Keeping Private Documents Private
When I share an email or a document with a colleague and ask for their confidentiality, I trust that they won’t share the information with others. Yet information that is particularly business- sensitive tends to be quite interesting, so we learn in the press when people are tempted to break the rules. For instance, last year Ad Age received leaked documents revealing advertising spending for Google’s largest customers. While Microsoft is not immune to leaks from personnel, it provides customers and employees with technology they can implement to guard email messages and documents from exposure beyond the intended audience.
Information Rights Management
Information Rights Management (IRM) is similar to Digital Rights Management for documents and information. With IRM, users can restrict rights to content and prevent authorized recipients of restricted content from forwarding, copying, modifying, printing, faxing, or pasting the content. Via IRM, Windows users can even prevent restricted content from being copied with Print Screen.
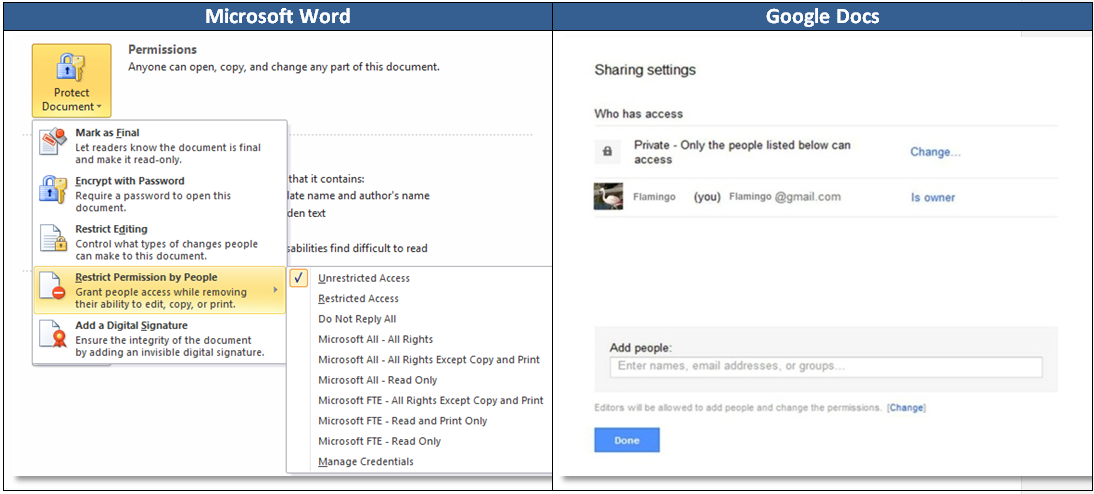
Let’s take a look at controlling access to Microsoft Word documents in the image below. In Word, I can use permission rights to limit document viewing to company staff. I can set permissions which prevent recipients from forwarding, copying or printing a document, and I can restrict a document so that only full-time employees can access it. Not only that, each Office application has the ability to apply similar restrictions.
Google Docs does not have Information Rights Management. In fact, the window for leaks is wide open in a Google environment! Google Docs allows users to specify who they want to share a document with online, yet users cannot apply any security settings to the document. Other users can download and share it any way they wish. In addition, if a user is working in a Google Apps domain, their files adopt the domain’s security setting, by default, whether those settings are private or not, so Google Apps users may be sharing or publishing documents without knowing they are doing so!
Controlling Document Access with Microsoft Word versus with Google Docs
“More Security Loopholes Found in Google Docs” and “Is Google Docs Secure Enough for Your Company’s Data?” reveal additional risks. Since Google Docs stores images with separate URLs, the images are available to anyone who knows the URL, regardless of whether the owner has given them permission to view the image, has revoked the user’s rights to it, or has deleted the image. Knowledgeable users can even change the revision number in the URL to access older versions of the image. Should an image be sensitive, such as a graph of company budgets or losses, the information could easily become very public, damaging the firm’s reputation. However, Google reviewed these security holes stating “We believe that these concerns do not pose a significant security risk to our users.” Google doesn’t seem to take security for Google Docs images very seriously.
