Use POSTMan and AAD app to get data from SharePoint Online using Graph API
This post is a contribution from Mustaq Patel, an engineer with the SharePoint Developer Support team
If we want to do a quick check if the AAD app is working against SharePoint Online using Graph API, we can use postman to set this up quickly. This blog post will demonstrate how to use Graph API with grantType = Authorization code. The blog post will also show how to use version 2.0 OAuth2 endpoint URLs.
For using REST API with POSTMan, please follow the below steps. It also shows how to use Client Credentials grant type.
Using OAuth 2.0 AAD App to retrieve data from SPO site using Graph
Step1:
Register your AAD app using apps.dev.microsoft.com or by directly browsing Azure Active Directory that is associated with SharePoint Online Tenant. My registration looks like below using https://apps.dev.microsoft.com
- Give app a name. Generate new password and copy it somewhere.
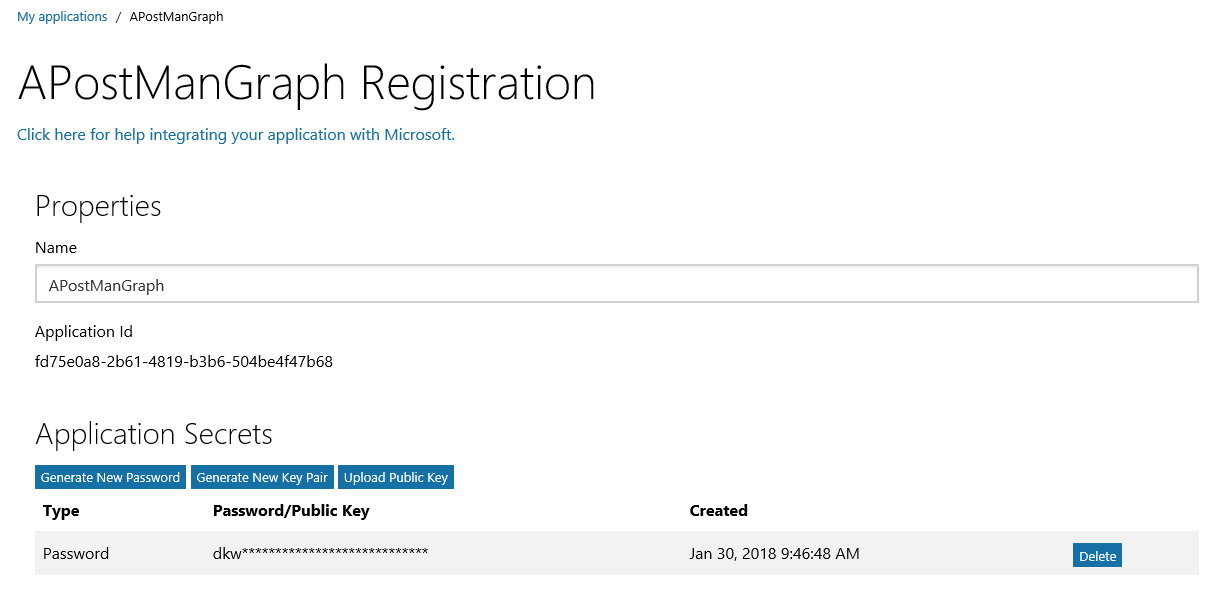
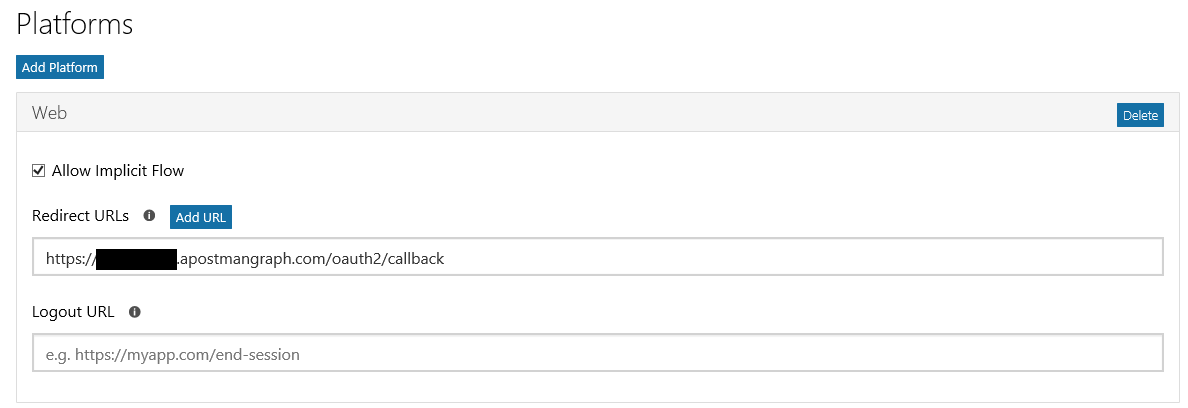
- Click Add platform and Select Web. Add Redirect url which needs to be unique. Please note that after .com it should be /oauth2/callback for postman to work. I normally give https://spotenantname.apptitle.com/oauth2/callback
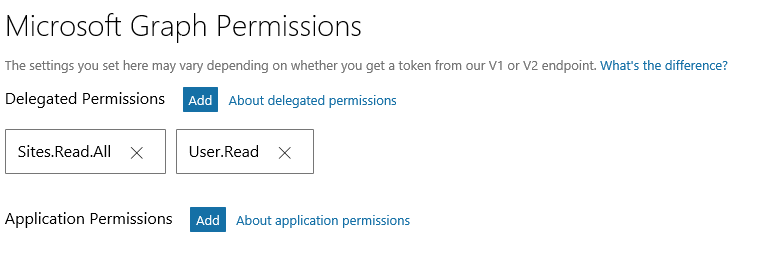
