BizTalk Server: Importing Certificates
Introduction
BizTalk Server depends mainly on the security provided by certificates and uses them for encryption, decryption, signing and verifying digital signatures. By making use of the certificates BizTalk Server can:
- Send and receive data that can be trusted
- Make sure that the data it processes is secure
- Make sure that authorized parties receive its messages
- Make sure that it receives messages from authorized parties
The underlying methodology of digital certificates is called Public Key Infrastructure (PKI). Here a user has a key pair consisting of a public and a private key. Any encryption performed with a private key can be decrypted with the corresponding public key, and vice versa. As the terms imply the private key remains under the sole control of the user and the public key is made publicly available. For the public to know who is the owner of a certain public key, the data that identifies the owner is added to that key. The combination of that data and the public key is referred to as a digital certificate.
Digital certificates are stored in certificate stores. A certificate store often has numerous certificates, possibly issued by a number of different certification authorities.
There are two locations (stores) that BizTalk uses:
Other People Store
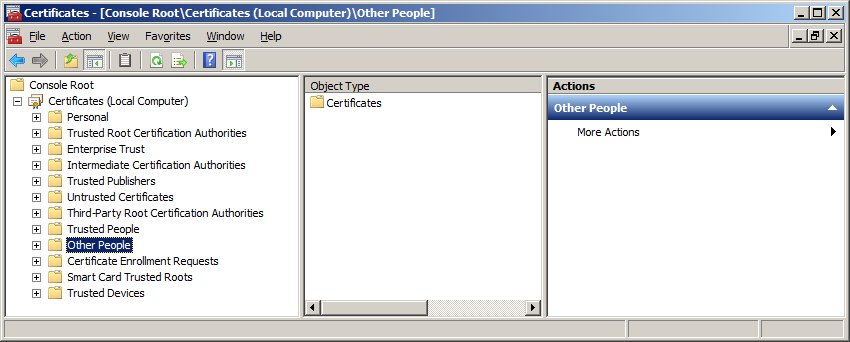
Through the Other People store BizTalk retrieves the public key certificates needed to encrypt outgoing messages and to verify the digital signatures on incoming messages. All users can read and use the certificates in this store. The following figure shows the Other People certificate store that BizTalk Server uses for public key certificates.
Figure 1. Certificate store local computer (click picture to enlarge).
Personal certificate store
BizTalk uses the Personal certificate store to create an association to a private key needed to decrypt incoming messages and sign outbound messages. The personal certificate store of the host instance is used to access the private key associated with that service account. Every Windows account enabled to log on interactively on a computer has a personal certificate store that only that account can access.
When a running host instance needs to decrypt incoming or sign outbound messages it requires a private key. The certificate that corresponds to that private key must be stored in the Personal certificate store for the service account that runs that host instance. The following figure shows the Personal certificate store that BizTalk Server uses for certificates that have an associated private key.
Figure 2. Personal Certificate store (click picture to enlarge).
Importing certificates
To import certificates you can use the Microsoft Management Console (MMC), or command line tool CertWizard.
Microsoft Management Console
Through mmc you have to perform the following steps:
a) Type mmc at command line.
b) Console will appear and you can select File.
c) Navigate to Add/Remove Snap-in….
d) In Add- or Remove Snap-ins select Certificates and click Add.
Figure 3. Add or Remove Snap-ins dialog enabling you to add a snap-in.
e) A Certificates Snap-in dialog screen will appear with three options how snap-in should manage the certificates:
- My user account
- Service account
- Computer account
f) Select one of the options and click Finish. (Note: I normally choose “Computer account”)
g) You can repeat steps e to f if you need to manage more than one certificate store. In “Select computer” window, select the option “Local computer: (the computer this console is running on)” and click Finish.
h) Once you have the desired Snap-ins click Ok.
i) You are now able to import certificates in key store you require by right clicking a store and select All Tasks --> Import…
You will be guided by Certificate Import Wizard.
j) When the Wizard fires up you see the welcome screen indicating you can copy a certificate or the revocation list to a certificate store. Click Next.
k) Specify the file to import using browse button and navigate to the location of the file. Click Next.
l) On certificate store screen you have to indicate where certificates need to be placed.
m) You can either let the Wizard automatically select the store based on the type of certificate or manually place it in a store. In that case the certificate store where you have started the Wizard is selected (i.e. Personal). You can use the Browse button to select another store. Click Next.
n) You will see a summary of where the certificate will be placed. Click Finish.
