How to Secure DNS Updates on Microsoft DNS Servers
Maintaining DNS records can be very challenging if it is done manually. That is why Microsoft DNS servers allow dynamic DNS updates but this needs to be enabled with caution as it needs to be done in a secure way. This Wiki article explains how DNS updates can be secured on Microsoft Windows DNS servers.
DNS records could be static or dynamic.
A static DNS record is a record that was created manually by a DNS administrator or a dynamic record that was converted by a DNS administrator to a static one. These records are maintained manually and should be administered only by trusted persons. Securing the updates of static DNS records requires limiting the persons having the rights to update them.
How to convert a dynamic resource record to a static one without re-creating it in DNS: http://social.technet.microsoft.com/wiki/contents/articles/21726.how-to-convert-a-dynamic-resource-record-to-a-static-one-without-re-creating-it-in-dns.aspx
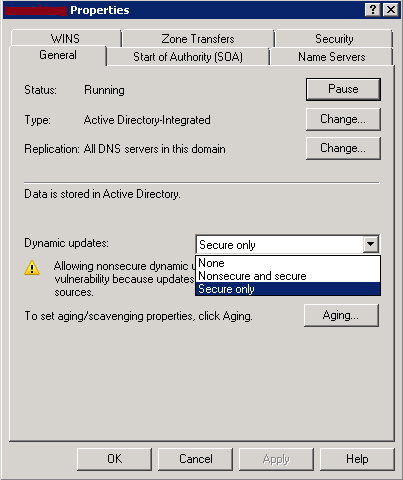
Dynamic DNS records are created by DNS clients or systems on behalf of DNS clients (Example: DHCP servers). Allowing Dynamic DNS updates minimizes the administrative effort to maintain DNS zones. On Microsoft DNS servers, there are three possible configurations for dynamic updates:
- None: No dynamic updates are allowed. The DNS zone records management need to be done manually.
- Nonesecure and secure: Dynamic updates are accepted without checking if the source of updates is trusted or not.
- Secure only: Dynamic updates are accepted only from trusted sources. This option is available only if your primary DNS zone is hosted on a Domain Controller and is an AD-integrated DNS zone.
If enabling Dynamic updates is required for a company, it is highly recommended to use Secure only dynamic updates option.
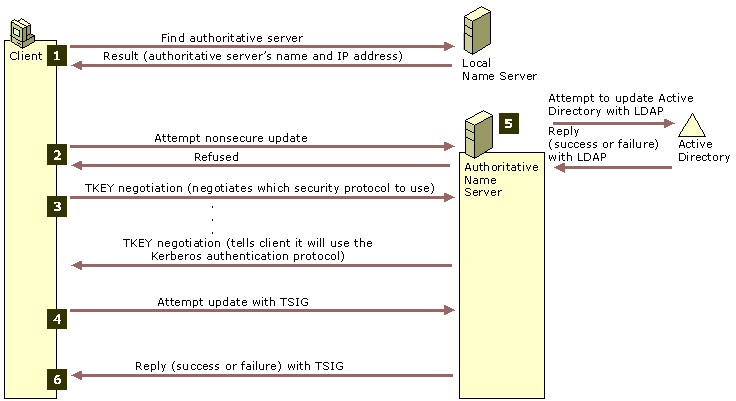
This is because a DNS update source is considered as trusted only if:
- The DNS update source was authenticated against Active Directory
- The DNS update source has the permission to update the DNS record (*)
(*) If the DNS record to update does not exist in your DNS zone then a new DNS record will be created and the DNS update source will be set as the owner and will be granted Full Control permission on the new DNS record.
The following figure shows the Secure Dynamic Update Process:
Secure Dynamic Update: http://technet.microsoft.com/en-us/library/cc961412.aspx
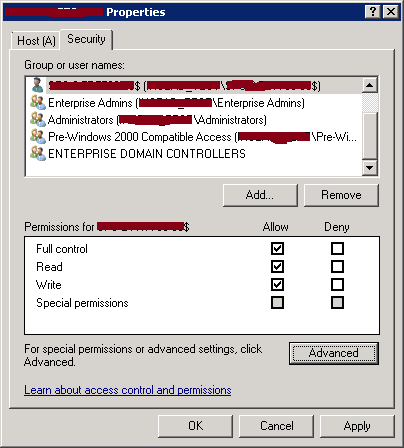
To identify who can make updates on an existing DNS record, you can examine the ACLs in the Security tab of its properties:
By clicking on Advanced and then going to Owner, you would be able to identify the owner of the DNS record (By using Secure only Dynamic updates, the DNS update source AD account will be set as the owner of the DNS record).