Managing Rights for Email
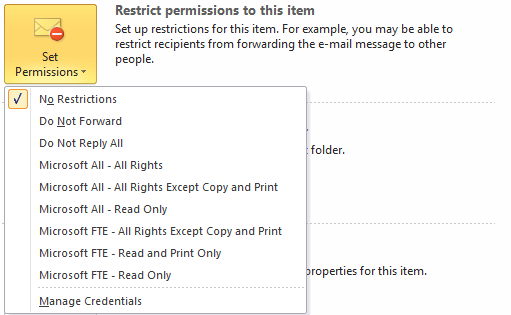
Microsoft also enables IRM for email. You can restrict access to email through Exchange via a set of permissions which are very similar to the permission settings in Office. You can identify the specific rights you want to allow or disallow. For example, to reduce risk and liability you can implement IRM so that staff can’t forward private, corporate messages outside the company without permission. Your business keeps private, team emails within the team, and company secrets contained in email remain confidential. Google has none of these capabilities.
Managing Rights with Microsoft Exchange
Information Rights Management requires certain on-premises investments. It is not for everyone. Larger organizations often take the time to implement and benefit from IRM. Should this interest you, customers can establish IRM settings for Office 2010 and Outlook 2010 using Group Policy, while SharePoint customers have the choice of managing security via a LiveID or through a Rights Management Server.

Comments
Anonymous
January 01, 2003
@Ian Ray: Microsoft Active Directory Federation Services now supports RSA SecurID token authentication, (two factor authentication), to secure not only Office 365 applications, but also Microsoft Exchange, and the Azure cloud. (http://bit.ly/uQDbaq).Anonymous
January 01, 2003
@Matt: Thank you for your idea.Anonymous
January 01, 2003
@Ian Ray, Yes, the MSN support team resolved an IRM issue in its trial of a free, consumer, Hotmail IRM service occurring two years ago. Of course, business customers had no impact. By design, the free email service that Microsoft offers consumers and the email services that Microsoft provides to businesses are completely separate. Thank you for citing options for business customers in securing their documents. That is good to know. More details about IRM for Office 2010 are here. (http://bit.ly/kwH4DQ) @Gary Ross: IRM requires some on-premise implementation, and the following white paper describes security for Office 365 customers. (http://bit.ly/l5hNQX). With hybrid deployment, customers can continue leverage this powerful capability.Anonymous
January 01, 2003
@Ian Ray: While we will certainly be updating this blog with cloud security topics, you might also browse the Office 365 technical blog which provides some good updates. (http://bit.ly/eLdkDk)Anonymous
January 01, 2003
@Ian Ray: While second factor authentication is not for everyone, organizations adopting it have a need for this level of user security and consider both human factors and costs in relation to benefit. I offer no guidance regarding sustainability of other, potential 2nd factor authentication methods to Office 365, as we look to partners and customers for feedback on these potential methods, based on their experience using them with the cloud service.Anonymous
January 01, 2003
@Ian Ray: Those wishing to implement RSA SecurID for two factor authentication might begin by reviewing this blog post. It describes using federated identities in Active Directory with Office 365. (http://bit.ly/xvW2eS). We look forward to hearing about customers’ and partners’ experience with other 2 factor methods in authenticating to Office 365!Anonymous
January 01, 2003
@Ian Ray: IRM requires some on-premise implementation, and the following white paper describes security for Office 365 customers.(http://bit.ly/l5hNQX).Anonymous
January 01, 2003
@Ian Ray: Microsoft knows that technical capability is one thing and recommending a sustainable solution is much different. That is an important and much greater commitment. As business partners and customers test, verify and gain experience with how other authentication technologies interoperate and work within organizations, Microsoft may begin to recommend both RSA SecurID and other 2 factor authentication technologies to Office 365 customers. Until that time may come, Microsoft recommends RSA SecurID for 2 factor authentication to Office 365.Anonymous
December 07, 2011
When is IRM coming to the cloud?Anonymous
December 08, 2011
Is this similar to Office 2003 IRM? That feature creates incompatibility issues, or at least it did the last time I saw a file where someone had actually used it. Google did add a "prevent download" feature in early November, FWIW.Anonymous
December 08, 2011
I should add that I've long been interested in this technology except for two issues:
- Fears that it would be just as incompatible as different DRM formats used on other media
- Issues with being locked out of data such as those in this post http://tinyurl.com/ch3eyej Standard encryption with keys passphrases seems to work adequately for confidential information and doesn't have the issue of doubt that in the future this information will become unavailable. ECM vendors have tried to sell there management lock-in features for years with very low uptake. If a truly compatible and future-proof solution was devised, I'm sure businesses would be quicker to other encryption methods.