CertWizard
With the CertWizard command line utility you can import a certificate from a .pfx or .cer file into a private or public store for use with Microsoft BizTalk Server. A .pfx file contains both a private key and certificate while a .cer file only holds the certificate. This utility first has to build in Visual Studio before you can use it. The source code for CertWizard can be found in the C:\Program Files\Microsoft BizTalk Server <version>\SDK\Utilities\Certificate Wizard folder or BTARN SDK folder using the MS-DOS CD command, for example, type cd C:\Program Files\Microsoft BizTalk <version> Accelerator for RosettaNet\SDK. In a 64-bit version of the operating system and BizTalk Server 20xx, it will be in the C:\Program Files (x86)\Microsoft BizTalk Server <version>\SDK\Utilities\Certificate Wizard folder.
To use the CertWizard utility, open the solution in Visual Studio <version> and build it or st the command prompt, type CertWizard /?. Now perform following steps to import a certificate:
a) Open a command prompt and navigate to the folder where CertWizard resides (i.e. C:\Program Files\Microsoft BizTalk Server <version>\SDK\Utilities\Certificate Wizard\bin\Debug or C:\Program Files\Microsoft BizTalk <version> Accelerator for RosettaNet\SDK).
b) Syntax for importing a private key is as follows:
CertWizard /Privatekey <filename>.pfx [/Filepassword <filepassword>] [/Useridentity <useridentity>] [/Password <password>] [/Thumbprint <thumbprint>] [/Usage sign|decrypt|both|none] [/Exportable true|false]
**
Figure 4. Screenshot of CertWizard capabilities.
c) You can also use CertWizard to import a rootkey by using the following command:
CertWizard /Rootkey filename.cer
Note: A root key is either an unsigned public key certificate or a self-signed certificate that identifies the Root Certificate Authority (CA).
Importing certificates can be done through mmc snap-in or command line tool (CertWizard). Using mmc a user can easily manage certificates. Through the All Tasks menu item the user is able to import certificates with the guidance of a wizard, which guides him through several steps to ultimately have the certificate imported in the desired store. This can also be achieved using the CertWizard command line tool. With certificates in the appropriate stores BizTalk has capability to sign and encrypt messages to facilitate message level security.
See Also
In general you need a good understanding on how to manage digital certificates used with BizTalk Server. Installation of certificates is one thing, but you also need to know in which folder to install certificates.
For a checklist of steps to install the certificates see:
Beside the checklist you can review these resources on MSDN:
- Best Practices for Managing Certificates
- Known Issues with Certificates in BizTalk Server
- Installing and Configuring Digital Certificates
BizTalk Server uses two types of certificate stores; the Other People certificate store for public key certificates, and the Personal certificate store of each host instance service account for certificates with associated private keys:
See the following TechNet Wiki concerning usage of certificates for signing and encryption:
- BizTalk Server 2013: Sign and verifying a message* *
- BizTalk Server 2013: Encrypting and decrypting a message
Another important place to find an extensive amount of BizTalk related articles is the TechNet Wiki itself. The best entry point is BizTalk Server Resources on the TechNet Wiki.
Finally Powershell is a good tool to see where the certificates are installed, using MMC (Microsoft Management Console) you can see all the certificates installed in the machine, but we cannot search by thumbprint. See Sandro Pereira’s post: