's post comes to us courtesy of Shawn Sullivan from Commercial Technical Support]
If you have ever been in the situation where you had to recover an Active Directory object that was accidentally deleted within a multiple Domain Controller environment, then you are probably somewhat familiar with the term “authoritative restore” and what it does. This link gives a pretty in-depth look at the procedure, however, some important points I want to call out on this post are:
- An authoritative restore is used if you are recovering objects from Active Directory that have either been deleted or changed and you need to restore those objects to their previous state.
- An object change or deletion will replicate to the other Domain Controllers in your network.
- The state of the object in the backup is considered “out-of-date” unless you specifically mark the restore of this object as authoritative.
- If you restore the system state and boot the server into normal mode before you mark the object for an authoritative restore, you will find that the object is once again changed or deleted when the server receives inbound replication from its partner.
- Be as specific as possible when targeting the objects that you intend to restore. For example, if you simply need to recover a deleted user account, don’t mark the entire OU that contains it for an authoritative restore. Just mark the user account itself.
- Avoid unnecessarily or undesirably reverting any objects to their previous state that are not related to the deletion. You could inadvertently restore attributes like passwords, profile paths, and group memberships that may no longer be valid.
- Minimize the amount of data requiring replication across the network.
- If you are recovering a Domain Controller from a full or system state backup and wish to restore it back into the domain without making any changes to the state or content of the domain, then you should not perform an authoritative restore.
- This is usually in scenarios where something other than Active Directory needs to be recovered on a Domain Controller. For example, a server with a corrupted file system or failing hardware.
- In this scenario, a healthy copy of Active Directory in the desired state still remains within the other Domain Controllers in the network. When the Domain Controller is restored, its copy of Active Directory will be brought up to date when it receives inbound replication from its partner.
Scenarios where you would mark the entire copy of Active Directory as authoritative are rare and the situation is most likely catostrophic. If you believe you might be in a situation like this, you should probably contact Microsoft Product Support Services for troubleshooting assistance.
Performing an authoritative restore of objects in Active Directory can become a very complicated proposition, depending on what it is that you intend to recover. There are just too many variables and different situations you could find yourself in to cover in one comprehensive article. However, to give you a good idea of the whole process, we will go through the common scenario where you wish to restore a single user account to its complete original state.
Note: There are tools, such as ADRestore, that can pull a deleted object out of its tombstone and place it in its previous location. However, certain attributes that are stripped from the object when it was deleted cannot be restored by such tools; for instance passwords and group memberships for user accounts. A tool like ADRestore is meant to be used if you do not have system state backup, not as a replacement for a system state backup.
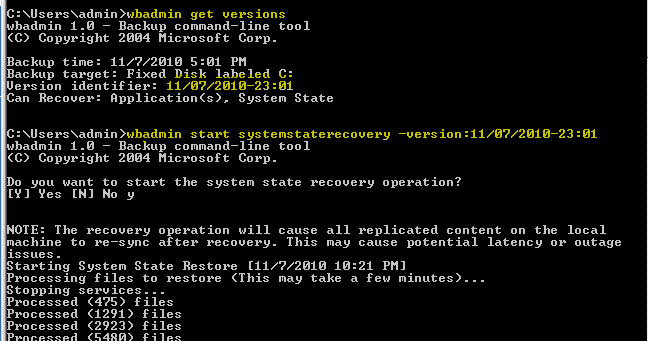
- Boot the SBS server into Directory Services Restore Mode and restore the system state backup with your chosen backup application:
After the POST, press F8 to enter the advanced boot options, choose Directory Services Restore Mode
Concerning the username and password that you will use to login to the server after it has booted into DSRM, review the following post
If you have taken your backup using SBS Backup or Windows Server Backup, review the following post. Here I have used wbadmin to obtain the ID for my available system state backup and to begin the restore procedure:
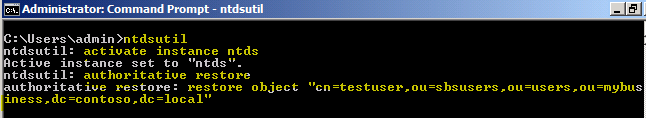
- Before you boot into normal mode, launch NTDSUTIL and mark the user account you wish to recover for authoritative restore:
Activate the NTDS instance: Activate Instance NTDS (see below).
Enter the Authoritative Restore context (see below).
Mark the object for authoritative restore: Restore Object “cn=username,ou=organizational unit,dc=domain,dc=local” (see below).
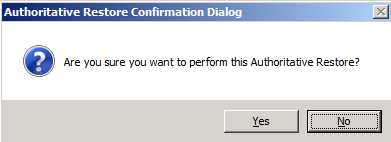
Click Yes to confirm
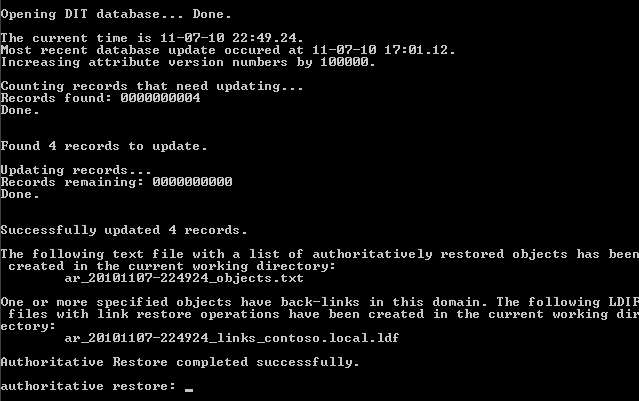
Note: The .txt. and .ldf files that are created during the restore process (see the output above) are for use in situations where you are recovering users and security groups that may have been migrated at some point in time from SBS 2000. For an explanation on this, see the sections “LVR and Restoration of Group Memberships” and “Files for Recovering Group Memberships Following Authoritative” under the following technet article : https://technet.microsoft.com/en-us/library/690730c7-83ce-4475-b9b4-46f76c9c7c90
You can see from the output that the attribute’s version number was incremented by 100000, which essentially make it more up-to-date as compared with what the remaining Domain Controllers have for this object. You can also see that 4 records were updated, this is the security group membership held by the account that I had deleted. In a simple recovery of a single user account, we do not have to take any further action at this point other than rebooting the server into normal mode.
New for SBS 2011 Standard
Windows 2008 R2 introduces a new feature called the AD Recycle Bin, which allows you to restore a deleted object in its entirety without having to go through the process I just talked about. This can save you quite a bit of time, but there are some caveats:
- This is not enabled by default on SBS 2011 Standard.
- To enable this feature, you must raise the forest functional level to Windows 2008 R2. This means you cannot have any domain controllers running Windows 2008 and earlier in the SBS domain.
- There is no simple GUI interface for this feature. You have to go through either LDP.exe or PowerShell to use it.
- This is not a replacement for system state backups. This is for recovering individual objects only, not the entire server.
You can find a step-by-step walkthrough at the following link, this covers everything from raising the functional level to performing a restore: https://technet.microsoft.com/en-us/library/dd392261(WS.10).aspx
Comments
- Anonymous
March 31, 2011
The comment has been removed - Anonymous
April 03, 2011
So the latest patches from MSFT suddenly have rendered my system usless. Similar issues to the 3 of 3 problem, then it then just dies. Restore to last known good doesn't work. Thanks. Here we go with a reinstall.