Troubleshooting FIM CM: Certificate Request Error: Denied by Policy Module
ISSUE
FIM CM certificate requests fail. The error returned in the CM request page is "denied by Policy Module."
TROUBLESHOOTING
Application and FIM Certificate Manager event logs
Log Name: Application
Source: Microsoft-Windows-CertificationAuthority
Date: 5/30/2013 12:17:36 PM
Event ID: 53
Task Category: None
Level: Warning
Keywords: Classic
User: SYSTEM
Computer: CA.contoso.com
Description:
Active Directory Certificate Services denied request xxxx because An unknown error occurred while processing the certificate. 0x80090327 (-2146893017). The request was for CN=CA.contoso.com. Additional information: Denied by Policy Module
Log Name: FIM Certificate Management
Source: FIM CM CA Modules
Date: 5/30/2013 12:17:36 PM
Event ID: 0
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: CA.contoso.com
Description:
"2013-05-30 12:17:36.56 -05" "Microsoft.Clm.PolicyModule.Policy" "Microsoft.Clm.Shared.CertificateServer.EnrollmentAttributes LoadEnrollmentAttributesData(System.String)" "" "NT AUTHORITY\SYSTEM" 0x00001C84 0x00000004
1) Exception Information
*********************************************
Exception Type: System.ApplicationException
Message: Unable to verify certificate validity.
Data: System.Collections.ListDictionaryInternal
TargetSite: Void VerifySigningCertificateValidity(System.Security.Cryptography.X509Certificates.X509Certificate)
HelpLink: NULL
Source: Microsoft.Clm.PolicyModule
StackTrace Information
*********************************************
at Microsoft.Clm.PolicyModule.Policy.VerifySigningCertificateValidity(X509Certificate cert)
at Microsoft.Clm.PolicyModule.Policy.LoadEnrollmentAttributesData(String xml)
2) Exception Information
*********************************************
Exception Type: System.Security.Cryptography.CryptographicException
Message: None of the signers of the cryptographic message or certificate trust list is trusted.
Data: System.Collections.ListDictionaryInternal
TargetSite: Void VerifySigningCertificateValidity(System.Security.Cryptography.X509Certificates.X509Certificate)
HelpLink: NULL
Source: Microsoft.Clm.PolicyModule
StackTrace Information
*********************************************
at Microsoft.Clm.PolicyModule.Policy.VerifySigningCertificateValidity(X509Certificate cert)
Enabling FIM CM logging (clm.txt) finds the following.
Request certificate from CA for certificate template: FIMCMCheckout. Status: -2146877420. Disposition: Denied. Disposition Message: Denied by Policy Module. Error Message: The request was denied by a certificate manager or CA administrator. 0x80094014 (-2146877420)
FURTHER TROUBLESHOOTING
Based on the exception details in the CM module event CAPI2 event logging was enabled on the CA. Reproducing the issue logged several CAPI2 events. The most notable example is below.
Log Name: Microsoft-Windows-CAPI2/Operational
Source: Microsoft-Windows-CAPI2
Date: 5/30/2013 1:19:25 PM
Event ID: 42
Task Category: Reject Revocation Information
Level: Error
Keywords: Revocation,Path Validation
User: SYSTEM
Computer: CA.contoso.com
Description:
For more details for this event, please refer to the "Details" section
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-CAPI2" Guid="{5bbca4a8-b209-48dc-a8c7-b23d3e5216fb}" />
<EventID>42</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>42</Task>
<Opcode>0</Opcode>
<Keywords>0x4000000000000005</Keywords>
<TimeCreated SystemTime="2013-05-30T18:19:25.984466500Z" />
<EventRecordID>17757</EventRecordID>
<Correlation />
<Execution ProcessID="8428" ThreadID="7344" />
<Channel>Microsoft-Windows-CAPI2/Operational</Channel>
<Computer>CA.contoso.com</Computer>
<Security UserID="S-1-5-18" />
</System>
<UserData>
<CertRejectedRevocationInfo>
<SubjectCertificate fileRef="85E6EA9235EC50D0AA98D8EEF86B91020DA7AC60.cer" subjectName="SVC_FIMCM_Agent" />
<IssuerCertificate fileRef="BA02C4B3EE999E878E5145883733A4CF069D28DE.cer" subjectName="CA" />
<CertificateRevocationList location="Store" fileRef="322DD0D0B6CEF55C8D276661F10A7ECEADEB6F0E.crl" issuerName="CA" />
<Action name="CheckTimeValidity" />
<EventAuxInfo ProcessName="certsrv.exe" />
<CorrelationAuxInfo TaskId="{6356E380-076B-4286-8E3A-C37766BBE58A}" SeqNumber="3" />
</CertRejectedRevocationInfo>
</UserData>
</Event>
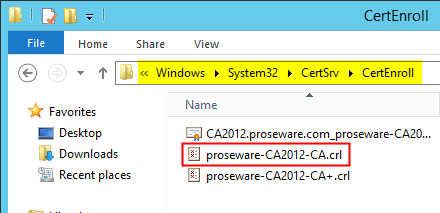
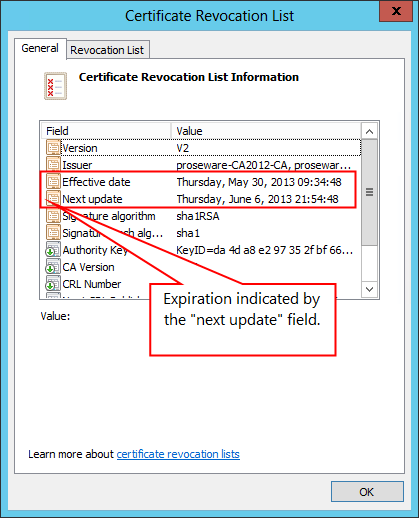
The event indicated something may be amiss with a CRL on the CA. Checking the CRL file on the CA itself (%systemroot%\System32\CertSrv\CertEnroll) found an expired CRL. However the externally published CRL (AD, http site, etc.) was current.
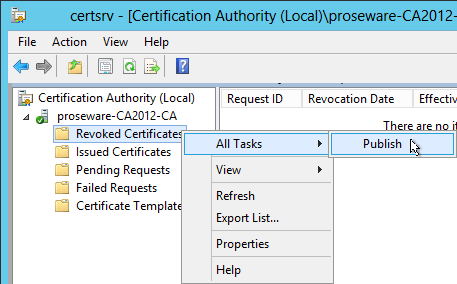
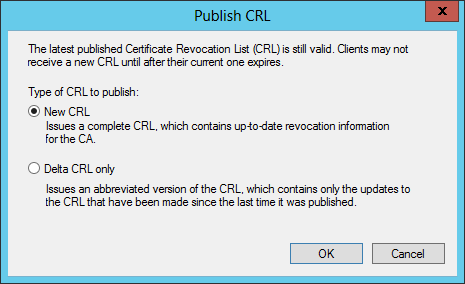
RESOLUTION
Published a new CRL in the Certification Authority snap-in and the local file (and others) updated as expected.