Anonymous
December 08, 2011
Another piece of security software I have used in the past is called "outlookgnupg" plugin. github.com/.../wiki This worked fairly well for decryption of sensitive documents sent when I worked for the government. Are there plans to extend the API of Office 365 to support such things? I have also used "cr-gpg" for Chrome (which I have had some issues installing on certain configurations due to its alpha status). Perhaps such a browser extension could be developed for encryption/decryption that would work with Office 365 as well. Just throwing this stuff out there. I haven't seen much Microsoft/Oracle/Adobe IRM integration actually in use, but have seen pgp-type encryption in use on sensitive document transmission many times.Anonymous
December 08, 2011
@Tony Tai Thank you for the link. From reading that blog, it appears S/MIME is not working in Office 365 without OWA. This would break any rights management, yes? I hope that has been/will be fixed.Anonymous
December 14, 2011
really? when do you want to compare this to google applications and not google docs?Anonymous
December 15, 2011
On the security issue in general, I would like to see an Office 365 option for "two-factor authentication". Enterprise still employs the obsolete 90 day password reset. This compiles with security audits of various standards devised decades ago, but does not secure information in a practical way. That is, a user could have a complex password written on a sticky note every 90 days or have "letmein11" as their password combined with text message codes... The latter seems to be more difficult to break from a practical perspecive. Really, it doesn't matter how strict sharing is set up if the account shared to is vulnerable. Office 365 programmers could solve this by borrowing a practical concept.Anonymous
December 27, 2011
@Tony Tai It would be nice if Active Directory allowed a user to use a set of hard tokens to turn off the existing authentication in the event that the SecurID keychain unit or phone is lost/stolen. I don't really understand the need for a proprietary solution as the only two-factor authentication offered. Seems expensive and cumbersome for a technology that has famously been compromised.Anonymous
January 05, 2012
@Tony Tai Are you stating that SaaS SMS or App-based two-factor authentication is not as "sustainable" a technology as SecurID keys? SecurID costs at minimum $25,000 for the central hardware and employees regularly lose the $60 keys. SecurID was compromised once, what assurance is there that this won't happen again. "Sustainable" does not seem like an appropriate label... "legacy" would fit better.Anonymous
January 09, 2012
@Tony Tai Well, I hope customers push for easier to deploy methods than SecurID.Anonymous
March 03, 2012
The comment has been removedAnonymous
July 29, 2015
http://www.gamesyoum7.com/game/347/%D9%84%D8%B9%D8%A8%D8%A9_%D8%A7%D9%84%D8%A8%D9%8A%D8%A7%D9%86%D9%88.html
http://www.gamesyoum7.com/game/343/%D9%84%D8%B9%D8%A8%D8%A9_%D8%A7%D9%84%D9%81%D8%B1%D8%A7%D8%AE.html
http://www.gamesyoum7.com/game/359/%D8%A7%D9%84%D8%B9%D8%A7%D8%A8_%D8%AA%D9%84%D8%A8%D9%8A%D8%B3_%D8%A8%D9%86%D8%A7%D8%AA.html
http://www.gamesyoum7.com/game/520/%D9%84%D8%B9%D8%A8%D8%A9_%D9%85%D8%A7%D8%B1%D9%8A%D9%88.html
