SharePoint 2013: Host Named Site Collection (HNSC) Overview
SharePoint 2013 introduced a type of Site Collection called Host Named Site Collection (HNSC) which is suitable for models dependent on DNS host names in multi- tenant environments.
This article draws on several sources including personal experience about HNSC.
In SharePoint 2013, you can either create path-based site collections or host-named site collections.
Host-named site collections enable you to assign a unique DNS name to site collections. For example, you can address them as http://TeamA.domain.com and http://TeamB.domain.com. This enables you to deploy many sites with unique DNS names in the same web application. It also enables hosters to scale an environment to many customers. If you do not use host-named site collections, your SharePoint web application will contain many path-based site collections that share the same host name (DNS name). For example, Team A has a site collection at http://domain.com/sites/teamA, and Team B has a site collection at http://domain.com/sites/teamB.
Host-named versus Path-based site collections
|
Host-named site collections |
Path-based site collections |
Creating sites |
You can use Windows PowerShell to create host-named site collections. You cannot use Central Administration to create host-named site collections. |
You can use Central Administration or Windows PowerShell to create path-based site collections. |
URLs |
Each host-named site collection in a web application is assigned a unique DNS name. You can use zones to assign up to five URLs to host-named sites, including vanity URLs. |
All path-based site collections in a web application share the same host name (DNS name) as the web application. You can extend a web application to implement up to five zones and create different host names for each zone. However, the host name for a zone applies to all site collections within the web application. |
Root site collection and search |
A root site collection is required to crawl content in a web application. A root site collection can be a site collection that users cannot access. |
Typically, a single path-based site collection serves as the root site collection within a web application. You can use managed paths to create additional site collections within the web application. |
URL mapping |
Use Windows PowerShell commands to manage URLs (Set-SPSiteURL, Remove-SPSiteURL, Get-SPSiteURL). |
Use Alternate Access Mappings to manage URLs. |
Self-service site creation |
You need to use a custom solution for self-service site creation with host-named site collections. The Self Service Site Creation feature that is part of the default installation of SharePoint 2013 does not work with host-named site collections. |
When you use the Self Service Site Creation feature that is part of the default installation of SharePoint 2013, you create path-based sites. |
Managed paths |
Managed paths for host-named site collections apply at the farm level and are available for all web applications. You have to use Windows PowerShell to create managed paths for host-named site collections. |
Managed paths for path-based sites apply at the web application level. You can use Central Administration or Windows PowerShell to create managed paths for path-based site collections. |
How to create host-named site collections:
Make sure you open the SharePoint 2013 Management Shell with the required permissions security admin and db_owner on DBs and administrator on the server which you will use.
Then write the following command:
New-SPSite 'http://site.company.com' -HostHeaderWebApplication 'http://<servername>' -Name 'Portal' -Description 'Customer root' -OwnerAlias 'domain\administrator' -language 1033 -Template 'STS#0'
Off-box termination of SSL with host-named site collections
Off-box termination of SSL occurs when a proxy server terminates an SSL request and uses HTTP to forward the request to a web server. To achieve off-box SSL termination with host-named site collections, the device that terminates the SSL connection, such as a reverse proxy server, must be capable of generating a custom HTTP header: Front-End-Https: On.
To Apply off-box termination of SSL with host-named site collections you will need to apply that on the reverse proxy:
Value |
Description |
On |
The reverse proxy server received the end user’s request over an encrypted (SSL or TLS) HTTPS connection. For example, Front-End-Https: On. |
Off |
The reverse proxy server received the end user’s request over an unencrypted HTTP connection. |
HNSC with OWA and SSL
There are cases if you have SSL HNSC that are exposed externally and are accessible through the internet and in this case you would like to force SSL for security reasons.