- Give permission to the app. Give delegated permission to Microsoft Graph and select Sites.Read.All
- Save. The app registration is complete. Keep ApplicationId, password which you copied in #1 and redirecturl for later use in postman.
Notes:
The permission you request will differ as per what you are retrieving from SPO. For now I am giving Sites.Read.All which will give read permission to the app on all sharepoint sites.
Step 2:
- Install latest PostMan (standalone version v5.5.2) from https://www.getpostman.com/apps.
- Open postman click Authorization and select OAuth 2.0. Click “Get New Access Token”.
- Input values as below.
Callback Url – this should be the redirect Url we copied from app registration
Auth Url – should be https://login.windows.net/common/oauth2/authorize?resource=https%3A%2F%2Fgraph.microsoft.com
Note the resource value is encoded and is https://graph.microsoft.com
Cliend Id – is the application Id we copied during app registration
Client Secret – is the password we copied during app registration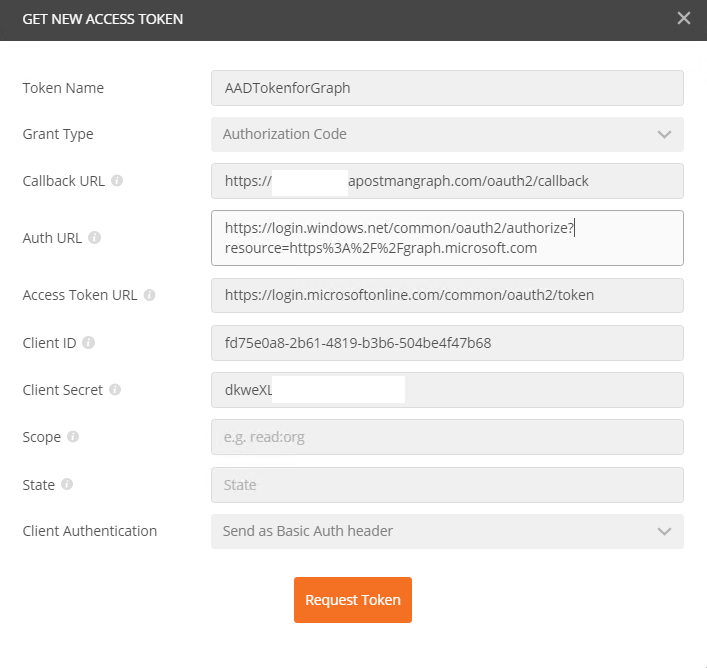
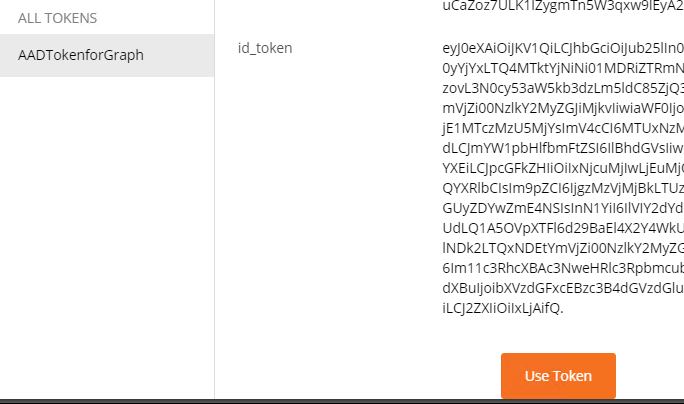
- Click Request Token. This will ask you to authenticate to your SPO Site and will give you App Consent UI to trust the App. Accept the permissions. Now you can see id_token generated, scroll all the way below and click use token. You may have to cancel the popup 2, 3 times to go to main postman window.