http://www.gamesyoum7.com/game/184/%D8%A7%D9%84%D8%B9%D8%A7%D8%A8_%D8%B2%D9%88%D9%85%D8%A7.html
http://www.gamesyoum7.com/game/21/%D9%84%D8%B9%D8%A8%D8%A9_%D8%A8%D9%86_%D8%AA%D9%86_%D9%88%D9%82%D8%AA%D8%A7%D9%84_%D8%A7%D9%84%D9%81%D8%B6%D8%A7%D8%A6%D9%8A%D9%8A%D9%86.html
http://www.gamesyoum7.com/game/52/%D9%84%D8%B9%D8%A8%D8%A9_%D8%A7%D9%84%D9%85%D8%B5%D8%A7%D8%B1%D8%B9%D8%A9_%D8%A7%D9%84%D8%AD%D8%B1%D8%A9.html
http://www.gamesyoum7.com/game/521/%D9%84%D8%B9%D8%A8%D8%A9_%D9%85%D9%82%D9%8A%D8%A7%D8%B3_%D8%A7%D9%84%D8%AD%D8%A8.html
http://www.gamesyoum7.com/game/348/%D9%84%D8%B9%D8%A8%D8%A9_%D8%A7%D9%84%D9%82%D8%B7%D8%A9.html
http://www.gamesyoum7.com/game/375/%D9%84%D8%B9%D8%A8%D8%A9_%D8%AC%D8%A7%D8%AA%D8%A7.html
http://www.gamesyoum7.com/game/87/%D9%84%D8%B9%D8%A8%D8%A9_%D8%A7%D9%84%D9%85%D8%B2%D8%B1%D8%B9%D8%A9_%D8%A7%D9%84%D8%B3%D8%B9%D9%8A%D8%AF%D8%A9.html
http://www.gamesyoum7.com/game/73/%D9%84%D8%B9%D8%A8%D8%A9_%D8%B1%D8%A7%D9%84%D9%8A_%D8%A7%D9%84%D8%B3%D9%8A%D8%A7%D8%B1%D8%A7%D8%AA.html
http://www.gamesyoum7.com/game/509/%D9%84%D8%B9%D8%A8%D8%A9_%D9%83%D8%A7%D9%86%D8%AF%D9%8A_%D9%83%D8%B1%D8%A7%D8%B4.html
http://www.gamesyoum7.com/game/355/%D9%84%D8%B9%D8%A8%D8%A9_%D8%A8%D8%A7%D8%B1%D8%A8%D9%8A.html
http://www.gamesyoum7.com/game/434/%D9%84%D8%B9%D8%A8%D8%A9_%D8%B3%D8%A8%D9%88%D9%86%D8%AC_%D8%A8%D9%88%D8%A8.html
http://www.gamesyoum7.com/game/3/%D9%84%D8%B9%D8%A8%D8%A9_%D8%AA%D9%88%D9%85_%D9%88%D8%AC%D9%8A%D8%B1%D9%8A.html
http://www.gamesyoum7.com/game/488/%D9%84%D8%B9%D8%A8%D8%A9_%D9%81%D9%8A%D9%81%D8%A7.html
http://www.gamesyoum7.com/game/446/%D9%84%D8%B9%D8%A8%D8%A9_%D8%B5%D8%A8_%D9%88%D8%A7%D9%8A_%D9%88%D8%A7%D9%84%D8%B0%D9%87%D8%A8.html
http://www.gamesyoum7.com/game/34/%D9%84%D8%B9%D8%A8%D8%A9_%D8%AD%D8%B1%D8%A8_%D8%A7%D9%84%D9%81%D8%B6%D8%A7%D8%A1.html
http://www.gamesyoum7.com/game/430/%D9%84%D8%B9%D8%A8%D8%A9_%D8%B3%D8%A8%D8%A7%D9%82_%D8%A7%D9%84%D8%B3%D9%8A%D8%A7%D8%B1%D8%A7%D8%AA.html
http://www.gamesyoum7.com/game/132/%D8%A7%D9%84%D8%B9%D8%A7%D8%A8_%D8%AA%D9%84%D8%A8%D9%8A%D8%B3_%D8%AC%D8%AF%D9%8A%D8%AF%D8%A9.html
http://www.gamesyoum7.com/game/126/%D8%A7%D9%84%D8%B9%D8%A7%D8%A8_%D8%A8%D9%86%D8%A7%D8%AA_%D8%AC%D8%AF%D9%8A%D8%AF%D8%A9.html
http://www.gamesyoum7.com/game/230/%D8%A7%D9%84%D8%B9%D8%A7%D8%A8_%D8%B7%D8%A8%D8%AE_%D8%AC%D8%AF%D9%8A%D8%AF%D8%A9.html
http://www.gamesyoum7.com/game/127/%D8%A7%D9%84%D8%B9%D8%A7%D8%A8_%D8%A8%D9%86_%D8%AA%D9%86_%D8%A7%D9%84%D8%AC%D8%AF%D9%8A%D8%AF%D8%A9.html
http://www.gamesyoum7.com/game/259/%D8%A7%D9%84%D8%B9%D8%A7%D8%A8_%D9%81%D9%84%D8%A7%D8%B4_%D8%AC%D8%AF%D9%8A%D8%AF%D8%A9.htmlAnonymous
September 28, 2015
http://www.ojekgratis.com
http://www.ojekgratis.com
http://www.ojekgratis.com
http://www.ubergratis.com/
http://www.uber.com/invite/ubergratis.com
http://a-ndroid.com/
http://a-ndroid.com/category/flashing/samsung
http://a-ndroid.com/category/flashing/tool
http://bonekateddy.com/?page_id=16
http://bonekateddy.com/cara-order/
http://bonekateddy.com/testimoni/
http://bonekateddy.com/about/
http://www.goseopro.net/2015/03/jasa-backlink-murah-berkualitas.html
http://hargaminyakbulus.com/
http://hargaminyakbulus.com/cara-pakai-minyak-bulus/
http://hargaminyakbulus.com/cara-menghilangkan-jerawat-paling-mujarab-ampuh-dan-efektif
http://hargaminyakbulus.com/cara-menghilangkan-jerawat-paling-mujarab-ampuh-dan-efektifAnonymous