Combining an AD based authentication and an ACL authorization system offers a secure way of allowing DNS updates when DNS clients directly query your DNS servers to request updates.
By default having DNS records dynamically updated requires that DNS clients request it. If a company has DNS clients (Windows NT for example) that do not request DNS record updates to be registered in their DNS zones, then the company requires a system that will register the DNS records on behalf of the client: Microsoft proposes using Windows Server DHCP servers to achieve that.
A DHCP server could be configured to register DNS records on behalf of their clients and propose the following settings:
- Enable DNS dynamic updates according to the settings below: Enabling this check box will enable DNS dynamic updates to be done by a DHCP server on behalf of its clients. If Dynamically update DNS A and PTR records only if requested by the DHCP clients option is used then the DHCP server will update DNS A and PTR records for a DHCP client only if the client requested it. If Always dynamically update DNS A and PTR records option is enabled then the DHCP server will update the DHCP client DNS A and PTR records regardless of whether the client has requested to perform its own updates.
- Discard A and PTR records when lease is deleted: Enabling this check box will make the DHCP server delete the DNS A and PTR records for a client when its DHCP lease expires and is not renewed.
- Dynamically update DNS A and PTR records for DHCP clients that do not request updates (for example, clients running Windows NT 4.0): Enabling this check box will make the DHCP server do dynamic updates of DNS A and PTR records for DHCP clients that do not request updates.
You need to note here that the DHCP servers will not be able to identify if the DHCP client is trusted or not and will request the updates on behalf of its client. To avoid having a server / client name squatting by another server / client via DHCP dynamic updates for DNS, it is important to have Name Protection feature enabled on DHCP servers.
What Is Name Protection: http://blogs.technet.com/b/teamdhcp/archive/2009/01/29/what-is-name-protection.aspx
There are actually two ways to make a Windows Server DHCP server authorized to register A and PTR DNS records on behalf of its client:
- By adding the DHCP server as a member of DNSUpdateProxy AD group: Any authenticated user can take ownership of registered DNS records by the DHCP server as they have no security. This is a not recommended option.
- By adding the DHCP server as member of DNSUpdateProxy AD group and using DNS dynamic update credentials: By using an AD account as DNS dynamic update credentials, DNS records registered by the DHCP server will have this AD account as owner. This prevents having them updated by any authenticated user. This is the recommended option and is required to have secure dynamic updates working when your DHCP server is collocated on a domain controller.
DNS Record Ownership and the DnsUpdateProxy Group: http://technet.microsoft.com/en-us/library/dd334715(v=ws.10).aspx
Remark: If a DNS record was created directly by a DNS client then, by default, a DHCP server would not be able to make updates on this DNS record as it does not have the permissions to do it.
Using DHCP registration for DNS A and PTR records on behalf of DHCP clients has another disadvantage which is the fact that, having the DHCP AD account as the owner of new DNS records will make these records not available to be updated directly by clients. This is because, in the ACLs of these records, the clients do not have the permission to update their own records.
Updating DNS Resource Records: http://technet.microsoft.com/en-us/library/ff631099(v=ws.10).aspx
DHCP: The DNSupdateproxy group must be secured if Name Protection is enabled on any IPv6 scope: http://technet.microsoft.com/en-us/library/ee941128(v=ws.10).aspx
As allowing Dynamic DNS updates might finish with many stale DNS records that need to be cleaned, enabling DNS aging and scavenging should help on the automatic cleanup of dynamic records.
How DNS aging and scavenging works: http://social.technet.microsoft.com/wiki/contents/articles/21724.how-dns-aging-and-scavenging-works.aspx