Bitlocker Drive Encryption In Server 2012/2012R2-Not Completed Need to Do the Alignments
Bitlocker is a drive encryption feature which was introduced in Windows Vista and Windows Server 2008, but Bitlocker is available only with the selected versions of Windows. Using bitlocker a user can prevent unauthorized access to the disk drives. Bitlocker has the following features
- Bitlocker can encrypt entire hard disk or utilized portion of the hard disk.
- Can be combined with EFS (Encrypted File System).
- Bitlocker is fully compatible with TPM which is the hardware device we can use for encryption. Using this feature we can encrypt system drives.
- We can configure Bitlocker options gsing group policy.
- We can manage recovery keys centrally.
In the Windows Server 2012/2012 R2 operating system, Bitlocker is a an on demand feature.
We can also centrally manage Bitlocker encryption using Group Policy as well.
Step by step to configure Bitlocker in Enterprise environment.
Configuring Group policy for Bitlocker
i. Create a group policy (GP name-Bitlockerconfig)
ii. Assign the policy to the domain
iii. Perform the following changes
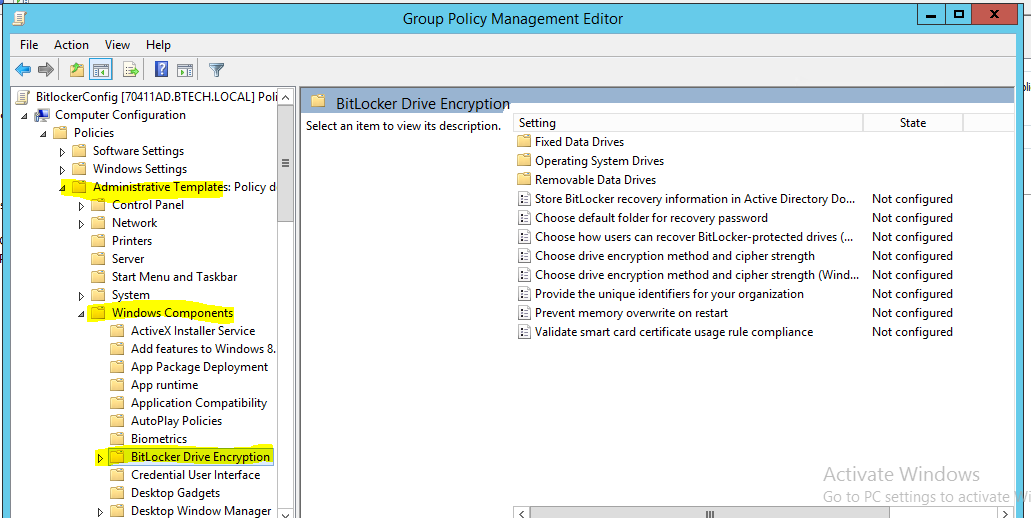
All the Bitlocker related settings are under "Computer configuration>Administrative Templates> Windows Components > Bitlocker Drive Encryption"
With Bitlocker group policy configuration can be configured with Fixed drives, Removable Data drives or Operating system Drives separately. Expanding BitLocker Drive Encryption folder will show all the available options. In this guide we are going to manage bitlocker on fixed drive.
Inside the fixed drive folder there are some group policy settings available. We are going to enable the last policy setting above (Choose how BitLocker-Protected fixed drives can be recovered). Using this setting we can recover the passwords of Bitlocker encrypted fixed drives. Below I saved all the Bitlocker recovery information with AD DS .
Enable Bitlocker in Server 2012 R2(File Server)
i. Open server manager and go to the Manage > Select "Add Roles And Features" and add "BitLocker Drive Encryption" from features list, It will automatically add the "Enhanced Storage" Feature also.
i. Once its complete, we have to restart the server.
Bitlocker encryption on disk drive
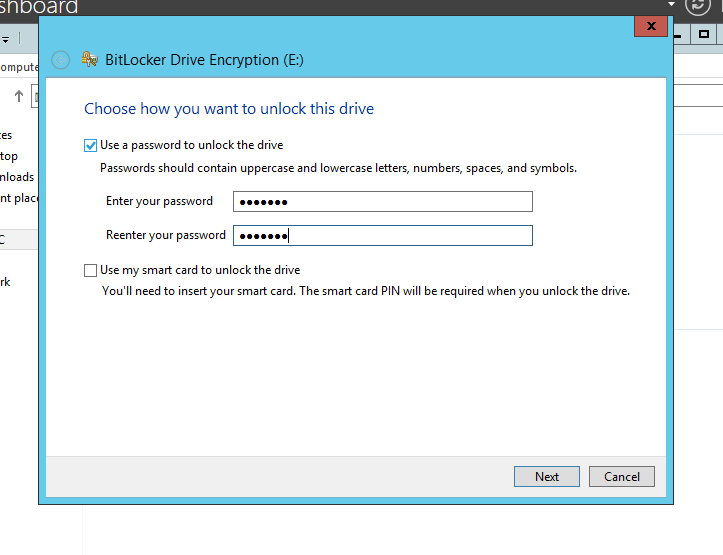
i. Now we can enable the bitlocker on our data drive(E Drive). Just right click on the drive and select "Turn on BitLocker".
ii. Enter password for Bitlocker encryption for this E drive.[
](resources/1234.7.png)
iii. We have three options for keeping this recovery key.
iv. Now we can start the encryption.