September 28, 2015
http://satriyoku.blogspot.com/2015/06/cara-membuat-id-bbm-di-hp-dan-komputer.html
http://satriyoku.blogspot.com/2015/01/cara-cek-pejwan-atau-page-one.html
http://satriyoku.blogspot.com/2015/04/jasa-backlink-manual-murah-amatiran-2015.html
http://satriyoku.blogspot.com/p/tentang-admin.html
http://www.okecapsa.com/
http://www.okecapsa.com/category/capsa-online/
http://www.okecapsa.com/category/capsa-susun/
http://www.okecapsa.com/category/dominoqq/
http://jualmodulbimbel.com/
http://jualmodulbimbel.com/produk
http://jualmodulbimbel.com/contact
http://jualmodulbimbel.com/cara-pemesanan
http://www.dhanyfirma.my.id/search/label/Action
http://www.dhanyfirma.my.id/search/label/Adventure
http://www.dhanyfirma.my.id/search/label/Arcade
http://www.dhanyfirma.my.id/search/label/CasinoAnonymous
October 01, 2015
Interior jakarta on http://maxinteriorjakarta.blogspot.comAnonymous
October 01, 2015
Situs buka jasa dan promosi jasa on http://www.bukajasa.comAnonymous
October 05, 2015
http://www.ojekgratis.com
http://www.ojekgratis.com
http://www.ojekgratis.com
http://www.ubergratis.com/
http://www.uber.com/invite/ubergratis.com
http://a-ndroid.com/
http://a-ndroid.com/category/flashing/samsung
http://a-ndroid.com/category/flashing/tool
http://bonekateddy.com/?page_id=16
http://bonekateddy.com/cara-order/
http://bonekateddy.com/testimoni/
http://bonekateddy.com/about/
http://www.goseopro.net/2015/03/jasa-backlink-murah-berkualitas.html
http://hargaminyakbulus.com/
http://hargaminyakbulus.com/cara-pakai-minyak-bulus/
http://hargaminyakbulus.com/cara-menghilangkan-jerawat-paling-mujarab-ampuh-dan-efektifAnonymous
October 05, 2015
http://satriyoku.blogspot.com/2015/10/cara-keluar-atau-mengeluarkan-akun-bbm.html
http://satriyoku.blogspot.com/2015/01/cara-cek-pejwan-atau-page-one.html
http://satriyoku.blogspot.com/2015/04/jasa-backlink-manual-murah-amatiran-2015.html
http://caraterbaru.web.id
http://www.caraterbaru.web.id/2015/09/cara-terbaru-membuat-widget-fanspage.html
http://www.caraterbaru.web.id/2015/09/mekanisme-terbaru-pengangkatan-guru.html
http://jualmodulbimbel.com/
http://jualmodulbimbel.com/produk
http://jualmodulbimbel.com/contact
http://jualmodulbimbel.com/cara-pemesanan
http://www.dewicapsa.com/search/label/Agen%20Poker%20Online
http://www.dewicapsa.com/search/label/Poker%20Android
http://www.dewicapsa.com/search/label/Capsa%20Susun
http://www.dewicapsa.com/search/label/Capsa%20Online
http://property-sunter.com/category/apartemen/
http://property-sunter.com/jual-beli-sewa-gudang-di-sunter/
http://property-sunter.com/jual-beli-sewa-ruko-di-sunter/
http://property-sunter.com/jual-beli-sewa-rumah-di-sunter/Anonymous
November 18, 2015
Jadwal bola hari ini on http://www.hantubola.com
Prediksi bola malam ini on http://wwwhantubola.com
Prediksi bola akurat on http://wwwhantubola.comAnonymous
November 18, 2015
uber gratis on http://www.ubergratis.com
uber coupon code on http://www.ubergratis.com
www.uber.com/invite/ubergratis.comAnonymous
November 20, 2015
cara menghilangkan bekas jerawat on http://hargaminyakbulus.com/cara-menghilangkan-bekas-jerawat-cepat-dan-mudah/
cara menghilangkan jerawat on http://hargaminyakbulus.com/cara-menghilangkan-jerawat-paling-mujarab-ampuh-dan-efektif/
Pengobatan Herbal Rematik Sendi on http://rematiksendi.wordpress.com/