This is not an issue by itself but if you are having OWA then you need to pay attention to an important note that if you want your https HNSC site to have OWA working then you will need to create it from begging with https like this:
New-SPSite 'https://site.company.com/departments/marketing' -HostHeaderWebApplication 'http://<servername>' -Name 'Marketing' -Description 'Portal' -OwnerAlias 'domain\administrator' -Template 'STS#0'
But if you created from the begging as http like this:
New-SPSite 'http://site.company.com/departments/marketing' -HostHeaderWebApplication 'http://<servername>' -Name 'Portal' -Description 'Portal' -OwnerAlias 'domain\administrator' -Template 'STS#0'
OWA will not work on HNSC when you try to add https URL so you will need to take backup of the existing http HNSC, remove it then create it as https then restore the backup, by that way OWA will work.
Zones:
When you create a new hostname site collection, the default alternate access mappings will still exist but cannot be used. Use Windows PowerShell commands to manage URL mappings for host-named site collections.
Each URL mapping is applied to a single zone. Use one of the following zone names when you map URLs:
- Default
- Intranet
- Internet
- Custom
- Extranet
To display all mappings:
Get-SPSiteUrl -Identity (Get-SPSite 'http://teams.domain.com')
To add mapping to HNSC:
Set-SPSiteUrl (Get-SPSite 'http://teams.domain.com') -Url 'http://teamsites.domain.com' -Zone Intranet
To remove the mapping:
Remove-SPSiteUrL (Get-SPSite 'http://teams.domain.com') -Url 'http://teamsites.domain.com'
Screen Shots for HNSC process creation:
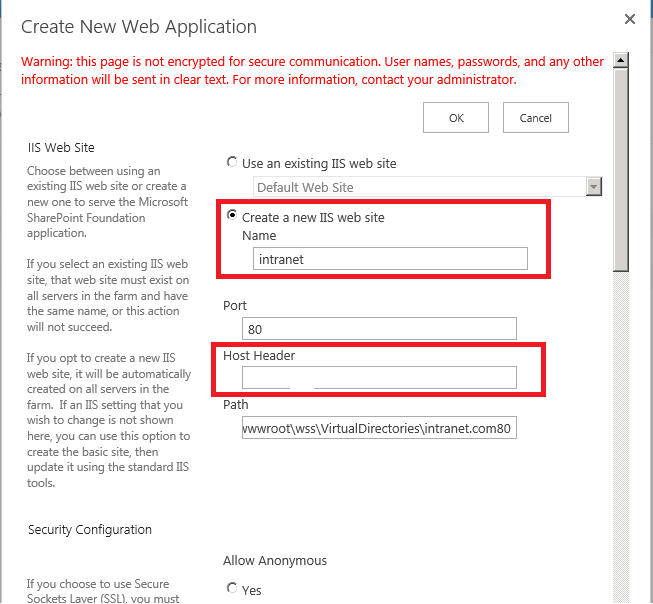
*** 1. Create web app as in the following screenshot and leave the host header empty***
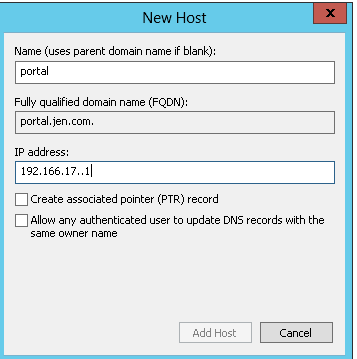
2. Add DNS record pointing to the IP of the server of it is single front end or the VIP if using load balancer
New-SPSite ‘http://portal.jen.com’ -HostHeaderWebApplication ‘http://intranet.com' -Name ‘Portal’ - OwnerAlias ‘domain\administrator’ -Template ‘STS#0′
Notes:
If you are having a web application and created underneath it the HNSC then you will need to add a binding on IIS on all Web Front End servers either do that from IIS console or use those commands:
Import-Module WebAdministration
New-WebBinding -Name 'webapp' -IPAddress '192.168.10.20' -HostHeader 'portal.x.com'
Sleep 60
# remove existing binding
Get-WebBinding -Name 'webapp' -HostHeader 'portal.x.com' | Remove-WebBinding
References: