Management of SIDs in Active Directory
SID (Security Identifier) is a unique identifier that Active Directory uses to identify objects as security principal. It is maintained in every Active Directory Domain and is never re-used.
How is an SID generated in Active Directory?
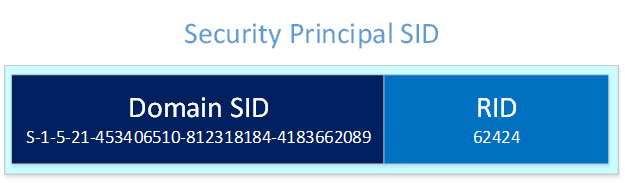
Each Active Directory domain has a unique identifier named Domain SID. This identifier is used to generate SIDs for security Principals within this domain. In fact, a security Principal SID in an Active Directory Domain is composed of the security principal domain SID as prefix and an RID (Relative Identifier) as a suffix:
To get your Domain SID, you can use the following Powershell command:
import-module activedirectory (Get-ADDomain).DomainSID.value |
Example of output: S-1-5-21-453406510-812318184-4183662089
To get an Active Directory security principal SID, you can run the following Powershell commands (You need to replace “Domain” with the NetBIOS name of your domain and “SecPrin_sAMAccountName” with the sAMAccountName of your security principal):
$Secprin = New-Object System.Security.Principal.NTAccount("Domain", "SecPrin_sAMAccountName") $strSID = $Secprin.Translate([System.Security.Principal.SecurityIdentifier]) $strSID.Value |
Example of output: S-1-5-21-453406510-812318184-4183662089-62424
How are RIDs managed in Active Directory?
RIDs are managed in each Active Directory Domain by the RID master FSMO holder. This is a Domain Controller that allocates a pool of RIDs to each of the Domain Controllers within its Active Directory domain. By default, an RID pool has 500 RIDs but this can be increased.
Each Domain Controller in an Active Directory domain uses its RID pool allocated by the RID master to create new security Principals. The RID master guarantees that every RID pool is unique and RIDs are never re-used. That is why a Security Identifier is always unique and never re-used.
The RID allocation of a Domain Controller can be checked by running the following command:
dcdiag.exe /test:ridmanager /v |
**How to protect your Active Directory from RID Pool Depletion: **http://social.technet.microsoft.com/wiki/contents/articles/21326.how-to-protect-your-active-directory-from-rid-pool-depletion.aspx
**
**
Why SIDs should not be re-used?
SIDs should not be re-used because they guarantee the uniqueness of a Security Principal within an Active Directory domain and re-using them will end up with security problems.
It is unsecure to re-use SIDs because this may grant unauthorized access to systems using SID-based ACLs.
Below is an example of how re-using an SID can be dangerous:
Let’s suppose that we have a Shared folder for Finance department within CONTOSO Company. An employee named John SMITH has full access to this Shared Folder which contains confidential data of the company.
John SMITH left the company and his AD account was removed. On the Shared Folder, John SMITH permission will not be automatically removed and the Shared folder will still report that John SMITH SID has full access to it.
If Active Directory was allowing the re-use of SIDs then a new security Principal can have John SMITH SID since it is available in Active Directory. If this was true then the new security Principal will automatically have Full access to Finance Shared Folder while it should not have.
That is why SIDs are never re-used in Active Directory.
How many SIDs can a security Principal have?
By default, a security Principal can have only one SID. In situations where a security Principal was migrated from a Domain to another, the security Principal can keep its old SIDs (SID History) to keep access to old resources during the transition. This is feasible by using tools like ADMT (Active Directory Migration Tool).
Where are SIDs stored in Active Directory?
In Active Directory, SIDs are stored in two attributes:
- objectSid: This is the security Principal SID that is generated during its creation
- sIDHistory: These are the SIDs that were kept from old domains (SID History)
Other Languages
This article is available in other languages.