Obat Herbal Pengapuran Tulang on http://rematiksendi.wordpress.com/
obat herbal asam urat manjur on http://rematiksendi.wordpress.com/
obat kista ovarium on http://obatkistaovarium.wordpress.com
obat kista ovarium herbal on http://obatkistaovarium.wordpress.com
pengobatan kista ovarium selain operasi on http://obatkistaovarium.wordpress.com
obat herbal on http://www.pustakaherbal.com
crystal x on http://www.pustakaherbal.com/2015/09/natural-crystal-x.html
obat herbal asam urat on http://www.pustakaherbal.com/2015/10/penyakit-asam-urat-penyebab-gejala-dan-cara-mengatasi.htmlAnonymous
November 20, 2015
capsa susun @ http://www.dewicapsa.com/search/label/Agen%20Poker%20Online
http://www.dewicapsa.com/search/label/Poker%20Android
http://www.dewicapsa.com/search/label/Capsa%20Susun
http://www.dewicapsa.com/search/label/Capsa%20Online
Jadwal Bola hari ini @ http://www.hantubola.com
Prediksi Bola malam ini http://www.hantubola.com
Prediksi bola akurat @ http://www.hantubola.comAnonymous
November 20, 2015
jasa interior jakarta @ http://www.maxinteriorjakarta.com/
http://www.maxinteriorjakarta.com/2015/10/jasa-desain-interior-kantor-modern.html
jasa interior kantor jakarta @ http://www.maxinteriorjakarta.com/2015/09/interiorjakarta.html
http://www.maxinteriorjakarta.com/2015/10/jasa-desain-interior-kamar-anak.html
http://www.maxinteriorjakarta.com/2015/10/jasa-desain-interior-kantor-jakarta.html
Dompet kulit pari on http://www.jabruzz-fashion.com
Harga Dompet kulit pari on http://www.jabruzz-fashion.com/2015/10/katalog-dompet-kulit-pari-asli-pria-wanita-murah.html
dompet pria kulit pari on http://www.jabruzz-fashion.com/2015/11/dompet-pria-kulit-pari-original-branded-hitam-oval.html
kotak jam tangan on http://www.jogjahandycraft.com
tempat perhiasan on http://www.jogjahandycraft.com
souvenir perusahaan on http://www.jogjahandycraft.comAnonymous
November 20, 2015
ojek gratis @ http://www.ojekgratis.com
grab bike on http://www.ojekgratis.com
Go jek bndung on http://www.ojekgratis.com
uber gratis @ http://www.ubergratis.com/
uber coupon code on http://www.ubergratis.com/
http://www.uber.com/invite/ubergratis.com
sprei katun jepang on http://www.paramacollection.id
grosir sprei katun jepang on http://www.paramacollection.id/
sprei katun jepang terbaru on http://www.paramacollection.id
jasa poles marmer on http://poleslantai.com/poles-marmer/
jasa poles marmer on http://www.poleslantai.com/
agen taruhan bola @ http://www.maubet4u.com
agen taruhan bola sbobet @ http://www.maubet4u.com,
agen taruhan bola online sbobet @ http://www.maubet4u.comAnonymous
November 20, 2015
jasa backlink berkualitas @ http://www.goseopro.net/2015/03/jasa-backlink-murah-berkualitas.html
http://www.goseopro.net/2015/10/alat-ukur-standar-backlink.html
http://www.goseopro.net/2015/10/bukti-klien-jasa-backlink-kami.html
http://www.goseopro.net/2015/11/beberapa-teknik-backlink-ampuh-dan.html
blog manfaat bersama @ http://manfaatbersama.blogspot.com
http://manfaatbersama.blogspot.com/2015/10/cara-mengatasi-windows-help-and-support.html
http://manfaatbersama.blogspot.com/2015/03/cara-menembus-situs-yang-di-blok.html
cara screenshot semua handphone android on http://satriyoku.blogspot.com/2015/11/cara-screenshot-handphone-android.html