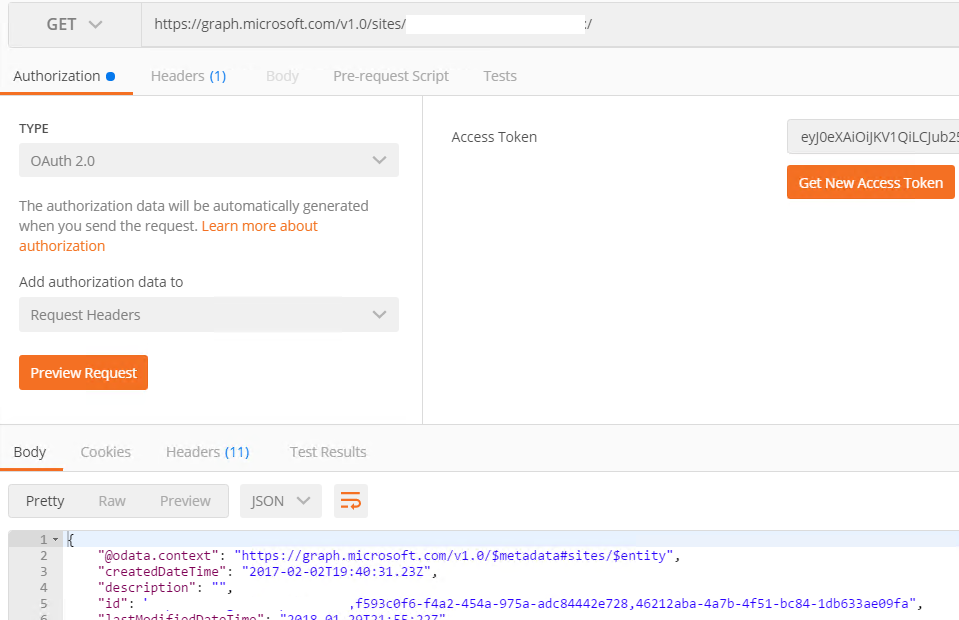
- On main postman screen. Provide the Graph Request Url, Select GET operation and click Send. If successful, we should see body showing response from the server like below. For testing we are getting site details by using below Graph request (tenantname will be as per your tenant)https://graph.microsoft.com/v1.0/sites/tenantname.sharepoint.com:/
- Below are few graph requests that you can tryGet particular site details (/sites/TeamSite is the path that I am requesting)
https://graph.microsoft.com/v1.0/sites/tenantname.sharepoint.com:/sites/TeamSiteGet listitems for a list from root site
https://graph.microsoft.com/v1.0/sites/tenantname.sharepoint.com/lists/DA53F478-07C8-4E10-AD26-76D64347ADDF/itemsGet listitems for another site
First get that site id by below request
https://graph.microsoft.com/v1.0/sites/tenantname.sharepoint.com:/sites/TeamSitecopy the entire id value and replace siteid below
https://graph.microsoft.com/v1.0/sites/siteid/lists/10FE61F7-EE89-4D86-A8FB-33DA455FAC2D/items
Using OAuth 2.0 version 2 endpoints to retrieve data from SPO site using Graph
For using oauth2 version 2.0 endpoint urls and use graph, the steps are exactly same as above, except the step where we get AccessToken, we have to use Scope and AuthUrl, TokenUrl will change.
Also, please note that 2.0 endpoint urls only support graph APIs and that means for SharePoint it is very limited.
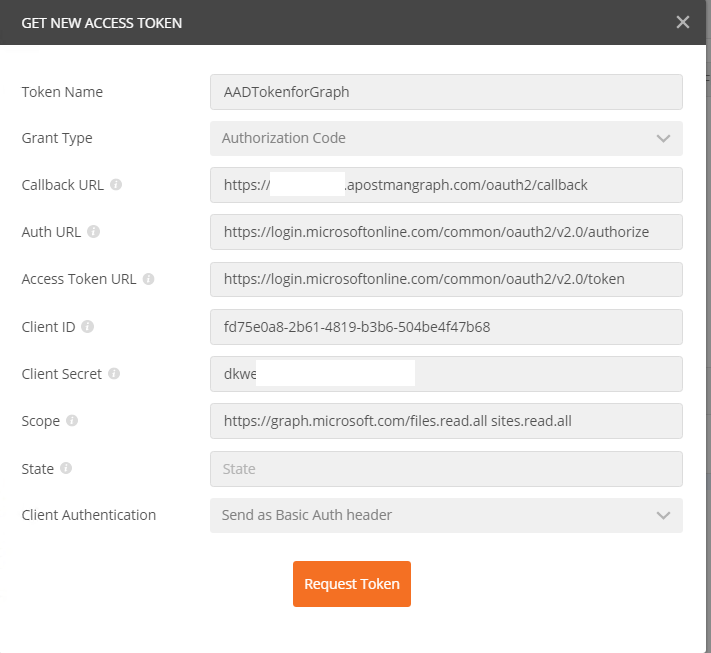
Using same above appregistration, here is my request to get AccessToken using oauth2 version 2.0 urls
Callback Url - this should be the redirect Url we copied from app registration
Auth Url – this should be https://login.windows.net/common/oauth2/v2.0/authorize
Access Token Url – this should be https://login.microsoftonline.com/common/oauth2/v2.0/token
Scope – List of scopes / permissions example https://graph.microsoft.com/files.read.all sites.read.all
Main difference between v2.0 urls and older once are below
Auth Url
V1 = https://login.windows.net/common/oauth2/authorize?resource=https%3A%2F%2Fgraph.microsoft.com
V2= https://login.microsoftonline.com/common/oauth2/v2.0/authorize
Token Url
V1 = https://login.microsoftonline.com/common/oauth2/token
V2 = https://login.microsoftonline.com/common/oauth2/v2.0/token
Scope
V1 = not needed
V2 = https://graph.microsoft.com/files.read.all sites.read.all (multiple permissions separated by spaces. We can only have 1 scope which is https://graph.microsoft.com)
Note - Getting access token for calling SharePoint APIs will use the same mechanism. The resource will change to "https://<tenant>.sharepoint.com". The app needs to be registered on https://portal.azure.com and should have permissions on the O365 SharePoint Online.
Comments
- Anonymous
February 06, 2018
help - Anonymous
June 04, 2018
Very much helpful.