Manage Bitlocker
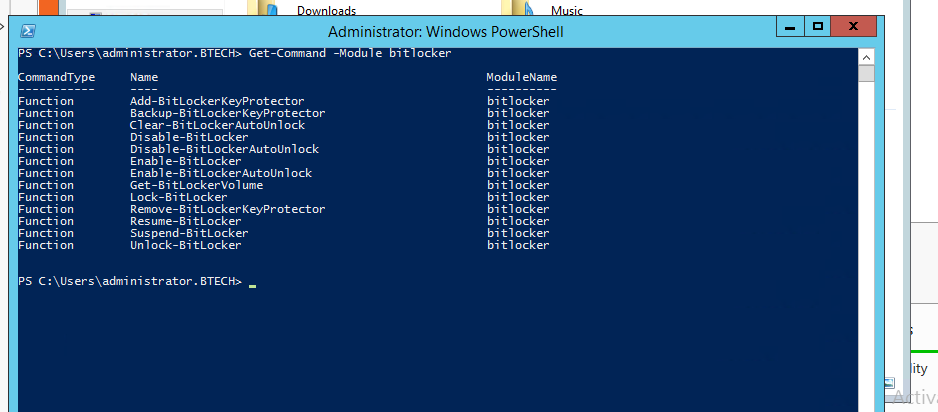
i. The easiest way to manage Bitlocker is to use the PowerShell cmdlets that come with the Bitlocker module. We can view those commands using Get-Command -Module Bitlocker cmdlet.
ii. When we login to our server, it shows E drive as an unlocked drive:
How to lock Bitlocker encrypted drive
i. Open PowerShell > we can use "Lock-Bitlocker -MountPoint "e:" -Forcedismountcmdlet to lock the drive
(Also we can use manage-bde -Lock e: -forcedismount command for the same purposes)
[
ii. After that its locked and we are prompted for a password when we try to open it:
](resources/06834.13.png)
*If we don’t have the password, forgotten password we have to click on more option and think about the recovery key
How to recover the Bitlocker encryption drive, in case of password forgotten or loss scenario
i.We can use saved recovery key in the local drive
*But this is not a good practice, file can be missing at any time
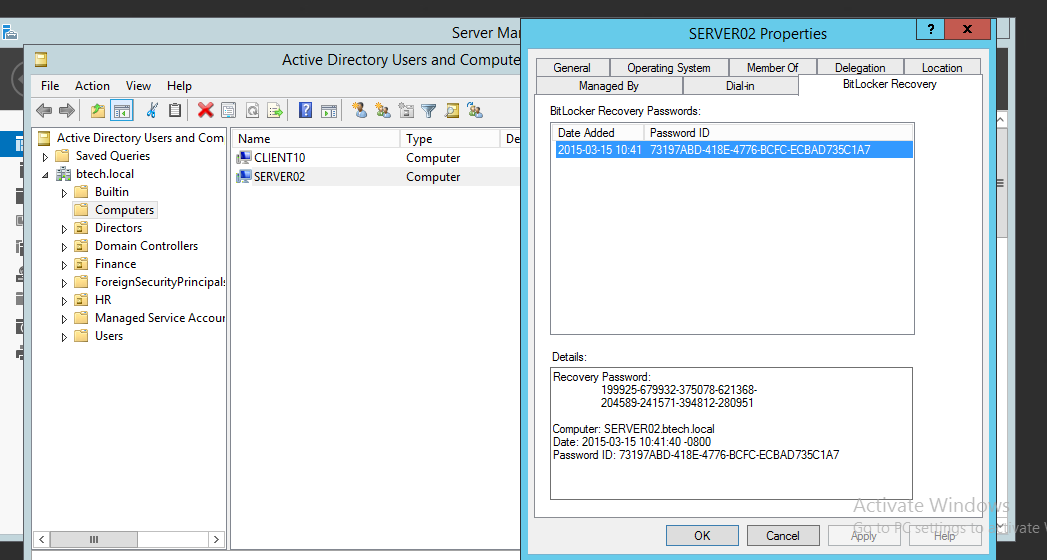
ii.From the Administrators point of view, easiest way is to recover the encryption key from the Active Directory(We have enabled it from Group Policy).To get the recovery key from Active Directory, Open the "Active Directory Users and Computers" > Right click on the computer which we want to recover the Bitlocker recovery key > Select "Bitlocker Recovery" Tab and get the recovery key