cara cek page one @http://satriyoku.blogspot.com/2015/01/cara-cek-pejwan-atau-page-one.html
jasa backlink manual on http://satriyoku.blogspot.com/2015/04/jasa-backlink-manual-murah-amatiran-2015.htmlAnonymous
November 20, 2015
ojek gratis @ http://www.ojekgratis.com
grab bike on http://www.ojekgratis.com
Go jek bndung on http://www.ojekgratis.com
uber gratis @ http://www.ubergratis.com/
uber coupon code on http://www.ubergratis.com/
http://www.uber.com/invite/ubergratis.com
sprei katun jepang on http://www.paramacollection.id
grosir sprei katun jepang on http://www.paramacollection.id/
sprei katun jepang terbaru on http://www.paramacollection.id
jasa poles marmer on http://poleslantai.com/poles-marmer/
jasa poles marmer on http://www.poleslantai.com/
agen taruhan bola @ http://www.maubet4u.com
agen taruhan bola sbobet @ http://www.maubet4u.com,
agen taruhan bola online sbobet @ http://www.maubet4u.comAnonymous
November 20, 2015
capsa susun @ http://www.dewicapsa.com/search/label/Agen%20Poker%20Online
http://www.dewicapsa.com/search/label/Poker%20Android
http://www.dewicapsa.com/search/label/Capsa%20Susun
http://www.dewicapsa.com/search/label/Capsa%20Online
Jadwal Bola hari ini @ http://www.hantubola.com
Prediksi Bola malam ini http://www.hantubola.com
Prediksi bola akurat @ http://www.hantubola.comAnonymous
November 20, 2015
cara menghilangkan bekas jerawat on http://hargaminyakbulus.com/cara-menghilangkan-bekas-jerawat-cepat-dan-mudah/
cara menghilangkan jerawat on http://hargaminyakbulus.com/cara-menghilangkan-jerawat-paling-mujarab-ampuh-dan-efektif/
Pengobatan Herbal Rematik Sendi on http://rematiksendi.wordpress.com/
Obat Herbal Pengapuran Tulang on http://rematiksendi.wordpress.com/
obat herbal asam urat manjur on http://rematiksendi.wordpress.com/
obat kista ovarium on http://obatkistaovarium.wordpress.com
obat kista ovarium herbal on http://obatkistaovarium.wordpress.com
pengobatan kista ovarium selain operasi on http://obatkistaovarium.wordpress.com
obat herbal on http://www.pustakaherbal.com
crystal x on http://www.pustakaherbal.com/2015/09/natural-crystal-x.html
obat herbal asam urat on http://www.pustakaherbal.com/2015/10/penyakit-asam-urat-penyebab-gejala-dan-cara-mengatasi.htmlAnonymous
November 28, 2015
http://3rbsoft.com/Anonymous
December 01, 2015
http://msry.org/funny-pictures.htmlAnonymous
December 01, 2015
http://msry.org/%D8%B5%D9%88%D8%B1-%D8%AD%D8%B2%D9%86.htmlAnonymous
December 03, 2015
http://msry.org/feedAnonymous
December 15, 2015
dompet wanita kulit pari on http://paridjogja.com/category/dompet-wanita
dompet wanita kulit ikan pari on http://paridjogja.com/category/dompet-wanita/dompet-wanita-lipat-dua
dompet wanita kulit pari murah on http://paridjogja.com/category/dompet-wanita/dompet-wanita-lipat-tiga
dompet wanita kulit ikan pari murah on http://paridjogja.com/blog/dompet-kulit-pari-dompet-pria-dompet-wanita-tas-gantungan-kunci-kulit-pari
dompet wanita kulit pari termurah on http://paridjogja.com/blog/caridompetwanitakulitparimurah
dompet wanita kulit ikan pari termurah on http://paridjogja.com/dompet-universal/dompet-universal-kulit-pari-duri-merah-maroon.html
grosir dompet wanita kulit pari on http://paridjogja.com/dompet-wanita/dompet-wanita-jual-dompet-pari-murah-berkualitas.html
grosir dompet wanita kulit ikan pari on http://paridjogja.com/reseller/grosir-dompet-wanita/grosir-dompet-wanita-kulit-ikan-pari.htmlAnonymous
December 28, 2015
pari djogja on http://paridjogja.com/tentang-kami
pari djogja on http://paridjogja.com/katalog
pari djogja on http://paridjogja.com/category/dompet-pria
pari djogja on http://paridjogja.com/tag/dompet-pari-murah
pari djogja on http://paridjogja.com/tag/grosir-dompet-pari
pari djogja on http://paridjogja.com/cara-belanja
pari djogja on http://paridjogja.com/category/gelang
pari djogja on http://paridjogja.com/category/reseller/grosir-dompet-wanita
pari djogja on http://paridjogja.com/category/paridjogja
pari djogja on http://paridjogja.com/tag/paridjogjaAnonymous
January 09, 2016
Paket tour wisata on http://www.tiketpesawat24jam.com
Paket tour wisata murah on http://www.tiketpesawat24jam.com
Paket tour wisata hemat on http://www.tiketpesawat24jam.comAnonymous
January 09, 2016
Perontok bulu permanent on http://www.toko-kesehatan-kecantikan.com
Obat perontok bulu on http://www.toko-kesehatan-kecantikan.com
yofume perontok bulu on http://www.toko-kesehatan-kecantikan.com/kosmetik/perontok-bulu.htmlAnonymous
January 09, 2016
Jual materai 6000 on http://www.grosirmaterai6000.com/
Grosir materai 6000 on http://www.grosirmaterai6000.com/2015/12/jual-materai-6000-terbaru-2015.html
Foto materai 6000 on http://www.grosirmaterai6000.com/p/gallery-produk-materai-6000-baru-2015.html
Cara pemesanan materai 6000 on http://www.grosirmaterai6000.com/p/blog-page.htmlAnonymous
January 09, 2016
Togel online on http://www.sindobet.com
Taruhan bola online on http://www.sindobet.com
Prediksi bola hari ini on http://www.sindobet.comAnonymous
January 09, 2016
Jasa backlink dan seo on http://www.goseopro.net/
Alat ukur standart backlink goseopro.net http://www.goseopro.net/2015/10/alat-ukur-standar- backlink.html
Jasa backlink murah berkualitas http://www.goseopro.net/2015/03/jasa-backlink-murah-berkualitas.htmlAnonymous
January 21, 2016
pari djogja on http://paridjogja.com/tentang-kami
pari djogja on http://paridjogja.com/katalog
pari djogja on http://paridjogja.com/category/dompet-pria
pari djogja on http://paridjogja.com/tag/dompet-pari-murah
pari djogja on http://paridjogja.com/tag/grosir-dompet-pari
pari djogja on http://paridjogja.com/cara-belanja
pari djogja on http://paridjogja.com/category/gelang
pari djogja on http://paridjogja.com/category/reseller/grosir-dompet-wanita
pari djogja on http://paridjogja.com/category/paridjogja
pari djogja on http://paridjogja.com/tag/paridjogjaAnonymous
March 30, 2016
fantastic post, very informative. I wonder why the other specialists of this sector do not notice this. You must continue your writing. I am confident, you’ve a great readers’ base already!
http://www.encendiabiochar.com/Anonymous
April 15, 2016
Hokiqq @ http://hokiqq.us
Dominoqq @ http://hokiqq.us
Bandarq @ http://hokiqq.usAnonymous
April 15, 2016
Cara flashing android @ http://indoflasher.net
Tutorial flashing android @ http://indoflasher.net
Tempat download stockrom dan firmware indonesia @ http://indoflasher.netAnonymous
April 15, 2016
Jasa seo murah bergaransi @ http://www.goseopro.net
jasa seo murah @ http://www.goseopro.net/p/goseopro-layanan-jasa-seo-murah.html
jasa backlink berkualitas @ http://www.goseopro.net/2015/03/jasa-backlink-murah-berkualitas.html